Compare commits
No commits in common. "master" and "20240225" have entirely different histories.
1
site.cfg
1
site.cfg
|
|
@ -1,4 +1,3 @@
|
|||
# SPDX-License-Identifier: CC0-1.0
|
||||
TITLE="Libreboot"
|
||||
DOMAIN="https://libreboot.org/"
|
||||
BLOGDIR="news/" # leave as empty string if you want the blog to be the homepage
|
||||
|
|
|
|||
|
|
@ -1,78 +0,0 @@
|
|||
---
|
||||
title: Контакты
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
Купите Libreboot предустановленным
|
||||
==================================
|
||||
|
||||
Если вы хотите, чтобы профессионал установил Libreboot для вас, то Minifree Ltd продает [Libreboot предустановленным](https://minifree.org/) на определенном оборудование, и также предоставляет сервис по [установке Libreboot](https://minifree.org/product/installation-service/) на ваши машины.
|
||||
|
||||
Основатель и ведущий разработчик Libreboot, Лия Роу, владеет и управляет Minifree; продажи обеспечивают финансирование для Libreboot.
|
||||
|
||||
Если вы самостоятельно устанавливаете Libreboot, вы можете получить поддержку:
|
||||
|
||||
Поддержка пользователей
|
||||
=======================
|
||||
|
||||
IRC и Reddit предпочительнее, если вы хотите попросить помощи (IRC рекомендуется). Информация об IRC и Reddit ниже.
|
||||
|
||||
Почтовая рассылка
|
||||
=================
|
||||
|
||||
У Libreboot есть своя почтовая рассылка: <https://lists.sr.ht/~libreboot/libreboot>
|
||||
|
||||
Адрес электронной почты: [~libreboot/libreboot@lists.sr.ht](mailto:~libreboot/libreboot@lists.sr.ht)
|
||||
|
||||
Обсуждение разработки
|
||||
=====================
|
||||
|
||||
Смотрите [страницу по Git](git.md) для того, чтобы узнать, как помогать с разработкой Libreboot.
|
||||
|
||||
На этой странице также содержаться инструкции, как отправлять патчи (с помощью pull request).
|
||||
|
||||
Чат в IRC
|
||||
==========
|
||||
|
||||
IRC - главный метод связи с проектом Libreboot. `#libreboot` на Libera IRC.
|
||||
|
||||
Чат в вебе:
|
||||
<https://web.libera.chat/#libreboot>
|
||||
|
||||
Libera - самая большая сеть IRC, используемая для свободных проектов. Узнайте больше здесь: <https://libera.chat/>
|
||||
|
||||
Если вы хотите подключиться к IRC через ваш любимый клиент (например, weechat или irssi):
|
||||
|
||||
* Сервер: `irc.libera.chat`
|
||||
* Канал: `#libreboot`
|
||||
* Порт (TLS): `6697`
|
||||
* Порт (не TLS): `6667`
|
||||
|
||||
Мы рекомендуем использовать порт `6697` со включенным TLS шифрованием.
|
||||
|
||||
Мы также рекомендуем использовать SASL для аутентификации. Эти страницы на сайте Libera IRC расскажут как это сделать:
|
||||
|
||||
* WeeChat SASL guide: <https://libera.chat/guides/weechat>
|
||||
* Irssi SASL guide: <https://libera.chat/guides/irssi>
|
||||
* HexChat SASL guide: <https://libera.chat/guides/hexchat>
|
||||
|
||||
В общем, вы должны проверить документацию вашего клиента для IRC.
|
||||
|
||||
Социальные сети
|
||||
===============
|
||||
|
||||
Mastodon
|
||||
--------
|
||||
|
||||
Основатель и велущий разработчик, Лия Роу, есть на Mastodon:
|
||||
|
||||
* <https://mas.to/@libreleah>
|
||||
|
||||
Связаться с Лией также можно и по этому адресу электронной почты:
|
||||
[leah@libreboot.org](mailto:leah@libreboot.org)
|
||||
|
||||
Reddit
|
||||
------
|
||||
|
||||
Чаще всего используется для поддержки пользователей, а также для новостей и анонсов:
|
||||
<https://www.reddit.com/r/libreboot/>
|
||||
100
site/contrib.md
100
site/contrib.md
|
|
@ -196,13 +196,33 @@ systems.
|
|||
Joshua Gay
|
||||
----------
|
||||
|
||||
Joshua was in a position during 2014-2016 to help promote Libreboot in the
|
||||
media, in his capacity working for the employer he worked for at the time;
|
||||
I credit him specifically. Joshua was one of Libreboot's earliest supporters.
|
||||
Joshua is former FSF staff.
|
||||
|
||||
He made sure everyone knew what I was doing, and he taught me a *lot* about
|
||||
licensing; many of Libreboot's practises today are still based on his lessons,
|
||||
such as the pitfalls of GPL compliance and how to really audit everything.
|
||||
Joshua helped with the early founding of the Libreboot project, in his capacity
|
||||
(at that time) as the FSF's licensing and compliance manager. It was his job to
|
||||
review products sent into to the FSF for review; the FSF has a certification
|
||||
program called *Respects Your Freedom* (RYF) where the FSF will promote your
|
||||
company's products if it comes with all Free Software.
|
||||
|
||||
I, Leah Rowe, was initially just selling ThinkPad X60 laptops with regular
|
||||
coreboot on them, and this included CPU microcode updates. At the time, I didn't
|
||||
think much of that. Joshua contacted me, in his capacity at the FSF, and asked
|
||||
if I would be interested in the FSF's RYF program; I was very surprised that the
|
||||
FSF would take me seriously, and I said yes. This is what started the early
|
||||
work on Libreboot. Joshua showed me all the problems my products had, and from
|
||||
that, the solution was clear:
|
||||
|
||||
Joshua used his media connections at the FSF to heavily promote my work, and
|
||||
on December 13th, 2013, the Libreboot project was born (but not called that).
|
||||
Joshua made sure that everyone knew what I was doing!
|
||||
|
||||
A few months later, the name *Libreboot* was coined, and the domain name
|
||||
*libreboot.org* was registered. At that point, the Libreboot project (in early
|
||||
2014) was officially born. Once again, Joshua provided every bit of help he
|
||||
could, heavily promoting the project and he even wrote this article on the FSF
|
||||
website, announcing it:
|
||||
|
||||
<https://web.archive.org/web/20171222063358/https://www.fsf.org/blogs/licensing/replace-your-proprietary-bios-with-libreboot>
|
||||
|
||||
Klemens Nanni
|
||||
-------------
|
||||
|
|
@ -213,22 +233,60 @@ libreboot, and several tweaks to the build system.
|
|||
Lisa Marie Maginnis
|
||||
-------------------
|
||||
|
||||
Lisa was one of Libreboot's early contributors to Libreboot. She personally
|
||||
helped me set up a lot of the early infrastructure, including things like IRC,
|
||||
mailing list and so on. She provided a lot of technical guidance, while working
|
||||
in a sysadmin job for a certain free software organisation; she was both a
|
||||
mentor and a friend.
|
||||
Lisa is a former sysadmin at the Free Software Foundation. In the early days of
|
||||
the project, she provided Leah with a lot of technical advice. She initially
|
||||
created Libreboot IRC channel, when Leah did not know how to
|
||||
use IRC, and also handed +F founder status to Leah for the channel. As an FSF
|
||||
sysadmin, it was Lisa's job to maintain a lot of the infrastructure used by
|
||||
Libreboot; at the time, mailing lists on the Savannah website were used by
|
||||
the Libreboot project. When Paul Kocialkowski was a member of the project in
|
||||
2016, she helped him get help from the FSF; he was the leader of the Replicant
|
||||
project at the time, which had funding from the FSF, and the FSF authorized him
|
||||
to use some of that funding for his work on Libreboot, thanks to Lisa's
|
||||
encouragement while she worked at the FSF.
|
||||
|
||||
She got me in touch with a lot of people, and at one point was instrumental in
|
||||
helping Paul Kocialkowski secure funding to work on the Veyron Speedy boards
|
||||
in Libreboot, e.g. ASUS Chromebook C201PA - at the time, this was using
|
||||
Google's own Depthcharge payload, which you can find in 2016 Libreboot
|
||||
releases.
|
||||
Lisa also stepped in when Leah Rowe missed her LibrePlanet 2016 talk. Leah was
|
||||
scheduled to do a talk about Libreboot, but didn't show up in time. Lisa, along
|
||||
with Patrick McDermott (former Libreboot developer, who was present at that
|
||||
conference) did the talk in Leah's place. The talk was never recorded, but the
|
||||
Free Software Foundation has these photos of that talk on their LibrePlanet
|
||||
website (the woman with the blue hair is Lisa, and the long-haired dude with the
|
||||
moustache is Patrick):
|
||||
|
||||
<http://web.archive.org/web/20170319043913/https://media.libreplanet.org/u/libreplanet/m/session-02-c-mws-png-libreplanet-2016-sessions/>
|
||||
|
||||
<http://web.archive.org/web/20170319043915/https://media.libreplanet.org/u/libreplanet/m/session-02-c-wide-png-libreplanet-2016-sessions/>
|
||||
|
||||
Fun fact: Patrick is also the lead developer of ProteanOS, an FSF-endorsed
|
||||
embedded OS project: <http://proteanos.com/> (uses BusyBox and Linux-libre)
|
||||
|
||||
Leah Rowe ran *2* LibrePlanet workshops; one in 2015 and another in 2016, while
|
||||
visiting Boston, MA, USA on both occasions to attend these conferences. These
|
||||
workshops were for Libreboot installations. People came to both workshops, to
|
||||
have Libreboot installed onto their computers. As FSF sysadmin, at that time,
|
||||
Lisa provided all of the infrastructure and equipment used at those workshops.
|
||||
Without her help, those workshops would have not been possible.
|
||||
|
||||
When the ASUS KGPE-D16 mainboard (high-end server board) was ported to Libreboot,
|
||||
Leah, working with Timothy Pearson (the one who ported it), shared patches back
|
||||
and forth with Lisa around mid 2016, mostly raminit patches, to get the board
|
||||
running at the FSF offices. This work ultimately lead to a most wonderful
|
||||
achievement:
|
||||
|
||||
The FSF and GNU websites now run on
|
||||
Librebooted ASUS KGPE-D16 based servers, on a fully free GNU+Linux distro. This
|
||||
means that the FSF now has full software freedom for their hosting infrastructure.
|
||||
|
||||
The FSF also provides access to this infrastructure for many other projects
|
||||
(besides GNU projects).
|
||||
|
||||
Lisa was a strong supporter of Libreboot in the very early days of the project,
|
||||
and her contributions were invaluable. I, Leah Rowe, owe her a debt of gratitude.
|
||||
|
||||
Lorenzo Aloe
|
||||
------------
|
||||
|
||||
Provided hardware testing for the [Dell OptiPlex 9020](docs/install/dell9020.md),
|
||||
Provided hardware testing for the [Dell OptiPlex 9020](docs/hardware/dell9020.md),
|
||||
also provided testing for proxmox with GPU passthrough on Dell Precision T1650,
|
||||
confirming near-native performance; with this, you can boot operating systems
|
||||
virtually natively, performance-wise, on a Libreboot system in cases where
|
||||
|
|
@ -245,7 +303,7 @@ Nicholas Chin
|
|||
-------------
|
||||
|
||||
[Ported Dell Latitude E6400 to Libreboot](news/e6400.md)
|
||||
and also [Dell Latitude E6430](docs/install/latitude.md) - author of
|
||||
and also [Dell Latitude E6430](hardware/e6430.md) - author of
|
||||
the `dell-flash-unlock` (formerly `e6400-flash-unlock`) utility, which
|
||||
can unlock the flash on these boards, allowing internal flashing of
|
||||
Libreboot directly from host OS running under the original Dell firmware.
|
||||
|
|
@ -258,6 +316,10 @@ relating to the [Intel Management Engine](../faq.md#intelme), in addition
|
|||
to making several improvements to the build system in libreboot. **Former
|
||||
libreboot project maintainer.**
|
||||
|
||||
In 2016, Leah Rowe ran a Libreboot installation workshop at the FSF's
|
||||
LibrePlanet conference. Working alongside Leah, Patrick helped run the workshop
|
||||
and assisted with installing Libreboot onto people's machines.
|
||||
|
||||
Paul Kocialkowski
|
||||
-----------------
|
||||
|
||||
|
|
@ -306,7 +368,7 @@ Riku Viitanen
|
|||
Added support for HP Elite 8200 SFF desktop PC to Libreboot. You can read
|
||||
about this in the hardware page:
|
||||
|
||||
[HP Elite 8200 SFF](docs/install/hp8200sff.md)
|
||||
[HP Elite 8200 SFF](docs/hardware/hp8200sff.md)
|
||||
|
||||
Steve Shenton
|
||||
-------------
|
||||
|
|
|
|||
|
|
@ -0,0 +1,467 @@
|
|||
---
|
||||
title: Учасники проекту
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
У цьому списку не обов'язково вказується, хто зараз працює над проектом,
|
||||
але в ньому вказано людей, які зробили значний внесок у проект.
|
||||
|
||||
Якщо ми забули вас тут згадати, повідомте нам, і ми вас додамо. (або якщо
|
||||
ви не хочете, щоб вас згадували, повідомте нас, і ми видалимо ваш
|
||||
запис)
|
||||
|
||||
Інформацію про те, хто працює над libreboot і як працює проект, можна
|
||||
знайти на цій сторінці: [who.md](who.md)
|
||||
|
||||
Ви можете дізнатися історію проекту libreboot, просто прочитавши цю сторінку.
|
||||
Тут докладно розповідається про всі основні внески в проект і
|
||||
загалом про те, як створювався проект (і хто допоміг його створити).
|
||||
|
||||
Лія Роу
|
||||
---------
|
||||
|
||||
**Засновник проекту Libreboot, а зараз провідний розробник** Лія
|
||||
працює над усіма аспектами libreboot, такими як:
|
||||
|
||||
* Загальне керівництво. Лія обробляє всі зовнішні внески до libreboot,
|
||||
переглядає пул реквести, має справу із звітами про помилки, делегує завдання, коли це необхідно
|
||||
або бажано. Лія контролює серверну інфраструктуру libreboot.org, розміщену
|
||||
в її лабораторії.
|
||||
* Лія має останнє слово щодо всіх рішень, беручи внесок через обговорення з
|
||||
представниками громадськості, переважно на IRC. Лія контролює випуски libreboot
|
||||
і загалом підтримує проект. Без Лії не було би Libreboot!
|
||||
* Система збірки (lbmk, скорочення від libreboot Make). Це автоматизована
|
||||
система збирання, яка лежить в серці libreboot; він завантажує, патчить, налаштовує
|
||||
та компілює відповідні компоненти, такі як coreboot, GRUB, і генерує образи ROM
|
||||
libreboot, які ви можете знайти в архівах випусків.
|
||||
* Апстрім робота над coreboot, коли необхідно (та іншими проектами, які libreboot
|
||||
використовує). Це також означає роботу з людьми поза межами проекту libreboot,
|
||||
щоб об'єднати виправлення (між іншим) в апстрім проектах,
|
||||
які libreboot використовує
|
||||
* Надання підтримки користувачів на IRC
|
||||
|
||||
Калеб Ла Гранж
|
||||
---------------
|
||||
|
||||
**Вторинний розробник, номер два для Лії.** Калеб - розробник libreboot на повний робочий день
|
||||
з вузьким фокусом. Калеб зосереджується на кількох напрямках розвитку:
|
||||
|
||||
* Система побудови. Калеб відповідає за вдосконалення та виправлення системи побудови libreboot Make.
|
||||
Зокрема, управління бінарними блобами, автоматизація та відтворюваність.
|
||||
* Апаратна модифікація. Калеб має пристрасть до переробки апаратного забезпечення; паяння,
|
||||
розпаювання, та тестування libreboot на отриманому обладнанні.
|
||||
* Перенесення плати. Все, що підтримується в Coreboot, можна перенести на libreboot, Калеб
|
||||
перевірить і перенесе будь-яку плату, до якої зможе потрапити. Крім того, будь-хто може
|
||||
зв'язатись з Калебом, щоб створити образи libreboot для тестування на своїй платі.
|
||||
* Документація. Калеб активно веде документацію щодо зазначених вище сфер
|
||||
інтересу. Додатково, Калеб відповідає за посібники з розбирання з власними
|
||||
малюнками та діаграмами для кількох плат.
|
||||
* Підтримка користувачів. Калеб активний в irc і готовий допомогти будь-якому користувачеві, який зацікавлений в
|
||||
використанні libreboot або потребує допомоги.
|
||||
* Цілі проекту. Калеб співпрацює з Лією над визначенням цілей проекту.
|
||||
Лія має останнє слово в кожному рішенні.
|
||||
|
||||
Зовнішні проекти
|
||||
================
|
||||
|
||||
Проект Coreboot
|
||||
----------------
|
||||
|
||||
Без coreboot проект libreboot був би просто неможливий.
|
||||
|
||||
Людей і компаній, які працюють над coreboot, багато, і вони роблять
|
||||
проект libreboot таким, яким він є. Проект libreboot активно використовує coreboot
|
||||
для ініціалізації обладнання.
|
||||
|
||||
GRUB
|
||||
--------
|
||||
|
||||
GRUB - це завантажувач, який використовується libreboot. Само собою зрозуміло, що
|
||||
розробники GRUB стимулюють libreboot своєю роботою.
|
||||
|
||||
SeaBIOS
|
||||
-------
|
||||
|
||||
Прошивка libreboot надає SeaBIOS як опцію корисного навантаження. SeaBIOS забезпечує
|
||||
застарілу реалізацію BIOS x86.
|
||||
|
||||
U-Boot
|
||||
------
|
||||
|
||||
Libreboot використовує U-Boot як корисне навантаження coreboot на ноутбуках
|
||||
ARM Chromebook з підтримкою coreboot.
|
||||
|
||||
Внески в алфавітному порядку
|
||||
============================
|
||||
|
||||
Алісса Розенцвейг
|
||||
-----------------
|
||||
|
||||
Переключила веб-сайт на використання розмітки замість рукописного HTML та користувацького
|
||||
PHP. **Колишній супроводжувач проекту libreboot (системний адміністратор libreboot.org).**
|
||||
|
||||
Алісса написала оригінальний генератор статичних сайтів (скрипти `sh`, що перетворюють
|
||||
markdown в html, через pandoc) для libreboot.org. Цей генератор статичних сайтів
|
||||
був значно змінений і відгалужений Лією Роу у формальний проект:
|
||||
|
||||
<https://untitled.vimuser.org/> (untitled - це робота Лії, а не Алісси, але вона базується на
|
||||
оригінальній роботі Аліси над генератором статичних сайтів, який раніше використовував Libreboot;
|
||||
веб-сайт Libreboot тепер створено за допомогою Untitled)
|
||||
|
||||
Альпер Небі Ясак
|
||||
----------------
|
||||
|
||||
Надав інтеграцію системи збірки та документацію для використання
|
||||
U-Boot в якості корисного навантаження, та початкові порти Libreboot деяких ARM Chromebook
|
||||
виходячи з того.
|
||||
|
||||
Альпер також займається розробкою на U-Boot, напр. продовжив майже завершений
|
||||
порт плати `gru-kevin` і об'єднав його з апстрімом.
|
||||
|
||||
Артур Хейманс
|
||||
--------------
|
||||
|
||||
Об'єднав патч із coreboot у libreboot, дозволяючи режимам живлення C3 та C4
|
||||
правильно працювати на ноутбуках GM45. Це була давня проблема до внеску
|
||||
Артура. Артур також виправив розмір відеопам'яті на i945 на системах
|
||||
GM45, що дозволило максимально розподілити VRAM для вбудованих графічних процесорів
|
||||
у цих системах, ще одна давня проблема в libreboot.
|
||||
|
||||
Артур також працював над системою збірки Libreboot, коли він був учасником
|
||||
проекту. Він досі працює над coreboot, і Libreboot отримує велику
|
||||
користь від його роботи. Його внесок у проект coreboot і Libreboot
|
||||
неоціненний.
|
||||
|
||||
Володимир Сербіненко
|
||||
-------------------
|
||||
|
||||
Перенес багато thinkpad, які підтримуються в libreboot, на coreboot, а
|
||||
також зробив багато виправлень у coreboot, які принесли користь проекту libreboot.
|
||||
|
||||
Володимир написав багато вихідного коду ініціалізації відео, який використовується різними
|
||||
платформами Intel у Libreboot, під час прошивки (зараз переписаний
|
||||
іншими в Ada, для libgfxinit в coreboot, але спочатку він був написаний на
|
||||
C і включений безпосередньо в coreboot; libgfxinit є субмодуль третьої сторони).
|
||||
|
||||
Демієн Замміт
|
||||
-------------
|
||||
|
||||
Підтримує порт coreboot Gigabyte GA-G41M-ES2L, інтегрований у
|
||||
libreboot. Також працює над іншим апаратним забезпеченням на користь
|
||||
проекту libreboot.
|
||||
|
||||
Демієн не працював безпосередньо над самим Libreboot, але він багато працював з
|
||||
Лією Роу, інтегруючи патчі та нові порти плати в Libreboot на основі
|
||||
попередньої роботи Демієна над coreboot.
|
||||
|
||||
Денис Каріклі
|
||||
-------------
|
||||
|
||||
На основі роботи, виконаної Пітером Стюджем, Володимиром Сербіненко та іншими
|
||||
в проекті coreboot, вдалось налагодити нативну ініціалізацію графіки для роботи
|
||||
на ThinkPad X60, що дозволяє підтримувати її в libreboot. Денис дав
|
||||
багато порад і допоміг створити проект libreboot.
|
||||
|
||||
Денис був наставником Лії Роу в ранні дні, коли вона заснувала проект
|
||||
Libreboot. Багато прийнятих рішень, особливо щодо системи збірки
|
||||
Libreboot (lbmk), були натхненні розмовами з Денисом.
|
||||
|
||||
Денис навчив Лію про регістри, які використовуються графічним процесором Intel для керування підсвічуванням.
|
||||
В ранні дні, ноутбуки ThinkPad X60 та T60 в Libreboot не мали працюючого
|
||||
контроля підсвічуванням, тому яскравість завжди була 100%. За допомогою Дениса,
|
||||
Лія змогла налаштувати керування підсвічуванням шляхом зворотньої розробки
|
||||
правильних значень для запису в ці регістри. На основі цього в coreboot
|
||||
було написано просте виправлення; однак виправлення перезаписувало безпосередньо регістр
|
||||
і не працювало з елементами керування яскравістю на основі ACPI. Інші в coreboot
|
||||
пізніше вдосконалили його, змусивши елементи керування підсвічуванням на основі ACPI працювати належним чином, на основі цієї
|
||||
попередньої роботи.
|
||||
|
||||
Джерун Квінт
|
||||
------------
|
||||
|
||||
Додав кілька виправлень до документації libreboot, пов'язаної зі
|
||||
встановленням Arch з повним дисковим шифруванням у системах libreboot.
|
||||
|
||||
Джошуа Гей
|
||||
----------
|
||||
|
||||
Джошуа колишній співробітник FSF.
|
||||
|
||||
Джошуа допоміг із раннім заснуванням проекту Libreboot, будучи
|
||||
(на той час) менеджером з ліцензування та відповідності FSF. Його роботою було
|
||||
переглядати продукти, надіслані до FSF для перевірки; FSF має програму
|
||||
сертифікації, під назвою *Поважає Вашу Свободу* (Respects Your Freedom), за якою FSF рекламуватиме
|
||||
продукти вашої компанії, якщо вони постачаються з усім вільним програмним
|
||||
забезпеченням.
|
||||
|
||||
Я, Лія Роу, спочатку просто продавала ноутбуки ThinkPad X60 із звичайним
|
||||
coreboot, і це включало оновлення мікрокоду ЦП. У той час
|
||||
я не дуже про це думала. Джошуа зв'язався зі мною, в своїх повноваженнях FSF, і спитав,
|
||||
чи зацікавить мене програма RYF FSF; Я була дуже здивована, що FSF
|
||||
сприйме мене серйозно, і я сказала так. Саме з цього почалася рання робота
|
||||
над Libreboot. Джошуа показав мені всі проблеми з моїми продуктами, і з
|
||||
цього, рішення було очевидним:
|
||||
|
||||
Необхідно, щоб існував проект із повністю вільною версією coreboot без будь-яких
|
||||
бінарних блобів. У той час (і це актуально й сьогодні) coreboot не був
|
||||
повністю вільним програмним забезпеченням і за замовчуванням постачався з двійковими блобами. Зокрема,
|
||||
оновлення мікрокоду ЦП включено за замовчуванням на всіх машинах x86. Працюючи
|
||||
з Джошуа, я створила повністю вільну версію coreboot.
|
||||
Спочатку він не називався Libreboot, і робота була призначена виключно для моєї
|
||||
компанії (на той час вона називалася Gluglug), яку просувала FSF.
|
||||
|
||||
Джошуа використовував свої медійні зв'язки в FSF, щоб активно рекламувати мою роботу, і
|
||||
13 грудня 2013 року народився проект Libreboot (але не названий так).
|
||||
Джошуа переконався, щоб всі знали, що я роблю!
|
||||
|
||||
Через кілька місяців було створено назву *Libreboot* і зареєстровано доменне ім'я
|
||||
*libreboot.org*. У цей момент офіційно народився проект Libreboot (на початку
|
||||
2014 року). Знову Джошуа надав всю можливу допомогу,
|
||||
активно просуваючи проект, і навіть написав цю статтю на веб-сайті FSF
|
||||
оголосивши про це:
|
||||
|
||||
<https://web.archive.org/web/20171222063358/https://www.fsf.org/blogs/licensing/replace-your-proprietary-bios-with-libreboot>
|
||||
|
||||
Ендрю Роббінс
|
||||
--------------
|
||||
|
||||
Працював над великими частинами старої системи збірки Libreboot і пов'язаною документацією.
|
||||
Ендрю приєднався до проекту Libreboot як штатний розробник у червні 2017,
|
||||
до моменту свого відходу в березні 2021 року.
|
||||
|
||||
Я, Лія Роу, дуже вдячна Ендрю Роббінсу за його численні внески
|
||||
протягом багатьох років.
|
||||
|
||||
Клеменс Нанні
|
||||
-------------
|
||||
|
||||
Внесено багато виправлень і покращень у конфігурацію GRUB, яка використовується в
|
||||
libreboot, а також кілька змін у системі збірки.
|
||||
|
||||
Ліза Марі Магінніс
|
||||
-------------------
|
||||
|
||||
Ліза - колишній системний адміністратор Free Software Foundation. На перших днях
|
||||
проекту вона давала Лії багато технічних порад. Спочатку вона створила
|
||||
IRC-канал Libreboot, коли Лія не знала, як користуватися
|
||||
IRC, а також передала +F статус засновника для каналу. Як системний
|
||||
адміністратор FSF, роботою Лізи було підтримувати велику частину інфраструктури,
|
||||
яку використовує Libreboot; на той час списки розсилки на веб-сайті Savannah
|
||||
використовувалися проектом Libreboot. Коли Пол Коціалковскі був
|
||||
учасником проекту в 2016 році, вона допомогла йому отримати допомогу від FSF; на той час він був
|
||||
керівником проекту Replicant, який фінансував FSF, і FSF дозволив
|
||||
йому використати частину цього фінансування для його роботи над Libreboot, завдяки Лізи
|
||||
підтримці, коли вона працювала у FSF.
|
||||
|
||||
Ліза також втрутилася, коли Лія Роу пропустила виступ на LibrePlanet 2016. Лія мала
|
||||
виступити з доповіддю про Libreboot, але не з'явилася вчасно. Ліза разом
|
||||
із Патріком Макдермоттом (колишнім розробником Libreboot, який був присутній
|
||||
на тій конференції) виступили замість Лії. Розмова ніколи не була записана, але
|
||||
Фонд вільного програмного забезпечення має ці фотографії цієї розмови на веб-сайті LibrePlanet
|
||||
(жінка з блакитним волоссям - Ліза, а довговолосий хлопець із вусами -
|
||||
Патрік):
|
||||
|
||||
<http://web.archive.org/web/20170319043913/https://media.libreplanet.org/u/libreplanet/m/session-02-c-mws-png-libreplanet-2016-sessions/>
|
||||
|
||||
<http://web.archive.org/web/20170319043915/https://media.libreplanet.org/u/libreplanet/m/session-02-c-wide-png-libreplanet-2016-sessions/>
|
||||
|
||||
Цікавий факт: Патрік також є провідним розробником ProteanOS, проекту вбудованої
|
||||
ОС, схваленого FSF: <http://proteanos.com/> (використовує BusyBox і Linux-libre)
|
||||
|
||||
Лія Роу провела *2* семінари LibrePlanet; один у 2015 році та інший у 2016 році,
|
||||
відвідуючи Бостон, Массачусетс, США в обох випадках для участі в цих конференціях. Ці
|
||||
семінари стосувалися встановлення Libreboot. Люди приходили на обидва семінари, щоб
|
||||
встановити Libreboot на свої комп'ютери. Як системний адміністратор FSF, на той час,
|
||||
Ліза забезпечила всю інфраструктуру та обладнання, яке використовувалося на цих семінарах.
|
||||
Без її допомоги ці майстер-класи були б неможливими.
|
||||
|
||||
Коли материнська плата ASUS KGPE-D16 (серверна плата високого класу) була перенесена на Libreboot,
|
||||
Лія, працюючи з Тімоті Пірсоном (той, хто її переніс),
|
||||
приблизно в середині 2016 року поділилася з Лізою виправленнями, в основному виправленнями raminit, щоб отримати плату, яка працює в офісах FSF. Ця робота
|
||||
зрештою призвела до чудового досягнення:
|
||||
|
||||
Веб-сайти FSF і GNU тепер працюють на, з встановленим Libreboot,
|
||||
заснованих на ASUS KGPE-D16 серверах, на повністю вільному GNU+Linux дистрибутиві. Це
|
||||
означає, що FSF тепер має повну свободу програмного забезпечення для своєї
|
||||
інфраструктури хостингу.
|
||||
|
||||
FSF також надає доступ до цієї інфраструктури для багатьох інших проектів
|
||||
(крім проектів GNU).
|
||||
|
||||
Ліза була сильною прихильницею Libreboot на перших днях проекту,
|
||||
і її внесок був неоціненним. Я, Лія Роу, у боргу перед нею.
|
||||
|
||||
Lorenzo Aloe
|
||||
------------
|
||||
|
||||
Provided hardware testing for the [Dell OptiPlex 9020](docs/hardware/dell9020.md),
|
||||
also provided testing for proxmox with GPU passthrough on Dell Precision T1650,
|
||||
confirming near-native performance; with this, you can boot operating systems
|
||||
virtually natively, performance-wise, on a Libreboot system in cases where
|
||||
that OS is not natively supported.
|
||||
|
||||
All round good guy, an honest and loyal fan.
|
||||
|
||||
Маркус Мьоллер
|
||||
--------------
|
||||
|
||||
Зробив логотип libreboot.
|
||||
|
||||
Nicholas Chin
|
||||
-------------
|
||||
|
||||
[Ported Dell Latitude E6400 to Libreboot](news/e6400.md).
|
||||
|
||||
Патрік "П. Дж." Макдермотт
|
||||
---------------------------
|
||||
|
||||
Патрік також провів багато досліджень і написав розділ поширених запитань libreboot,
|
||||
пов'язаний із [Intel Management Engine](../faq.md#intelme), а також зробив кілька покращень у
|
||||
системі збірки libreboot. **Колишній супроводжувач проекту
|
||||
libreboot.**
|
||||
|
||||
У 2016 році Лія Роу провела семінар зі встановлення Libreboot на конференції FSF
|
||||
LibrePlanet. Працюючи разом з Лією, Патрік допомагав вести семінар
|
||||
та допомагав установлювати Libreboot на комп'ютери людей.
|
||||
|
||||
Пітер Стюдж
|
||||
-----------
|
||||
|
||||
Допоміг написати [розділ поширених запитань про DMA](../faq.md#hddssd-firmware), та надав
|
||||
загальні поради на перших днях проекту. У той час Пітер був розробником coreboot
|
||||
і головним розробником проекту *libusb* (який flashrom
|
||||
активно використовує).
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024.
|
||||
|
||||
Пітер також написав утиліту *bucts*, яка використовується для встановлення біта Top Swap
|
||||
(TS) для керування резервним копіюванням (BUC) на ноутбуках i945, таких як ThinkPad X60/T60, яка є корисною для
|
||||
обхідного шляху для прошивки Libreboot без використання зовнішнього обладнання; на цій машині,
|
||||
з Lenovo BIOS, можна перепрошити все, крім головного завантажувального
|
||||
блоку, але платформи Intel мають 2 завантажувальні блоки, і ви вказуєте, який із них
|
||||
використовувати, встановленням біта TS. Потім ви завантажуєтеся лише з одним прошитим завантажувальним блоком
|
||||
(завантажувальним блоком проекту coreboot на цій машині), а потім скидаєте
|
||||
bucts перед повторною прошивкою ROM, щоб прошити основний завантажувальний блок. Libreboot
|
||||
розміщує копію його роботи, оскільки його веб-сайт, на якому розміщено bucts,
|
||||
більше не відповідає.
|
||||
|
||||
Пол Коціалковський
|
||||
-----------------
|
||||
|
||||
Переніс ноутбуки Chromebook на основі ARM (Rockchip RK3288 SoC) до
|
||||
libreboot. Також один із головних розробників [Replicant](http://www.replicant.us/).
|
||||
|
||||
Пол Менцель
|
||||
-----------
|
||||
|
||||
Дослідив та виправив помилку в coreboot на ThinkPad X60/T60, яку виявляло
|
||||
ядро Linux 3.12 і новіших версій, через яку прискорення 3D не
|
||||
працювало, а відео загалом ставало нестабільним. Проблема полягала в тому, що
|
||||
coreboot під час ініціалізації відеочіпсета Intel, відображав *GTT Stolen Memory* в
|
||||
не тому місці, оскільки код базувався на коді ядра, а в ядрі Linux
|
||||
була така сама помилка. Коли Linux це виправив, він виявив ту саму помилку в coreboot.
|
||||
|
||||
Пол працював над цим із Libreboot,
|
||||
періодично надсилаючи патчі для тестування, доки помилку не було виправлено
|
||||
в coreboot, а потім допоміг ій інтегрувати виправлення в libreboot.
|
||||
|
||||
Riku Viitanen
|
||||
-------------
|
||||
|
||||
Added support for HP Elite 8200 SFF desktop PC to Libreboot. You can read
|
||||
about this in the hardware page:
|
||||
|
||||
[HP Elite 8200 SFF](docs/hardware/hp8200sff.md)
|
||||
|
||||
Стів Шентон
|
||||
-------------
|
||||
|
||||
Стів виконав першу роботу зі зворотньої розробки Intel Flash Descriptor, який використовується
|
||||
на машинах ICH9M, таких як ThinkPad X200. Він створив структуру C, що визначає (використовуючи
|
||||
бітові поля в C) цю область дескриптора. За допомогою деяких хитрих трюків він зміг
|
||||
виявити існування біта в дескрипторі для *вимкнення* Intel ME
|
||||
(management engine) на цих платформах.
|
||||
|
||||
Його початкове підтвердження концепції визначило лише дескриптор, і зробило би це:
|
||||
|
||||
* Читання дескриптора за замовчуванням і регіонів GbE з ROM Lenovo X200 (прошивка
|
||||
за замовчуванням, не coreboot)
|
||||
* Вимкнення ME, встановивши 2 біти в дескрипторі
|
||||
* Вимкнення регіона ME
|
||||
* Переміщення дескриптора+GbE (загалом 12КБ) поруч
|
||||
* Виділення решти флеш-пам'яті для регіону BIOS
|
||||
* На основі цього створено 12КБ регіон дескриптор+область GBE для вставки
|
||||
в образ ROM coreboot.
|
||||
|
||||
У перші дні, до того, як Libreboot підтримував платформи GM45+ICH9M, такі як
|
||||
ThinkPad X200/T400, ви могли використовувати ці машини, але щоб уникнути
|
||||
Intel ME, вам доводилося виконувати прошивку без області дескриптора. У ті часи це працювало нормально,
|
||||
тому що ME обробляв лише TPM та AMT на цих машинах, і система
|
||||
працювала нормально, але Intel Flash Descriptor також обробляє область Intel GbE NVM
|
||||
у флеш-пам'яті, яка використовується для інтерфейсу Intel Gigabit Ethernet.
|
||||
|
||||
Отже, ви або мали Intel ME, або не підтримували ethernet. Стів зрозумів, як
|
||||
вимкнути Intel ME за допомогою 2 бітів перемикання в дескрипторі, а також як видалити область
|
||||
Intel ME з флеш-пам'яті.
|
||||
|
||||
Ґрунтуючись на його дослідженні, я, Лія Роу, працюючи разом зі Стівом, також виконала зворотню розробку
|
||||
області Intel GbE NVM (енергонезалежна пам'ять) у
|
||||
завантажувальній флеш-пам'яті. Цей регіон визначає параметри конфігурації для вбудованої мережевої карти Intel
|
||||
GbE, якщо присутня.
|
||||
|
||||
На основі цього я змогла взяти початкове підтвердження концепції та написати
|
||||
утиліту `ich9gen`, яка генерує Intel Flash Descriptor та регіон GbE NVM,
|
||||
з нуля, без визначення регіону Intel ME. Саме цей інструмент,
|
||||
інструмент `ich9gen`, використовує Libreboot для надання образів ROM для GM45+ICH9M
|
||||
платформ (таких як ThinkPad X200/T400/T500/W500), із повнофункціональним
|
||||
дескриптором та функціональним Gigabit Ethernet, але *без* необхідності мікропрограми Intel
|
||||
Management Engine (ME), що робить ці машини *вільними* (ME
|
||||
повністю вимкнено, коли ви використовуєте образ дескриптора+gbe, створене `ich9gen`).
|
||||
|
||||
З *моїм* інструментом `ich9gen` (інструмент Стіва називався `ich9deblob`), вам більше
|
||||
не потрібен був дамп оригінальної мікропрограми Lenovo BIOS! Я не могла би написати цей інструмент
|
||||
без первинного підтвердження концепції Стіва. Я працювала з ним
|
||||
протягом багатьох місяців. Вся GM45+ICH9M підтримка (X200, T400 і так далі) в
|
||||
Libreboot стала можливою завдяки його роботі у 2014 році.
|
||||
|
||||
Тімоті Пірсон
|
||||
---------------
|
||||
|
||||
Перенес плату ASUS KGPE-D16 до coreboot для компанії Raptor
|
||||
Engineering, генеральним директором якої є Тімоті.
|
||||
Тімоті підтримує цей код у coreboot, допомогаючи проекту,
|
||||
з його інтеграцією з libreboot. Контактні
|
||||
дані цієї людини є на сайті raptor.
|
||||
|
||||
**Підтримку D16 було припинено 19 листопада 2022 року. Ви все ще можете використовувати
|
||||
старіші версії Libreboot, і старіші випуски.**
|
||||
|
||||
Swift Geek
|
||||
----------
|
||||
|
||||
Додав патч для ich9gen для створення дескрипторів розміром 16MiB.
|
||||
|
||||
Після цього Swift Geek повільно почав долучатися, поки не став розробником на повний
|
||||
робочий день. Внески Swift Geek насправді ніколи не були у формі *коду*,
|
||||
але те, що йому не вистачало в коді, він компенсував чудовою підтримкою як для користувачів,
|
||||
так і для інших розробників, допомагаючи іншим дізнатися більше про технології на
|
||||
низькому рівні.
|
||||
|
||||
Коли Swift Geek був учасником проекту, його роль здебільшого полягала в
|
||||
наданні підтримки користувачам (на каналі IRC) і проведенні досліджень. Swift Geek знає
|
||||
багато про апаратне забезпечення. Swift Geek також зробив деяку апстрім розробку GRUB.
|
||||
|
||||
Swift Geek неодноразово надавав технічні поради Лії Роу
|
||||
та допоміг їй покращити її навички паяння, а також навчив її
|
||||
деяким навичкам ремонту, до того моменту, коли вона тепер може виправляти більшість несправностей
|
||||
на материнських платах ThinkPad (під час перегляду схем та бордв'ю).
|
||||
|
||||
Swiftgeek залишив проект у березні 2021 року. Я, Лія Роу, бажаю його всього найкращого в його
|
||||
починаннях і дуже вдячна за його численні внески протягом багатьох
|
||||
років.
|
||||
|
||||
vitali64
|
||||
--------
|
||||
|
||||
Додав підтримку cstate 3 на macbook21, що забезпечує тривалий термін служби батареї
|
||||
та нижчу температуру процесора під час простою. vitali64 на irc
|
||||
|
|
@ -25,28 +25,6 @@ libreboot from the available source code.
|
|||
The following document describes how `lbmk` works, and how you can make changes
|
||||
to it: [libreboot maintenance manual](../maintain/)
|
||||
|
||||
Multi-threaded builds
|
||||
=====================
|
||||
|
||||
Libreboot's build system defaults to a single build thread, but you can change
|
||||
it by doing e.g.
|
||||
|
||||
export XBMK_THREADS=4
|
||||
|
||||
This would make lbmk run on 4 threads.
|
||||
|
||||
More specifically: when compiling source trees via `script/trees`, `-jTHREADS`
|
||||
is passed, where THREADS is the number of threads. This is also set when running
|
||||
xz commands for compression, using the `-t` option.
|
||||
|
||||
Environmental variables
|
||||
=======================
|
||||
|
||||
Please read about environmental variables in [the build
|
||||
instructions](../maintain/), before running lbmk. You should set
|
||||
your variables accordingly, though you do not technically need to; some
|
||||
of them may be useful, e.g. `LBMK_THREADS` (sets the number of build threads).
|
||||
|
||||
Sources
|
||||
=======
|
||||
|
||||
|
|
@ -108,9 +86,6 @@ On Fedora, you can use the following
|
|||
|
||||
sudo dnf install python-unversioned-command
|
||||
|
||||
On most modern distros, Python 2 is no longer included and Python 3 will be
|
||||
the only one available on the `python`.
|
||||
|
||||
How to compile Libreboot
|
||||
========================
|
||||
|
||||
|
|
@ -135,24 +110,24 @@ Fedora, Arch Linux/Parabola or Void Linux.
|
|||
|
||||
Some examples (run them as root, use use e.g. `sudo`, `doas`):
|
||||
|
||||
./mk dependencies ubuntu
|
||||
./build dependencies ubuntu
|
||||
|
||||
or
|
||||
|
||||
./mk dependencies debian
|
||||
./build dependencies debian
|
||||
|
||||
or
|
||||
|
||||
./mk dependencies fedora38
|
||||
./build dependencies fedora38
|
||||
|
||||
or
|
||||
|
||||
./mk dependencies arch
|
||||
./build dependencies arch
|
||||
|
||||
NOTE: In case of Ubuntu 20.04 LTS or derived distros for that specific release,
|
||||
use the dedicated configuration file:
|
||||
|
||||
./mk dependencies ubuntu2004
|
||||
./build dependencies ubuntu2004
|
||||
|
||||
Check: `config/dependencies/` for list of supported distros.
|
||||
|
||||
|
|
@ -164,32 +139,32 @@ Next, build ROM images
|
|||
----------------------
|
||||
|
||||
Libreboot MaKe (lbmk) automatically runs all necessary commands; for
|
||||
example, `./mk -b coreboot` will automatically build the required payloads
|
||||
if not already compiled.
|
||||
example, `./build roms` will automatically run `./build grub`
|
||||
if the required GRUB payload (under `elf/grub/`) does not exist.
|
||||
|
||||
As a result, you can now (after installing the correct build dependencies) run
|
||||
just a single command, from a fresh Git clone, to build all ROM images:
|
||||
|
||||
./mk -b coreboot
|
||||
./build roms all
|
||||
|
||||
or even just build specific ROM images, e.g.:
|
||||
|
||||
./mk -b coreboot x60
|
||||
./build roms x60
|
||||
|
||||
or get a list of supported build targets:
|
||||
|
||||
./mk -b coreboot list
|
||||
./build roms list
|
||||
|
||||
Or maybe just build payloads?
|
||||
-----------------------------
|
||||
|
||||
If you wish to build payloads, you can also do that. For example:
|
||||
|
||||
./mk -b grub
|
||||
./build grub
|
||||
|
||||
./mk -b seabios
|
||||
./update trees -b seabios
|
||||
|
||||
./mk -b u-boot
|
||||
./update trees -b u-boot
|
||||
|
||||
Previous steps will be performed automatically. However, you can *still* run
|
||||
individual parts of the build system manually, if you choose. This may be
|
||||
|
|
@ -202,7 +177,7 @@ Want to modify Libreboot?
|
|||
Check the [lbmk maintenance manual](../maintain/) for guidance. You may for
|
||||
example want to modify a config, e.g.:
|
||||
|
||||
./mk -m coreboot x200_8mb
|
||||
./update trees -m coreboot x200_8mb
|
||||
|
||||
Or perhaps add a new board! The maintenance manual will teach you how the
|
||||
Libreboot build system (lbmk) works!
|
||||
|
|
|
|||
|
|
@ -35,55 +35,6 @@ libreboot з доступного джерельного коду.
|
|||
Наступний документ описує те, як працює `lbmk`, і як ви можете робити зміни
|
||||
до нього: [керівництво обслуговування libreboot](../maintain/)
|
||||
|
||||
Release status
|
||||
==============
|
||||
|
||||
Information about status will be reported during builds; if a board is
|
||||
marked as stable, the build proceeds without further input. If the board is
|
||||
marked anything other, a warning appears asking if you wish to proceed; to
|
||||
disable these warnings, do this before building (not recommended):
|
||||
|
||||
export XBMK_STATUS=n
|
||||
|
||||
In Libreboot, we specify: `stable`, `unstable`, `broken` or `untested`.
|
||||
The "unstable" marking means that the board boots mostly/entirely reliably
|
||||
annd should be safe to use, but may have a few issues, but nothing which would,
|
||||
for example, cause safety issues e.g. thermal, data reliability etc.
|
||||
|
||||
The `broken` setting means that a given board will likely brick if flashed.
|
||||
The `untested` setting means untested.
|
||||
|
||||
Release status is always set with regards to the current lbmk revision, on
|
||||
the theory that the current revision is being used to generate a full release.
|
||||
The setting is decided on a board-by-board basis, taking its various quirks
|
||||
and idiosynrasies into account.
|
||||
|
||||
Multi-threaded builds
|
||||
=====================
|
||||
|
||||
Libreboot's build system defaults to a single build thread, but you can change
|
||||
it by doing e.g.
|
||||
|
||||
export XBMK_THREADS=4
|
||||
|
||||
This would make lbmk run on 4 threads.
|
||||
|
||||
Environmental variables
|
||||
=======================
|
||||
|
||||
Please read about environmental variables in [the build
|
||||
instructions](../maintain/), before running lbmk. You should set
|
||||
your variables accordingly, though you do not technically need to; some
|
||||
of them may be useful, e.g. `XBMK_THREADS` (sets the number of build threads).
|
||||
|
||||
Environmental variables
|
||||
=======================
|
||||
|
||||
Please read about environmental variables in [the build
|
||||
instructions](../maintain/), before running lbmk. You should set
|
||||
your variables accordingly, though you do not technically need to; some
|
||||
of them may be useful, e.g. `XBMK_THREADS` (sets the number of build threads).
|
||||
|
||||
Git
|
||||
===
|
||||
|
||||
|
|
@ -127,15 +78,15 @@ time or date can cause connections to be dropped during negotiation.
|
|||
libreboot включає сценарій, який автоматично встановлює apt-get залежності
|
||||
в Ubuntu 20.04:
|
||||
|
||||
sudo ./mk dependencies ubuntu2004
|
||||
sudo ./build dependencies ubuntu2004
|
||||
|
||||
Окремі сценарії також існують:
|
||||
|
||||
sudo ./mk dependencies debian
|
||||
sudo ./build dependencies debian
|
||||
|
||||
sudo ./mk dependencies arch
|
||||
sudo ./build dependencies arch
|
||||
|
||||
sudo ./mk dependencies void
|
||||
sudo ./build dependencies void
|
||||
|
||||
Check: `config/dependencies/` for list of supported distros.
|
||||
|
||||
|
|
@ -150,23 +101,23 @@ libreboot Make (lbmk) автоматично виконує всі необхі
|
|||
В якості результату, ви тепер можете (після встановлення правильних залежностей побудови) виконати
|
||||
лише одну команду, з свіжого Git clone, для побудови образів ROM:
|
||||
|
||||
./mk -b coreboot
|
||||
./build roms all
|
||||
|
||||
або навіть побудувати конкретні образи ROM, такі як:
|
||||
|
||||
./mk -b coreboot x60
|
||||
./build roms x60
|
||||
|
||||
or get a list of supported build targets:
|
||||
|
||||
./mk -b coreboot list
|
||||
./build roms list
|
||||
|
||||
Якщо ви бажаєте побудувати корисні навантаження, можете зробити це. Наприклад:
|
||||
|
||||
./mk -b grub
|
||||
./build grub
|
||||
|
||||
./mk -b seabios
|
||||
./update trees -b seabios
|
||||
|
||||
./mk -b u-boot
|
||||
./update trees -b u-boot
|
||||
|
||||
Попередні кроки буде виконано автоматично. Однак, ви можете *досі* виконати
|
||||
окремі частини системи побудови власноруч, якщо виберете. Це може бути
|
||||
|
|
|
|||
|
|
@ -3,6 +3,9 @@ title: GRUB payload
|
|||
x-toc-enable: true
|
||||
...
|
||||
|
||||
TODO: this guide should be reviewed and updated. Some info might be out of
|
||||
date.
|
||||
|
||||
GRUB already has excellent
|
||||
documentation, but there are aspects of libreboot that deserve special
|
||||
treatment. libreboot provides the option to boot GRUB directly, running on
|
||||
|
|
@ -30,16 +33,10 @@ files:
|
|||
When you build GRUB from source, you can use the `grub-mklayout` program to
|
||||
create a special keymap file for GRUB. [Learn how to build GRUB](../build/)
|
||||
|
||||
Te compile GRUB, in lbmk, do this:
|
||||
|
||||
./mk -b grub default
|
||||
|
||||
Other GRUB trees are available, but the `default` one will do for now.
|
||||
|
||||
When you've built GRUB, using `lbmk` (libreboot build system), take your kepmap
|
||||
file (generated by ckbcomp) and run it through `grub-mklayout` like so:
|
||||
|
||||
cat frazerty | ./src/grub/default/grub-mklayout -o frazerty.gkb
|
||||
cat frazerty | ./src/grub/grub-mklayout -o frazerty.gkb
|
||||
|
||||
Place the newly created `.gkb` file under `config/grub/keymap` in lbmk. When
|
||||
you build libreboot, a ROM image with GRUB payload and your newly created
|
||||
|
|
|
|||
|
|
@ -0,0 +1,9 @@
|
|||
---
|
||||
title: ASUS Chromebook C201
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
This page is absolete. Refer to these pages instead:
|
||||
|
||||
* [C201 flashing instructions](../install/c201.md)
|
||||
* [Chromebook flashing instructions](../install/chromebooks.md)
|
||||
|
|
@ -0,0 +1,61 @@
|
|||
---
|
||||
title: Intel D510MO and D410PT desktop boards
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
Intel D510MO
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Intel |
|
||||
| **Name** | D510MO/D410PT |
|
||||
| **Released** | 2010 |
|
||||
| **Chipset** | Intel NM10 Express (Mount Olive) |
|
||||
| **CPU** | Intel Atom |
|
||||
| **Graphics** | Integrated |
|
||||
| **Display** | None. |
|
||||
| **Memory** | Up to 4GB |
|
||||
| **Architecture** | x86_64 |
|
||||
| **Original boot firmware** | Intel BIOS |
|
||||
| **Intel ME/AMD PSP** | Not present. |
|
||||
| **Flash chip** | ? |
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|----------------|---------------------------------------|
|
||||
| **Internal flashing with original boot firmware** | N |
|
||||
| **Display** | - |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | P+ |
|
||||
| **External output** | P+ |
|
||||
| **Display brightness** | - |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
This is a desktop board using intel hardware (circa \~2009, ICH7
|
||||
southbridge, similar performance-wise to the ThinkPad X200. It can make
|
||||
for quite a nifty desktop. Powered by libreboot.
|
||||
|
||||
NOTE: D410PT is another name and it's the same board. Flash the exact same
|
||||
ROM and it should work.
|
||||
|
||||
NOTE: This board has a working framebuffer in Grub, but in Linux in
|
||||
native resolution the display is unusable due to some raminit issues.
|
||||
This board can however be used for building a headless server.
|
||||
|
||||
Flashing instructions can be found at
|
||||
[../install/d510mo.md](../install/d510mo.md)
|
||||
|
|
@ -0,0 +1,124 @@
|
|||
---
|
||||
title: Intel D945GCLF desktop board
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
<img tabindex=1 alt="D945GCLF" class="p" src="https://av.libreboot.org/d945gclf/d945gclf.jpg" /><span class="f"><img src="https://av.libreboot.org/d945gclf/d945gclf.jpg" /></span>
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Intel |
|
||||
| **Name** | D945GCLF/D945GCLF2D |
|
||||
| **Released** | 2008 |
|
||||
| **Chipset** | Intel Calistoga 945GC |
|
||||
| **CPU** | Intel Atom |
|
||||
| **Graphics** | ? |
|
||||
| **Display** | None. |
|
||||
| **Memory** | Up to 2GB |
|
||||
| **Architecture** | x86_64 |
|
||||
| **Original boot firmware** | Intel BIOS |
|
||||
| **Intel ME/AMD PSP** | Not present. |
|
||||
| **Flash chip** | SOIC-8 512KiB |
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | | Notes |
|
||||
|----------------|---------------------------------------|-------|
|
||||
| **Internal flashing with original boot firmware** | N | |
|
||||
| **Display** | - | |
|
||||
| **Audio** | W+ | |
|
||||
| **RAM Init** | W+ | |
|
||||
| **External output** | W+ | |
|
||||
| **Display brightness** | - | |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|--------------|
|
||||
| **GRUB** | Doesn't work |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Doesn't work |
|
||||
</div>
|
||||
If you just want flashing instructions, go to
|
||||
[../install/d945gclf.md](../install/d945gclf.md)
|
||||
|
||||
D945GCLF2D also reported working by a user.
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
This board is a mini-itx desktop board for 2008. It uses an atom 230,
|
||||
which is a singe core CPU but it is hyperthreaded so it appears to have
|
||||
2 thread to the OS. The flash chip is very small, 512KiB, so grub2 does
|
||||
not fit, which is why libreboot has to use seabios on this target. Full
|
||||
disk encryption like on other supported targets will not be possible, so
|
||||
plan accordingly.
|
||||
|
||||
This board has a 945gc chipset which is the desktop equivalent of 945gm
|
||||
which can be found in the Lenovo x60/t60 or macbook2,1. This chipset
|
||||
features an ICH7 southbridge. It has 1 DIMM slot that can accommodate up
|
||||
to 2G of DDR2 RAM.
|
||||
|
||||
Connectivity-wise it has 1 PCI slot, a 10/100 ethernet port, 4 usb slot
|
||||
and 4 usb ports, with one internal header and 2 SATA ports.
|
||||
|
||||
The D945GCLF2 is an upgraded version of this board. The differences are:
|
||||
1 more USB header, 10/100/1000 ethernet and a dual core cpu (also
|
||||
hyperthreaded). Since the board is almost identical (and coreboot code
|
||||
seem to indicate that it works, since MAX\_CPU=4 is set), it is believed
|
||||
that it should also work but this is untested.
|
||||
|
||||
Remarks about vendor bios:
|
||||
--------------------------
|
||||
|
||||
- Without coreboot/libreboot this board is completely useless, since the
|
||||
vendor bios is very bad. It cannot boot from any HDD whether it is
|
||||
connected to the SATA port or USB. With libreboot it works just
|
||||
fine.
|
||||
|
||||
- The vendor bios write protects the flash so it requires external
|
||||
flashing to install libreboot on this device. Once libreboot is
|
||||
flashed there is no problem to update the firmware internally
|
||||
|
||||
Here is an image of the board:\
|
||||
\
|
||||
Here is an image of the D945GCLF2 board:\
|
||||
{width="80%" height="80%"}\
|
||||
And SPI SOIC8 flash chip\
|
||||
{width="50%" height="50%"}
|
||||
|
||||
How to replace thermal paste and fan
|
||||
------------------------------------
|
||||
|
||||
This board comes with very crappy disposable loud fan, that one has no
|
||||
bearings, which can not be repaired or oiled properly, do not waste your
|
||||
time trying to fix it, just buy one chinese same size fan\
|
||||
{width="50%" height="50%"}
|
||||
{width="50%" height="50%"}\
|
||||
Make sure that new one has same wiring\
|
||||
{width="50%" height="50%"}\
|
||||
This is a new one, with bearing and maintenable\
|
||||
{width="50%" height="50%"}
|
||||
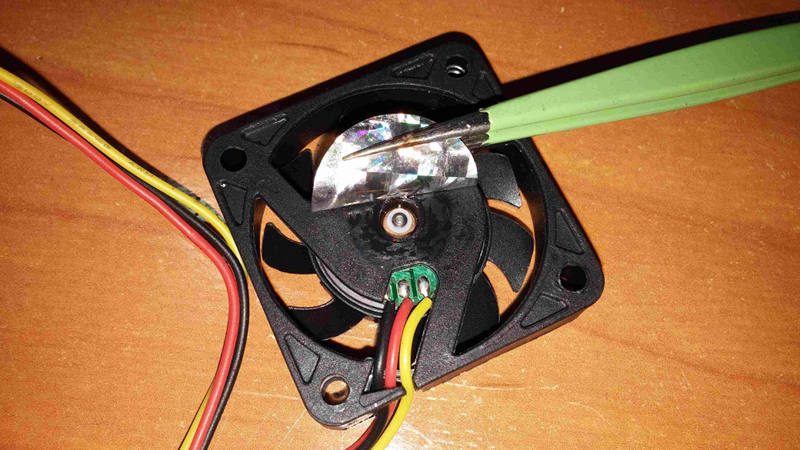{width="50%" height="50%"}\
|
||||
Now remove the both coolers rotating them a bit, slowly, then clean both
|
||||
silicons and both coolers (removing cmos battery first is recommended)\
|
||||
{width="50%" height="50%"}\
|
||||
Put a little bit of non conductive thermal paste on both silicons (only
|
||||
cpu silicon iis shown on that image)\
|
||||
{width="50%" height="50%"}\
|
||||
|
||||
Before assembling new fan, some need new longer screws, make sure having
|
||||
these (on the left is original one, too short for new fan)\
|
||||
{width="50%" height="50%"}\
|
||||
After that, assemble your new fan into CPU cooler\
|
||||
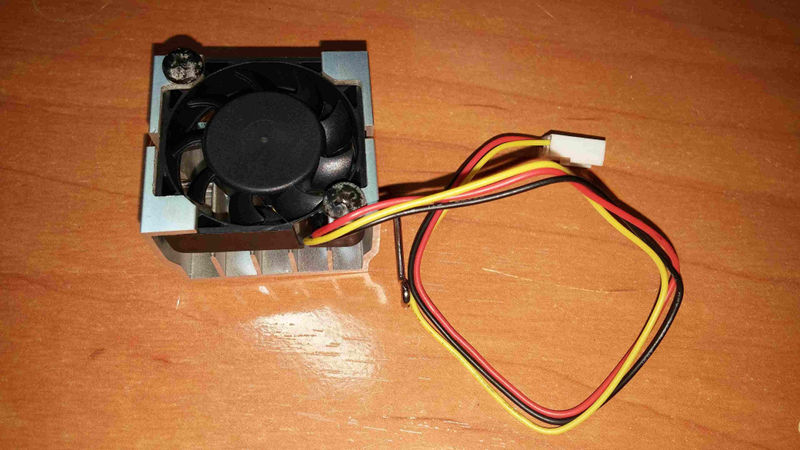{width="50%" height="50%"}\
|
||||
Finally assemle both coolers on both chips, do not forget put in the CPU
|
||||
fan connector back, and you are done.
|
||||
|
|
@ -48,7 +48,7 @@ P*: Partially works with blobs
|
|||
|
||||
| ***Features*** | |
|
||||
|---------------------------------------------------|----|
|
||||
| **Internal flashing with original boot firmware** | W+ |
|
||||
| **Internal flashing with original boot firmware** | ? |
|
||||
| **Display (if Intel GPU)** | W+ |
|
||||
| **Display (discrete CPU, SeaBIOS payload only)** | W* |
|
||||
| **Audio** | W+ |
|
||||
|
|
@ -66,7 +66,7 @@ Introduction
|
|||
**Unavailable in Libreboot 20240126 or earlier. You must [compile from
|
||||
source](../build/), or use a version newer than Libreboot 20240126**
|
||||
|
||||
Official information about this machine can be found here:
|
||||
Official information about the laptop can be found here:
|
||||
<https://i.dell.com/sites/doccontent/shared-content/data-sheets/en/Documents/optiplex-9020-micro-technical-spec-sheet.pdf>
|
||||
|
||||
Buy Libreboot preinstalled
|
||||
|
|
@ -91,64 +91,23 @@ Kukri's patch is here:
|
|||
This patch, at this revision (patchset 31), is what Libreboot uses for this
|
||||
port.
|
||||
|
||||
QUBES: how to get it working
|
||||
-------------------
|
||||
|
||||
Qubes requires IOMMU to be turned on. Please now read the next section.
|
||||
Qubes *WILL* work, if you configure Libreboot as directed below, but otherwise
|
||||
it will fail by default. This is because Libreboot *disables the IOMMU by
|
||||
default*, on this board.
|
||||
|
||||
Graphics cards and IOMMU
|
||||
Graphics cards
|
||||
--------------
|
||||
|
||||
IOMMU is buggy for some reason (we don't know why yet), when you plug in
|
||||
a graphics card. The graphics card simply won't work. On some of them,
|
||||
you can use the console but as soon as you start xorg, it will just b0rk.
|
||||
On current lbmk master, graphics cards *do* work. The option to hide PEG
|
||||
devices from MRC was disabled. Now when you insert a graphics card, the
|
||||
onboard Intel GPU is disabled and the graphics card is used instead.
|
||||
|
||||
Current Libreboot revisions *disable IOMMU by default*, on this board. The
|
||||
coreboot code for initialising IOMMU was modified by the Libreboot project, to
|
||||
make it a toggle. IOMMU works fine if you use only Intel graphics.
|
||||
|
||||
The way coreboot works is this: if vt-d is present on the CPU, it enables an
|
||||
IOMMU, and only if vt-d is present. This is still the behaviour in Libreboot,
|
||||
but Libreboot adds an additional check: if `iommu` is not set in nvram, it
|
||||
defaults to on, but if it's set to disabled, then IOMMU is not initialised.
|
||||
|
||||
On all other Haswell boards, LIbreboot enables IOMMU by default. To enable
|
||||
it on the 9020, do this on your ROM:
|
||||
|
||||
nvramtool -C libreboot.rom -w iommu=Enable
|
||||
|
||||
Then flash the ROM image. You can find nvram
|
||||
under `src/coreboot/default/util/nvramtool`. Do this in lbmk if you don't
|
||||
already havse `src/coreboot/default/`:
|
||||
|
||||
./update trees -f coreboot default
|
||||
|
||||
Then do this:
|
||||
|
||||
make -C src/coreboot/default/util/nvramtool
|
||||
|
||||
The binary `nvramtool` will then live in that directory. More information
|
||||
available in [Libreboot build instructions](../build/). Information about
|
||||
dumping/flashing the ROM can be found
|
||||
in [Libreboot flashing instructions](../install/)
|
||||
and [Libreboot external flashing instructions](../install/spi.md).
|
||||
|
||||
NOTE: If IOMMU is enabled, you can still use a graphics card, but you must
|
||||
pass this on the Linux cmdline paramaters: `iommu=off`
|
||||
|
||||
NOTE2: Libreboot uses a *static option table* on all boards that have nvram,
|
||||
which is why you must use the `-C` option on your ROM, to change the static
|
||||
table that is baked into it.
|
||||
|
||||
Here is an example of the type of errors we got when testing graphics cards
|
||||
with IOMMU enabled:
|
||||
NOTE: You must set `iommu=off` in your linux cmdline. For instance, set this
|
||||
in `/etc/default/grub` and regenerate your GRUB config. With the IOMMU turned
|
||||
off, graphics cards work fine. Otherwise, with IOMMU turned on, you might get
|
||||
this error:
|
||||
|
||||
<https://av.vimuser.org/error.jpg>
|
||||
|
||||
Make sure to configure your image accordingly.
|
||||
NOTE2: You *can* use the onboard Intel GPU (without a graphics card inserted),
|
||||
and leave IOMMU turned on. You only need to disable the IOMMU when a graphics
|
||||
card is inserted.
|
||||
|
||||
7020 compatibility
|
||||
------------------
|
||||
|
|
@ -162,13 +121,13 @@ separate targets for MT and SFF.
|
|||
Build ROM image from source
|
||||
---------------------------
|
||||
|
||||
For the MT variant (7020 MT and 9020 MT):
|
||||
For the MT variant (7020 MT and 9020 SFF):
|
||||
|
||||
./mk -b coreboot dell9020mt_nri_12mb
|
||||
./build roms dell9020mt_12mb
|
||||
|
||||
For the SFF variant (7020 SFF and 9020 SFF):
|
||||
For the SFF variant (7020 MT and 7020 SFF):
|
||||
|
||||
./mk -b coreboot dell9020sff_nri_12mb
|
||||
./build roms dell9020sff_12mb
|
||||
|
||||
It is important that you choose the right one. The MT variant is the full
|
||||
MTX tower.
|
||||
|
|
@ -200,21 +159,6 @@ Flash a ROM image (software)
|
|||
If you're already running Libreboot, and you don't have flash protection
|
||||
turned on, [internal flashing](../install/) is possible.
|
||||
|
||||
Internal flashing can also be done with the original Dell BIOS, if the
|
||||
SERVICE_MODE jumper near the PCIe slots is installed. Before flashing,
|
||||
|
||||
rmmod spi-intel-platform
|
||||
|
||||
needs to be run to prevent errors. Once Libreboot is installed, the
|
||||
SERVICE_MODE jumper can be removed.
|
||||
|
||||
**Note: The Dell BIOS can write EFI variables to flash when shutting
|
||||
down, which could corrupt the newly flashed Libreboot ROM and render
|
||||
the system unusable. To prevent this, after flashing internally from
|
||||
the original Dell BIOS, remove power from the computer instead of
|
||||
shutting it down normally. It's recommended to use a live USB instead
|
||||
of the internal drive to prevent potential filesystem corruption.**
|
||||
|
||||
Flash a ROM image (hardware)
|
||||
-----------------
|
||||
|
||||
|
|
@ -224,7 +168,8 @@ This is to prevent short circuiting and power surges while flashing.**
|
|||
For general information, please refer to [25xx NOR flash
|
||||
instructions](../install/spi.md) - that page refers to use of socketed flash.
|
||||
|
||||
There are two SOIC-8 chips. You can split up your 12MB ROM image
|
||||
This machine is somewhat cumbersome to flash, because it has a SOIC-16 flash
|
||||
for the first 8MB part, and 4MB SOIC8. You can split up your 12MB ROM image
|
||||
like so:
|
||||
|
||||
dd if=libreboot.rom of=4mb.rom bs=1M skip=8
|
||||
|
|
@ -0,0 +1,78 @@
|
|||
---
|
||||
title: Dell Latitude E5520
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
Dell Latitude E5520
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Dell |
|
||||
| **Name** | Latitude E5520 |
|
||||
| **Variants** | E5520 with Intel GPU supported |
|
||||
| **Released** | 2012 |
|
||||
| **Chipset** | Intel Sandy Bridge |
|
||||
| **CPU** | Intel Core i3, i5 or i7 |
|
||||
| **Graphics** | Intel HD 4000 and unsupported Nvidia NVS 5200M |
|
||||
| **Display** | 1366x768/1600x900 TFT |
|
||||
| **Memory** | 4 or 8GB (Upgradable to 16GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | SMSC MEC5055 with proprietary firmware |
|
||||
| **Original boot firmware** | Dell UEFI |
|
||||
| **Intel ME/AMD PSP** | Present, neutered |
|
||||
| **Flash chip** | 2xSOIC-8, 6MiB (4MiB and 2MiB in combination) |
|
||||
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|---------------------------------------------------|----|
|
||||
| **Internal flashing with original boot firmware** | W+ |
|
||||
| **Display (if Intel GPU)** | W+ |
|
||||
| **Display (if Nvidia GPU)** | U |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Introduction
|
||||
============
|
||||
|
||||
**Libreboot 20231021 and releases newer than this have ROMs available for
|
||||
Dell Latitude E5520.**
|
||||
|
||||
ROM images for Dell Latitude E5520 are available for flashing in the Libreboot
|
||||
releases *after* 20230625, or you can compile a ROM image for installation via
|
||||
lbmk, see: [build instructions](../build/)
|
||||
|
||||
Only the Intel GPU variants are supported, currently. All models with Intel GPU
|
||||
are assumed to work.
|
||||
|
||||
Unlike the E6400, this one does require a neutered Intel ME image to run. This
|
||||
means running it through `me_cleaner` before flashing; the Libreboot build
|
||||
system does this automatically, during build, or you can insert a neutered
|
||||
ROM image using the vendor scripts, see guide:
|
||||
|
||||
[Insert vendor files](../install/ivy_has_common.md)
|
||||
|
||||
As with the E6400, this one is flashable in software, from Dell UEFI firmware
|
||||
to Libreboot. Please refer to the installation instructions.
|
||||
|
||||
**To install Libreboot, see: [E5520 installation
|
||||
instructions](../install/e6430.md)**
|
||||
|
|
@ -0,0 +1,80 @@
|
|||
---
|
||||
title: Dell Latitude E5530
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
Dell Latitude E5530
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Dell |
|
||||
| **Name** | Latitude E5530 |
|
||||
| **Variants** | E5530 with Intel GPU supported |
|
||||
| **Released** | 2012 |
|
||||
| **Chipset** | Intel Ivy Bridge |
|
||||
| **CPU** | Intel Core i3, i5 or i7 |
|
||||
| **Graphics** | Intel HD 4000 and unsupported Nvidia NVS 5200M |
|
||||
| **Display** | 1366x768/1600x900 TFT |
|
||||
| **Memory** | 4 or 8GB (Upgradable to 16GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | SMSC MEC5055 with proprietary firmware |
|
||||
| **Original boot firmware** | Dell UEFI |
|
||||
| **Intel ME/AMD PSP** | Present, neutered |
|
||||
| **Flash chip** | 2xSOIC-8, 12MiB (8MiB and 4MiB in combination) |
|
||||
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|---------------------------------------------------|----|
|
||||
| **Internal flashing with original boot firmware** | W+ |
|
||||
| **Display (if Intel GPU)** | W+ |
|
||||
| **Display (if Nvidia GPU)** | U |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Introduction
|
||||
============
|
||||
|
||||
**Libreboot 20231021 and releases newer than this have ROMs available for
|
||||
Dell Latitude E5530.**
|
||||
|
||||
ROM images for Dell Latitude E5530 are available for flashing in the Libreboot
|
||||
releases *after* 20230625, or you can compile a ROM image for installation via
|
||||
lbmk, see: [build instructions](../build/)
|
||||
|
||||
Only the Intel GPU variants are supported, currently. All models with Intel GPU
|
||||
are assumed to work.
|
||||
|
||||
Unlike the E6400, this one does require a neutered Intel ME image to run. This
|
||||
means running it through `me_cleaner` before flashing; the Libreboot build
|
||||
system does this automatically, during build, or you can insert a neutered
|
||||
ROM image using the vendor scripts, see guide:
|
||||
|
||||
[Insert vendor files](../install/ivy_has_common.md)
|
||||
|
||||
As with the E6400, this one is flashable in software, from Dell UEFI firmware
|
||||
to Libreboot. Please refer to the installation instructions.
|
||||
|
||||
**To install Libreboot, see: [E5530 installation
|
||||
instructions](../install/e6430.md)**
|
||||
|
||||
Of note: this machine features a Broadnic nic, for ethernet.
|
||||
|
|
@ -0,0 +1,271 @@
|
|||
---
|
||||
title: Dell Latitude E6400
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
<img tabindex=1 alt="Dell Latitude E6400" class="p" src="https://av.libreboot.org/e6400/e6400-seabios.jpg" /><span class="f"><img src="https://av.libreboot.org/e6400/e6400-seabios.jpg" /></span> <img tabindex=1 alt="Dell Latitude E6400 XFR" class="p" style="max-width:24em" src="https://av.libreboot.org/e6400/e6400xfr-seabios.jpg" /><span class="f"><img src="https://av.libreboot.org/e6400/e6400xfr-seabios.jpg" /></span>
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Dell |
|
||||
| **Name** | Latitude E6400 |
|
||||
| **Variants** | E6400, E6400 XFR and E6400 ATG are supported |
|
||||
| **Released** | 2009 |
|
||||
| **Chipset** | Intel Cantiga GM45(Intel GPU)/PM45(Nvidia GPU) |
|
||||
| **CPU** | Intel Core 2 Duo (Penryn family). |
|
||||
| **Graphics** | Intel GMA 4500MHD (and NVidia Quadro NVS 160M
|
||||
on some models) |
|
||||
| **Display** | 1280x800/1440x900 TFT |
|
||||
| **Memory** | 2 or 4GB (Upgradable to 8GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | SMSC MEC5035 with proprietary firmware |
|
||||
| **Original boot firmware** | Dell BIOS |
|
||||
| **Intel ME/AMD PSP** | Present. Can be completely disabled. |
|
||||
| **Flash chip** | SOIC-8 4MiB or 2MiB+4MiB |
|
||||
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|---------------------------------------------------|----|
|
||||
| **Internal flashing with original boot firmware** | W+ |
|
||||
| **Display (if Intel GPU)** | W+ |
|
||||
| **Display (if Nvidia GPU)** | W* |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Introduction
|
||||
============
|
||||
|
||||
Known supported variants: E6400, E6400 XFR and E6400 ATG. This page has
|
||||
been updated to include information about Nvidia GPU variants. See news post:
|
||||
[Dell Latitude E6400 XFR support confirmed, plus experimental Nvidia GPU
|
||||
support on E6400 variants](../../news/e6400nvidia.md).
|
||||
|
||||
**To install Libreboot, see: [E6400 installation
|
||||
instructions](../install/e6400.md)**
|
||||
|
||||
ROM images for Dell Latitude E6400 are available for flashing in the Libreboot
|
||||
release 20230423 onwards, or you can compile a ROM image for installation via
|
||||
lbmk, see: [build instructions](../build/)
|
||||
|
||||
There are two possible flash chip sizes for the E6400: 4MiB (32Mbit) or 2+4MiB
|
||||
(16Mbit+32MBit). Libreboot presently supports the 4MiB version, and provides
|
||||
8MiB images for those who upgrade their flash to 8MiB or 16MiB. There appears
|
||||
to be several possible mainboard PCBs for the E6400, which we believe mostly
|
||||
affects the GPU configuration and the number of available SPI flash footprints:
|
||||
|
||||
- LA-3801P: iGPU, possibly dual SPI (however only one may be populated)
|
||||
- LA-3803P: dGPU, dual SPI (however only one may be populated)
|
||||
- LA-3805P: iGPU, single SPI flash (4MiB)
|
||||
- LA-3806P: dGPU, unknown SPI configuration (likely at least 4MiB)
|
||||
|
||||
These PCB numbers can be found either under the black plastic in the RAM slots
|
||||
on the bottom (CPU side) of the board, the top left corner near the VGA port
|
||||
(top side, under the keyboard and palmrest), or near the CPU backplate (only
|
||||
requires removal of the keyboard).
|
||||
|
||||
We believe that all boards will have at least a single 4MiB flash chip,
|
||||
regardless of the number of SPI footprints. This is likely the most common
|
||||
configuration on most available systems. The 2+4MiB configuration likely
|
||||
would have only been used on systems with full Intel ME firmware with AMT
|
||||
functionality, though this configuration has not yet been encountered.
|
||||
|
||||
Most people will want to use the 4MiB images.
|
||||
|
||||
Intel GPU: 100% Free Software is possible
|
||||
---------------
|
||||
|
||||
This is a GM45/PM45 platform, so completely libre initialisation in
|
||||
coreboot is possible, provided by default in Libreboot.
|
||||
|
||||
Management Engine (ME) firmware removed
|
||||
-------------------------
|
||||
|
||||
This port in Libreboot makes use of `ich9gen` from ich9utils, which
|
||||
you can read about in the [ich9utils manual](../install/ich9utils.md) - this
|
||||
creates a no-ME setup. The Intel Management Engine firmware (ME) is completely
|
||||
removed, and the ME disabled, just like on ThinkPad X200, T400 and so on.
|
||||
|
||||
*The E6400 laptops may come with the ME (and sometimes AMT in addition) before
|
||||
flashing libreboot. Dell also sold configurations with the ME completely
|
||||
disabled, identifiable by a yellow sticker reading "3 ME Disabled" inside the
|
||||
bottom panel. This config sets the MeDisable bit in the IFD and sets the ME
|
||||
region almost entirely to 1's, with the occasional 32-bit value (likely not
|
||||
executable). libreboot disables and removes it by using a modified descriptor:
|
||||
see [../install/ich9utils.md](../install/ich9utils.md)*
|
||||
(contains notes, plus instructions)
|
||||
|
||||
Issues pertaining to Nvidia GPU variants
|
||||
========================================
|
||||
|
||||
Copper shim for GPU cooling
|
||||
---------------------------
|
||||
|
||||
NOTE: this section does *not* apply to XFR or ATG variants of E6400, which have
|
||||
a much beefier heatsink by default.
|
||||
|
||||
The *default* heatsink in Nvidia variants of E6400 (regular model) has thermal
|
||||
paste for the CPU, and a thermal *pad* for the GPU. This pad is woefully
|
||||
inadequate, but replacing it with *paste* is a bad idea, because of the gap
|
||||
there would be between heatsink plate and GPU die.
|
||||
|
||||
A solution for this would be to use a *copper shim*, with paste on each side,
|
||||
to replace the thermal pad.
|
||||
|
||||
This eBay seller seems to make and sell a lot of copper shims, specifically
|
||||
for E6400:
|
||||
|
||||
**SELLER LINK REMOVED.** - one will not be re-added. Putting ebay links on the
|
||||
Libreboot site is folly, because they disappear. Just search for it and see if
|
||||
you can find one for purchase. It's literally just a small bit of copper cut
|
||||
smooth to just the right size. Actually, there's a lot of engineering behind
|
||||
that, but installation is very simple, and any decent seller will provide
|
||||
guidance.
|
||||
|
||||
If you buy one of those, could you measure it? Tell Libreboot the dimensions.
|
||||
Get in touch with us. It would be nice to know precise specs, but that seller
|
||||
provides what you need. If you find similar listings elsewhere, please also
|
||||
let us know.
|
||||
|
||||
The shim will greatly reduce GPU temperatures, and probably improve performance
|
||||
due to less GPU throttling as a result of heat.
|
||||
|
||||
Nouveau(in Linux) currently broken
|
||||
----------------------------------
|
||||
|
||||
Nouveau is the libre driver in Linux, for Nvidia graphics. Nvidia themselves
|
||||
do not provide binary drivers anymore, for these GPUs. It crashes in Linux,
|
||||
when you try to start Xorg (Wayland is untested).
|
||||
|
||||
If you're booting an Nvidia variant in Linux, boot Linux with
|
||||
the `nomodeset` kernel option at boot time. This means that graphics are
|
||||
rendered in software.
|
||||
|
||||
Development discussion, for Nvidia variants of E6400, is available here:
|
||||
|
||||
<https://codeberg.org/libreboot/lbmk/issues/14>
|
||||
|
||||
OpenBSD's Nvidia driver works perfectly
|
||||
---------------------------------------
|
||||
|
||||
OpenBSD 7.3 was tested, on my Nvidia-model E6400, and Xorg works OK with
|
||||
the `nv` driver.
|
||||
|
||||
<img tabindex=1 class="l" style="max-width:35%" src="https://av.libreboot.org/openbsd.jpg" /><span class="f"><img src="https://av.libreboot.org/openbsd.jpg" /></span>
|
||||
|
||||
See: <https://www.openbsd.org/>
|
||||
|
||||
OpenBSD is a complete free 4.4BSD Unix operating system focused on portability,
|
||||
security and *code correctness*. It's quite useable for most day to day tasks.
|
||||
|
||||
You can find information in Libreboot about BSD operating systems on the
|
||||
main guide:
|
||||
|
||||
* [BSD Operating Systems](../bsd/)
|
||||
|
||||
FreeBSD and newer Linux (e.g. Archlinux) untested!
|
||||
--------------------------------------------------
|
||||
|
||||
FreeBSD has not yet been tested, as far as we know, but it should work.
|
||||
|
||||
[Testers needed! Please get in touch!](../maintain/testing.html)
|
||||
|
||||
**At the time of writing this post, FreeBSD
|
||||
and newer Linux have not yet been tested** (I plan to test *Arch Linux*), but
|
||||
the older Linux/Mesa version in Debian 11.6 works just fine in the Dell BIOS,
|
||||
and I've confirmed that it uses the exact same Video BIOS Option ROM.
|
||||
|
||||
Desktop environment / window manager on OpenBSD + Performance notes
|
||||
-------------------------------------------------------------------
|
||||
|
||||
TODO: This section could probably be moved to its own section. It's not really
|
||||
relevant to Libreboot per se, but it may help a few people.
|
||||
|
||||
Again, Linux's nouveau driver is currently broken. I've been playing with my
|
||||
E6400 (nvidia model) for a while and I've found that these things are a *must*
|
||||
for performance (the machine otherwise lags, openbsd's `nv` driver isn't quite
|
||||
as good as nouveau, when the nouveau one works that is):
|
||||
|
||||
* Use a lightweight desktop environment like LXQt, or lightweight window
|
||||
manager (OpenBSD has `cwm` in base, and it's excellent)
|
||||
* Install `obsdfreqd` which scales down the CPU speed during idle state; the
|
||||
GPU has a poor thermal pad for cooling and so if the CPU is running hot,
|
||||
that doesn't bode well for GPU temperatures either, and the GPU is likely
|
||||
lagging due to heat:
|
||||
|
||||
How to install `obsdfreqd`:
|
||||
|
||||
pkg_add obsdfreqd
|
||||
rcctl enable obsdfreqd
|
||||
|
||||
Now, before you start it, make sure `apmd` is disabled; it can be used, but
|
||||
not with the `-A` flag:
|
||||
|
||||
rcctl stop apmd
|
||||
rcctl disable apmd
|
||||
|
||||
Now start obsdfreqd:
|
||||
|
||||
rcctl start obsdfreqd
|
||||
|
||||
You will be well served to perform the copper shim mod, for GPU cooling.
|
||||
With `obsdfreqd`, your laptop will run much cooler. This is generally a good
|
||||
idea anyway, especially on laptops, to save electricity.
|
||||
|
||||
Of course, there are many tweaks that you can do to OpenBSD but the key is:
|
||||
don't use heavy bloated software. The term *lightweight* is misleading anyway;
|
||||
if the software does its job efficiently, and you're happy with it, then it is
|
||||
by definition superior for your purposes. So, "lightweight" is simply a word
|
||||
for "efficient" in many contexts. We should encourage the use and development
|
||||
of highly efficient software that runs more smoothly on old machines. The
|
||||
elitist attitude of *just buy a new computer* is quite damaging; re-use is
|
||||
always better, when that is feasible and safe. The power of BSD (and Linux) is
|
||||
precisely that you can tweak it to get the most use out of older hardware..
|
||||
|
||||
Another nice hint: higher resolution video like 1080p 60fps or above won't
|
||||
play smoothly at all in a web browser. In testing at least on OpenBSD 7.3,
|
||||
Firefox seems to have the best performance among all the web browsers, at least
|
||||
when I used it. Anything 720p 30/60fps will work ~OK.
|
||||
|
||||
For YouTube, you could use yt-dlp, which is available in ports, and use mpv to
|
||||
stream via yt-dlp. Or download manually with yt-dlp and play offline. See:
|
||||
|
||||
<https://github.com/yt-dlp/yt-dlp>
|
||||
|
||||
<https://mpv.io/>
|
||||
|
||||
Another hint: for watching youtube in the browser, Invidious works quite well.
|
||||
It's a frontend that lets you view it by proxy, and there are many instances
|
||||
of it online. For a list of instances, see:
|
||||
|
||||
<https://redirect.invidious.io/>
|
||||
|
||||
Unlike youtube.com, watching youtube via invidious works even with JavaScript
|
||||
turned off in the browser. You can use it to also search YouTube, and then
|
||||
paste the youtube.com link into yt-dlp or mpv; Invidious websites themselves
|
||||
also often provide a download button for videos.
|
||||
|
||||
The yt-dlp software may also work on a few other websites besides YouTube.
|
||||
Running with JavaScript turned *off* is generally recommended for performance,
|
||||
especially on slower machines, turning it on only when you need it. Many
|
||||
websites are just full of junk nowadays.
|
||||
|
||||
|
|
@ -0,0 +1,78 @@
|
|||
---
|
||||
title: Dell Latitude E6420
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
Dell Latitude E6420
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Dell |
|
||||
| **Name** | Latitude E6420 |
|
||||
| **Variants** | E6420 with Intel GPU supported |
|
||||
| **Released** | 2012 |
|
||||
| **Chipset** | Intel Sandy Bridge |
|
||||
| **CPU** | Intel Core i3, i5 or i7 |
|
||||
| **Graphics** | Intel HD 4000 and unsupported Nvidia NVS 5200M |
|
||||
| **Display** | 1366x768/1600x900 TFT |
|
||||
| **Memory** | 4 or 8GB (Upgradable to 16GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | SMSC MEC5055 with proprietary firmware |
|
||||
| **Original boot firmware** | Dell UEFI |
|
||||
| **Intel ME/AMD PSP** | Present, neutered |
|
||||
| **Flash chip** | 2xSOIC-8, 6MiB (4MiB and 2MiB in combination) |
|
||||
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|---------------------------------------------------|----|
|
||||
| **Internal flashing with original boot firmware** | W+ |
|
||||
| **Display (if Intel GPU)** | W+ |
|
||||
| **Display (if Nvidia GPU)** | U |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Introduction
|
||||
============
|
||||
|
||||
**Libreboot 20231021 and releases newer than this have ROMs available for
|
||||
Dell Latitude E6420.**
|
||||
|
||||
ROM images for Dell Latitude E6420 are available for flashing in the Libreboot
|
||||
releases *after* 20230625, or you can compile a ROM image for installation via
|
||||
lbmk, see: [build instructions](../build/)
|
||||
|
||||
Only the Intel GPU variants are supported, currently. All models with Intel GPU
|
||||
are assumed to work.
|
||||
|
||||
Unlike the E6400, this one does require a neutered Intel ME image to run. This
|
||||
means running it through `me_cleaner` before flashing; the Libreboot build
|
||||
system does this automatically, during build, or you can insert a neutered
|
||||
ROM image using the vendor scripts, see guide:
|
||||
|
||||
[Insert vendor files](../install/ivy_has_common.md)
|
||||
|
||||
As with the E6400, this one is flashable in software, from Dell UEFI firmware
|
||||
to Libreboot. Please refer to the installation instructions.
|
||||
|
||||
**To install Libreboot, see: [E6420 installation
|
||||
instructions](../install/e6430.md)**
|
||||
|
|
@ -0,0 +1,78 @@
|
|||
---
|
||||
title: Dell Latitude E6430
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
Dell Latitude E6430
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Dell |
|
||||
| **Name** | Latitude E6430 |
|
||||
| **Variants** | E6430 with Intel GPU supported |
|
||||
| **Released** | 2012 |
|
||||
| **Chipset** | Intel Ivy Bridge |
|
||||
| **CPU** | Intel Core i3, i5 or i7 |
|
||||
| **Graphics** | Intel HD 4000 and unsupported Nvidia NVS 5200M |
|
||||
| **Display** | 1366x768/1600x900 TFT |
|
||||
| **Memory** | 4 or 8GB (Upgradable to 16GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | SMSC MEC5055 with proprietary firmware |
|
||||
| **Original boot firmware** | Dell UEFI |
|
||||
| **Intel ME/AMD PSP** | Present, neutered |
|
||||
| **Flash chip** | 2xSOIC-8, 12MiB (8MiB and 4MiB in combination) |
|
||||
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|---------------------------------------------------|----|
|
||||
| **Internal flashing with original boot firmware** | W+ |
|
||||
| **Display (if Intel GPU)** | W+ |
|
||||
| **Display (if Nvidia GPU)** | U |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Introduction
|
||||
============
|
||||
|
||||
**Libreboot 20231021 and releases newer than this have ROMs available for
|
||||
Dell Latitude E6430.**
|
||||
|
||||
ROM images for Dell Latitude E6430 are available for flashing in the Libreboot
|
||||
releases *after* 20230625, or you can compile a ROM image for installation via
|
||||
lbmk, see: [build instructions](../build/)
|
||||
|
||||
Only the Intel GPU variants are supported, currently. All models with Intel GPU
|
||||
are assumed to work.
|
||||
|
||||
Unlike the E6400, this one does require a neutered Intel ME image to run. This
|
||||
means running it through `me_cleaner` before flashing; the Libreboot build
|
||||
system does this automatically, during build, or you can insert a neutered
|
||||
ROM image using the vendor scripts, see guide:
|
||||
|
||||
[Insert vendor files](../install/ivy_has_common.md)
|
||||
|
||||
As with the E6400, this one is flashable in software, from Dell UEFI firmware
|
||||
to Libreboot. Please refer to the installation instructions.
|
||||
|
||||
**To install Libreboot, see: [E6430 installation
|
||||
instructions](../install/e6430.md)**
|
||||
|
|
@ -0,0 +1,78 @@
|
|||
---
|
||||
title: Dell Latitude E6520
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
Dell Latitude E6520
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Dell |
|
||||
| **Name** | Latitude E6520 |
|
||||
| **Variants** | E6520 with Intel GPU supported |
|
||||
| **Released** | 2012 |
|
||||
| **Chipset** | Intel Sandy Bridge |
|
||||
| **CPU** | Intel Core i3, i5 or i7 |
|
||||
| **Graphics** | Intel HD 4000 and unsupported Nvidia NVS 5200M |
|
||||
| **Display** | 1366x768/1600x900 TFT |
|
||||
| **Memory** | 4 or 8GB (Upgradable to 16GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | SMSC MEC5055 with proprietary firmware |
|
||||
| **Original boot firmware** | Dell UEFI |
|
||||
| **Intel ME/AMD PSP** | Present, neutered |
|
||||
| **Flash chip** | 2xSOIC-8, 6MiB (4MiB and 2MiB in combination) |
|
||||
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|---------------------------------------------------|----|
|
||||
| **Internal flashing with original boot firmware** | W+ |
|
||||
| **Display (if Intel GPU)** | W+ |
|
||||
| **Display (if Nvidia GPU)** | U |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Introduction
|
||||
============
|
||||
|
||||
**Libreboot 20231021 and releases newer than this have ROMs available for
|
||||
Dell Latitude E6520.**
|
||||
|
||||
ROM images for Dell Latitude E6520 are available for flashing in the Libreboot
|
||||
releases *after* 20230625, or you can compile a ROM image for installation via
|
||||
lbmk, see: [build instructions](../build/)
|
||||
|
||||
Only the Intel GPU variants are supported, currently. All models with Intel GPU
|
||||
are assumed to work.
|
||||
|
||||
Unlike the E6400, this one does require a neutered Intel ME image to run. This
|
||||
means running it through `me_cleaner` before flashing; the Libreboot build
|
||||
system does this automatically, during build, or you can insert a neutered
|
||||
ROM image using the vendor scripts, see guide:
|
||||
|
||||
[Insert vendor files](../install/ivy_has_common.md)
|
||||
|
||||
As with the E6400, this one is flashable in software, from Dell UEFI firmware
|
||||
to Libreboot. Please refer to the installation instructions.
|
||||
|
||||
**To install Libreboot, see: [E6520 installation
|
||||
instructions](../install/e6430.md)**
|
||||
|
|
@ -0,0 +1,78 @@
|
|||
---
|
||||
title: Dell Latitude E6530
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
Dell Latitude E6530
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Dell |
|
||||
| **Name** | Latitude E6530 |
|
||||
| **Variants** | E6530 with Intel GPU supported |
|
||||
| **Released** | 2012 |
|
||||
| **Chipset** | Intel Ivy Bridge |
|
||||
| **CPU** | Intel Core i3, i5 or i7 |
|
||||
| **Graphics** | Intel HD 4000 and unsupported Nvidia NVS 5200M |
|
||||
| **Display** | 1366x768/1600x900 TFT |
|
||||
| **Memory** | 4 or 8GB (Upgradable to 16GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | SMSC MEC5055 with proprietary firmware |
|
||||
| **Original boot firmware** | Dell UEFI |
|
||||
| **Intel ME/AMD PSP** | Present, neutered |
|
||||
| **Flash chip** | 2xSOIC-8, 12MiB (8MiB and 4MiB in combination) |
|
||||
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|---------------------------------------------------|----|
|
||||
| **Internal flashing with original boot firmware** | W+ |
|
||||
| **Display (if Intel GPU)** | W+ |
|
||||
| **Display (if Nvidia GPU)** | U |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Introduction
|
||||
============
|
||||
|
||||
**Libreboot 20231021 and releases newer than this have ROMs available for
|
||||
Dell Latitude E6530.**
|
||||
|
||||
ROM images for Dell Latitude E6530 are available for flashing in the Libreboot
|
||||
releases *after* 20230625, or you can compile a ROM image for installation via
|
||||
lbmk, see: [build instructions](../build/)
|
||||
|
||||
Only the Intel GPU variants are supported, currently. All models with Intel GPU
|
||||
are assumed to work.
|
||||
|
||||
Unlike the E6400, this one does require a neutered Intel ME image to run. This
|
||||
means running it through `me_cleaner` before flashing; the Libreboot build
|
||||
system does this automatically, during build, or you can insert a neutered
|
||||
ROM image using the vendor scripts, see guide:
|
||||
|
||||
[Insert vendor files](../install/ivy_has_common.md)
|
||||
|
||||
As with the E6400, this one is flashable in software, from Dell UEFI firmware
|
||||
to Libreboot. Please refer to the installation instructions.
|
||||
|
||||
**To install Libreboot, see: [E6530 installation
|
||||
instructions](../install/e6430.md)**
|
||||
|
|
@ -0,0 +1,104 @@
|
|||
---
|
||||
title: Gigabyte GA-G41M-ES2L desktop board
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
GA-G41M-ES2L
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Gigabyte |
|
||||
| **Name** | GA-G41M-ES2L |
|
||||
| **Released** | 2009 |
|
||||
| **Chipset** | Intel G41 |
|
||||
| **CPU** | Intel Core 2 Extreme/Quad/Duo,
|
||||
Pentium Extreme/D/4 Extreme/4/Celeron |
|
||||
| **Graphics** | Integrated |
|
||||
| **Display** | None. |
|
||||
| **Memory** | Up to 16GB |
|
||||
| **Architecture** | x86_64 |
|
||||
| **Original boot firmware** | AWARD BIOS |
|
||||
| **Intel ME/AMD PSP** | Present. Can be disabled |
|
||||
| **Flash chip** | 2x8Mbit |
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|----------------|---------------------------------------|
|
||||
| **Internal flashing with original boot firmware** | W+ |
|
||||
| **Display** | - |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | P+ |
|
||||
| **External output** | P+ |
|
||||
| **Display brightness** | - |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-------|
|
||||
| **GRUB** | Slow! |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
This is a desktop board using intel hardware (circa \~2009, ICH7
|
||||
southbridge, similar performance-wise to the ThinkPad X200. It can make
|
||||
for quite a nifty desktop. Powered by libreboot.
|
||||
|
||||
As of Libreboot release 20221214, only SeaBIOS payload is provided in ROMs
|
||||
for this board. According to user reports, they work quite well. GRUB was
|
||||
always buggy on this board, so it was removed from lbmk.
|
||||
|
||||
IDE on the board is untested, but it might be possible to use a SATA HDD
|
||||
using an IDE SATA adapter. The SATA ports do work, but it's IDE emulation. The
|
||||
emulation is slow in DMA mode sia SeaBIOS, so SeaBIOS is configured to use PIO
|
||||
mode on this board. This SeaBIOS configuration does not affect the Linux kernel.
|
||||
|
||||
You need to set a custom MAC address in Linux for the NIC to work.
|
||||
In /etc/network/interfaces on debian-based systems like Debian or
|
||||
Devuan, this would be in the entry for your NIC:\
|
||||
hwaddress ether macaddressgoeshere
|
||||
|
||||
Alternatively:
|
||||
|
||||
cbfstool libreboot.rom extract -n rt8168-macaddress -f rt8168-macaddress
|
||||
|
||||
Modify the MAC address in the file `rt8168-macaddress` and then:
|
||||
|
||||
cbfstool libreboot.rom remove -n rt8168-macaddress
|
||||
cbfstool libreboot.rom add -f rt8168-macaddress -n rt8168-macaddress -t raw
|
||||
|
||||
Now you have a different MAC address hardcoded. In the above example, the ROM
|
||||
image is named `libreboot.rom` for your board. You can find cbfstool
|
||||
under `cbutils/` after running the following command
|
||||
in the build system:
|
||||
|
||||
./update trees -b coreboot utils
|
||||
|
||||
You can learn more about using the build system, lbmk, here:\
|
||||
[libreboot build instructions](../build/)
|
||||
|
||||
Flashing instructions can be found at
|
||||
[../install/](../install/)
|
||||
|
||||
RAM
|
||||
---
|
||||
|
||||
**This board is very picky with RAM. If it doesn't boot, try an EHCI debug
|
||||
dongle, serial usb adapter and null modem cable, or spkmodem, to get a
|
||||
coreboot log to see if it passed raminit.**
|
||||
|
||||
Kingston 8 GiB Kit KVR800D2N6/8G with Elpida Chips E2108ABSE-8G-E
|
||||
|
||||
this is a 2x4GB setup and these work quite well, according to a user on IRC.
|
||||
|
||||
Nanya NT2GT64U8HD0BY-AD with 2 GiB of NT5TU128M8DE-AD chips works too.
|
||||
|
||||
Many other modules will probably work just fine, but raminit is very picky on
|
||||
this board. Your mileage *will* fluctuate, wildly.
|
||||
|
|
@ -72,7 +72,7 @@ Build ROM image from source
|
|||
|
||||
The build target, when building from source, is thus:
|
||||
|
||||
./mk -b coreboot hp2170p_16mb
|
||||
./build roms hp2170p_16mb
|
||||
|
||||
Installation
|
||||
============
|
||||
|
|
@ -35,20 +35,41 @@ OR YOU MIGHT BRICK YOUR MACHINE: [SAFETY PRECAUTIONS](../../news/safety.md)**
|
|||
</div>
|
||||
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
Libreboot has support for this, in the Git repository and release versions
|
||||
from Libreboot 20230423 onwards.
|
||||
|
||||
Brief board info
|
||||
================
|
||||
----------------
|
||||
|
||||
HP EliteBook 2560p is a 12.5" laptop you can read more about here:
|
||||
|
||||
<https://support.hp.com/us-en/product/hp-elitebook-2560p-notebook-pc/5071201>
|
||||
|
||||
Installation of Libreboot
|
||||
=========================
|
||||
-------------------------
|
||||
|
||||
Coreboot also has some information:
|
||||
You can actually just compile the Libreboot ROM for this, and flash the
|
||||
entire ROM, then flash it. The *coreboot* project proper, has information
|
||||
about this:
|
||||
|
||||
<https://doc.coreboot.org/mainboard/hp/2560p.html#programming>
|
||||
|
||||
Refer to the coreboot guide for flashing instructions, and you can build the
|
||||
images for it in Libreboot like so:
|
||||
|
||||
./build roms hp2560p_8mb
|
||||
|
||||
More information about building ROM images can be found in
|
||||
the [build guide](../build/).
|
||||
|
||||
This is a *Sandybridge* board which means that a neutered ME image is required
|
||||
if you wish to flash the ME region. Libreboot's build system automatically
|
||||
downloads, neuters (using `me_cleaner`) and inserts this if compiling from
|
||||
source.
|
||||
|
||||
If you're using *Libreboot release* ROM images, the ME image has been scrubbed
|
||||
and you must re-insert it. Use the information on this guide to know how
|
||||
to do that:
|
||||
|
|
@ -56,7 +77,9 @@ to do that:
|
|||
[Insert vendor files on Intel Sandybridge/Ivybridge/Haswell
|
||||
platforms](../install/ivy_has_common.md)
|
||||
|
||||
Make sure to set the MAC address in the flash:
|
||||
You may also wish to change the *default MAC address* if you're planning to
|
||||
use the onboard Intel Gigabit Ethernet. You can do this using the information
|
||||
in the same guide linked above, or read the nvmutil manual:
|
||||
|
||||
[Modify MAC addresses with nvmutil](../install/nvmutil.md).
|
||||
|
||||
Refer to the [Libreboot flashing guides](../install/spi.md)
|
||||
|
|
@ -0,0 +1,128 @@
|
|||
---
|
||||
title: HP EliteBook 2570p
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
**[PLEASE READ THESE INSTRUCTIONS BEFORE INSTALLING](../../news/safety.md),
|
||||
OR YOU MIGHT BRICK YOUR MACHINE: [SAFETY PRECAUTIONS](../../news/safety.md)**
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
HP EliteBook 2570p
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|---------------------------|-----------------------------------|
|
||||
| **Manufacturer** | HP |
|
||||
| **Name** | EliteBook 2570p |
|
||||
| **Released** | 2012 |
|
||||
| **Chipset** | Intel QM77 |
|
||||
| **CPU** | Intel Ivy Bridge, socketed |
|
||||
| **Graphics** | Intel HD Graphics |
|
||||
| **Display** | 12.5" 1366x768 |
|
||||
| **Memory** | Up to 16GB (2x8GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | KBC1126, proprietary |
|
||||
| **Intel ME/AMD PSP** | Present, neutered |
|
||||
| **Flash chip** | SOIC-16 16MiB |
|
||||
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
Libreboot has support for this, in the Git repository and release versions
|
||||
after (but not including) 20230423.
|
||||
|
||||
Brief board info
|
||||
----------------
|
||||
|
||||
HP EliteBook 2570p is a 12.5" laptop very similar to the 2560p.
|
||||
The only real difference seems to be that this shipped with Ivy Bridge
|
||||
processors rather than Sandy Bridge, and has an USB 3.0 port.
|
||||
|
||||
You can read more specifications directly from HP:
|
||||
|
||||
<https://support.hp.com/us-en/document/c03412731>
|
||||
|
||||
The following is tested and confirmed working
|
||||
thanks to `Johan Ehnberg (johan@molnix.com)`:
|
||||
|
||||
- Native raminit with 2+2 (matched or unmatched), 2+8 or 8+8 GiB RAM
|
||||
- SeaBIOS and GRUB (booted Devuan and Ubuntu) (corebootfb+txtmode)
|
||||
- S3 suspend to RAM
|
||||
- Backlight control
|
||||
- 2.5" SATA SSD
|
||||
- Optical drive slot
|
||||
- Gigabit Ethernet
|
||||
- Mini-PCIe Wi-Fi
|
||||
- SD card reader
|
||||
- Bluetooth
|
||||
- Touchpad
|
||||
- Headphone jack, speakers and microphone
|
||||
- Webcam
|
||||
- Docking station: all ports except that weird extension port tested,
|
||||
hotplug and unplug work
|
||||
- VGA & DisplayPort
|
||||
- Fn combos, mute button
|
||||
- "Launch browser" button: worked one day, not other.
|
||||
Probably just not configured in OS.
|
||||
|
||||
These were visible on lsusb, but no further tests were performed:
|
||||
|
||||
- Fingerprint sensor
|
||||
- Smart card reader
|
||||
- WWAN (3G modem)
|
||||
|
||||
Untested:
|
||||
|
||||
- Trackpoint (not present on cheap aftermarket keyboard tested)
|
||||
- ExpressCard
|
||||
- eSATA & mSATA (believed to work based on coreboot comments)
|
||||
|
||||
Not working:
|
||||
|
||||
- Radio button
|
||||
|
||||
Installation of Libreboot
|
||||
-------------------------
|
||||
|
||||
You can actually just compile the Libreboot ROM for this, and flash the
|
||||
entire ROM. The process is the same as 2560p, except you probably have
|
||||
a SOIC-16 chip instead of SOIC-8. Follow these instructions:
|
||||
|
||||
<https://doc.coreboot.org/mainboard/hp/2560p.html#programming>
|
||||
|
||||
Refer to that coreboot guide for flashing instructions, and you can
|
||||
build the images for it in Libreboot like so:
|
||||
|
||||
./build roms hp2570p_16mb
|
||||
|
||||
More information about building ROM images can be found in
|
||||
the [build guide](../build/).
|
||||
|
||||
This is an *Ivy Bridge* board which means that a neutered ME image is required
|
||||
if you wish to flash the ME region. Libreboot's build system automatically
|
||||
downloads, neuters (using `me_cleaner`) and inserts this if compiling from
|
||||
source.
|
||||
|
||||
If you're using *Libreboot release* ROM images, the ME image has been scrubbed
|
||||
and you must re-insert it. Use the information on this guide to know how
|
||||
to do that:
|
||||
|
||||
[Insert vendor files on Intel Sandybridge/Ivybridge/Haswell
|
||||
platforms](../install/ivy_has_common.md)
|
||||
|
||||
You may also wish to change the *default MAC address* if you're planning to
|
||||
use the onboard Intel Gigabit Ethernet. You can do this using the information
|
||||
in the same guide linked above, or read the nvmutil manual:
|
||||
|
||||
[Modify MAC addresses with nvmutil](../install/nvmutil.md).
|
||||
|
||||
|
|
@ -49,14 +49,6 @@ P*: Partially works with blobs
|
|||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
|
||||
Disable security before flashing
|
||||
================================
|
||||
|
||||
Before internal flashing, you must first disable `/dev/mem` protections. Make
|
||||
sure to re-enable them after you're finished.
|
||||
|
||||
See: [Disabling /dev/mem protection](../install/devmem.md)
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
|
|
@ -96,7 +88,7 @@ to recover from an unbootable BIOS:
|
|||
|
||||
You can build the images for it in Libreboot like so:
|
||||
|
||||
./mk -b coreboot hp8200sff_8mb
|
||||
./build roms hp8200sff_8mb
|
||||
|
||||
More information about building ROM images can be found in
|
||||
the [build guide](../build/).
|
||||
|
|
@ -146,6 +138,10 @@ between the pins until you can see the normal BIOS boot screen.
|
|||
|
||||

|
||||
|
||||
Boot into an OS supported by flashprog. On Linux, make sure you add the
|
||||
kernel parameter **iomem=relaxed** which disables memory protections that
|
||||
prevent BIOS flashing.
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
||||
|
|
@ -158,7 +154,7 @@ Pin-Strap is set". If it doesn't, start again from the beginning.
|
|||
|
||||
Now build the **4** MiB Libreboot image.
|
||||
|
||||
./mk -b coreboot hp8200sff_4mb
|
||||
./build roms hp8200sff_4mb
|
||||
|
||||
More information about building ROM images can be found in
|
||||
the [build guide](../build/).
|
||||
|
|
@ -183,7 +179,7 @@ Power off the computer. Make sure to power off, rebooting is not enough!
|
|||
|
||||
Power on the computer.
|
||||
Now we can flash the full 8 MiB image. Boot to an OS with flashprog
|
||||
again.
|
||||
again. On linux, remember the **iomem=relaxed** kernel parameter.
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
|
@ -0,0 +1,339 @@
|
|||
---
|
||||
title: HP EliteBook 820 G2
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
**[PLEASE READ THESE INSTRUCTIONS BEFORE INSTALLING](../../news/safety.md),
|
||||
OR YOU MIGHT BRICK YOUR MACHINE: [SAFETY PRECAUTIONS](../../news/safety.md)**
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
<img tabindex=1 alt="HP EliteBook 820 G2" class="p" src="https://av.libreboot.org/hp820g2/hp820g2.jpg" /><span class="f"><img src="https://av.libreboot.org/hp820g2/hp820g2.jpg" /></span>
|
||||
<img tabindex=1 alt="HP EliteBook 820 G2" class="p" src="https://av.libreboot.org/hp820g2/hp820g2_lid.jpg" /><span class="f"><img src="https://av.libreboot.org/hp820g2/hp820g2_lid.jpg" /></span>
|
||||
<br/>
|
||||
<img tabindex=1 alt="HP EliteBook 820 G2" class="p" src="https://av.libreboot.org/hp820g2/hp820g2_ports1.jpg" /><span class="f"><img src="https://av.libreboot.org/hp820g2/hp820g2_ports1.jpg" /></span>
|
||||
<img tabindex=1 alt="HP EliteBook 820 G2" class="p" src="https://av.libreboot.org/hp820g2/hp820g2_ports2.jpg" /><span class="f"><img src="https://av.libreboot.org/hp820g2/hp820g2_ports2.jpg" /></span>
|
||||
<br/>
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | HP |
|
||||
| **Name** | EliteBook 820 G2 |
|
||||
| **Variants** | EliteBook 820 G2 |
|
||||
| **Released** | 2014 |
|
||||
| **Chipset** | 5th gen (Broadwell, SoC) |
|
||||
| **CPU** | Intel i5-5200U, i5-5300U, i7-5500U, i7-5600U |
|
||||
| **Graphics** | Intel HD 5500 graphics (libre initialisation) |
|
||||
| **Display** | 14" 1366x768 or 1920x1080 TFT |
|
||||
| **Memory** | Two slots, max 16GB/slot (32GB), DDR3/SODIMM |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | SMSC MEC1324 in main boot flash |
|
||||
| **Original boot firmware** | HP UEFI firmware |
|
||||
| **Intel ME/AMD PSP** | Present. Can be disabled with me_cleaner. |
|
||||
| **Flash chip** | SOIC-8 16MiB 128Mbit, 12MiB usable by coreboot |
|
||||
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|---------------------------------------------------|----|
|
||||
| **Internal flashing with original boot firmware** | N |
|
||||
| **Display (if Intel GPU)** | W+ |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | W+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
|
||||
Full hardware specifications can be found on HP's own website:
|
||||
|
||||
<https://support.hp.com/gb-en/document/c04543492>
|
||||
|
||||
Libreboot pre-installed
|
||||
=======================
|
||||
|
||||
My company, Minifree Ltd, also sells this machine with Libreboot pre-installed.
|
||||
I use the profits from sales to fund my work. You can find the Libreboot 820
|
||||
here:
|
||||
|
||||
<https://minifree.org/product/libreboot-820/>
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
**Unavailable in Libreboot 20231106 or earlier. You must [compile from
|
||||
source](../build/), or use a release newer than 20231106.**
|
||||
|
||||
This is a beastly 12.5" Broadwell machine from HP, the main benefit of which is
|
||||
greater power efficiency (compared to Ivybridge and Haswell platforms), while
|
||||
offering similar CPU performance but much higher graphics performance.
|
||||
|
||||
Variants exist with either Intel Core i5-5200U, i5-5300U, i7-5500U or
|
||||
i7-5600U and it comes with a plethora of ports; 3x USB 3.0, DisplayPort (which
|
||||
can do 4K 60Hz), a VGA port, can be expanded to 32GB RAM, has *3* slots which
|
||||
can take SSDs (PCIe, M2 and regular SATA), also has a side dock connector (for
|
||||
a docking station). The screen is eDP type and can be upgraded to 1920x1080.
|
||||
|
||||
This is a nice portable machine, with very reasonable performance. Most people
|
||||
should be very satisfied with it, in daily use. It is widely available in
|
||||
online market places. This page will tell you how to flash it!
|
||||
|
||||
All variants of this mainboard will come with Intel HD 5500 graphics, which has
|
||||
completely free software initialisation in coreboot, provided by *libgfxinit*.
|
||||
|
||||
Build ROM image from source
|
||||
---------------------------
|
||||
|
||||
First, install the build dependencies and initialise git, using the
|
||||
instructions in [building from source](../build/). Unless you're using a
|
||||
release after Libreboot 20231106, you *must* use the latest `lbmk.git`.
|
||||
|
||||
The build target, when building from source, is thus:
|
||||
|
||||
./build roms hp820g2_12mb
|
||||
|
||||
NOTE: The actual flash is 16MB, but you must flash only the first 12MB of it.
|
||||
The ROM images provided by Libreboot are 12MB.
|
||||
|
||||
There is a separate 2MB *system* flash that you must *erase*, prior to
|
||||
installing Libreboot. This, along with Libreboot's modified IFD, bypasses
|
||||
the security (HP Sure Start) that the vendor put there, allowing you to
|
||||
use coreboot-based firmware such as Libreboot.
|
||||
|
||||
Installation
|
||||
============
|
||||
|
||||
Insert binary files
|
||||
-------------------
|
||||
|
||||
If you're using a release ROM, please ensure that you've inserted extra firmware
|
||||
required refer to the [guide](../install/ivy_has_common.md) for that. (**failure
|
||||
to adhere to this advice will result in a bricked machine**)
|
||||
|
||||
If you're *building* from source (using lbmk), the steps takes above are done
|
||||
for you automatically, inserting all of the required files. The above link is
|
||||
only relevant for *release* images, which lack some of these files.
|
||||
|
||||
Set MAC address
|
||||
---------------
|
||||
|
||||
This platform uses an Intel Flash Descriptor, and defines an Intel GbE NVM
|
||||
region. As such, release/build ROMs will contain the same MAC address. To
|
||||
change the MAC address, please read [nvmutil documentation](../install/nvmutil.md).
|
||||
|
||||
Update an existing Libreboot installation
|
||||
-----------------
|
||||
|
||||
<img class="l" tabindex=1 alt="HP EliteBook 820 G2" class="p" src="https://av.libreboot.org/hp820g2/hp820g2_backlit.jpg" /><span class="f"><img src="https://av.libreboot.org/hp820g2/hp820g2_backlit.jpg" /></span>
|
||||
|
||||
NOTE: This section only applies if you haven't enabled write protection. You
|
||||
can otherwise use the external flashing instructions (see below) for both the
|
||||
initial installation and updates, but for updates you don't need to re-erase
|
||||
the private flash, if it was already erased.
|
||||
|
||||
If you're already running Libreboot, and you don't have flash protection
|
||||
turned on, [internal flashing](../install/) is possible, but please note:
|
||||
|
||||
You must *only* flash the first 12MB, and nothing in the final 4MB of the flash.
|
||||
This is because the EC firmware is in flash, and we don't touch that during
|
||||
initial installation or during updates.
|
||||
|
||||
Update it like so:
|
||||
|
||||
Create a dummy 16MB ROM like so:
|
||||
|
||||
```
|
||||
dd if=/dev/zero of=new.bin bs=16M count=1
|
||||
```
|
||||
|
||||
Then insert your 12MB Libreboot ROM image into the dummy file:
|
||||
|
||||
```
|
||||
dd if=libreboot.rom of=new.bin bs=12M count=1 conv=notrunc
|
||||
```
|
||||
|
||||
The `libreboot.rom` file is the 12MB image from Libreboot. The `new.bin`
|
||||
file is the Libreboot ROM, padded to 16MB. You will not flash the entire 16MB
|
||||
file, but flashprog detects a 16MB flash IC. This just makes flashrom not
|
||||
complain about mismatching ROM/chip size.
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
||||
You should flash each region individually:
|
||||
|
||||
```
|
||||
flashprog -p internal --ifd -i gbe -w new.bin --noverify-all
|
||||
flashprog -p internal --ifd -i bios -w new.bin --noverify-all
|
||||
flashprog -p internal --ifd -i me -w new.bin --noverify-all
|
||||
flashprog -p internal --ifd -i ifd -w new.bin --noverify-all
|
||||
```
|
||||
|
||||
NOTE: The `--ifd` option uses the regions defined in the *flashed* IFD, so
|
||||
they must match the ROM. You can otherwise dump a layout file and use that,
|
||||
using the instructions below (using `-l layout.txt` instead of `--ifd`).
|
||||
|
||||
NOTE: If you already did an installation before, and you don't want to
|
||||
[change the MAC address](../install/nvmutil.html) stored in the gbe region,
|
||||
you can skip the gbe/ifd/me regions as above, and flash just the BIOS region.
|
||||
|
||||
NOTE: Use of `--ifd` requires flashrom 1.2 or higher. If you have an older
|
||||
version, or you don't have `--ifd`, you could instead do:
|
||||
|
||||
```
|
||||
ifdtool -f layout.txt libreboot.rom
|
||||
```
|
||||
|
||||
Then, instead of `--ifd` you would use `-l layout.txt`.
|
||||
|
||||
ALSO: The `--ifd` option makes flashrom flash regions based on what's in
|
||||
the *current* flashed IFD.
|
||||
|
||||
Flashing Libreboot first time (hardware)
|
||||
========================================
|
||||
|
||||
**PLEASE ENSURE that you dump a copy of both flash ICs (system flash and
|
||||
private flash). Take two dumps of each, and make sure each has two good hashes.
|
||||
This is because there are certain files that, while you may not need for a
|
||||
regular Libreboot installation, may be useful for recovery purposes. You have
|
||||
been warned!**
|
||||
|
||||
This section is relevant to you if you're still running the original HP
|
||||
firmware. You must [flash externally](../install/spi.md).
|
||||
|
||||
Take stock of these further notes, because there are extra steps that you
|
||||
must take.
|
||||
|
||||
HP Sure Start
|
||||
-------------
|
||||
|
||||
There is a 16MB flash and a 2MB flash. Read this page for info:
|
||||
<https://doc.coreboot.org/mainboard/hp/hp_sure_start.html>
|
||||
|
||||
The page makes it seem more complicated than necessary, from a user's point
|
||||
of view. What you really need to do is just erase the 2MB flash IC, and flash
|
||||
only the first 12MB of the 16MB flash IC. A photo is shown below. Consult
|
||||
the [SPI flashing guide](../install/spi.md) and act as if you were flashing,
|
||||
but leave out `-w libreboot.rom` (don't write an image), and instead
|
||||
use the `--erase` option, with your clip connected to the private flash (2MB
|
||||
flash IC).
|
||||
|
||||
You might want to dump the private flash first, just in case (use `-r priv.rom`
|
||||
or whatever filename you want to dump to, and take two dumps, ensuring that
|
||||
the hashes match). The private (2MB) flash is inaccessible from your OS. The
|
||||
system stores hashes of the IFD, GbE and a copy of IFD/GbE in private flash,
|
||||
restoring them if they were modified, but erasing the private flash disables
|
||||
this security mechanism.
|
||||
|
||||
Here is a photo of the board, with the flashes:
|
||||
|
||||

|
||||
|
||||
HP bootblock
|
||||
------------
|
||||
|
||||
See: <https://doc.coreboot.org/mainboard/hp/elitebook_820_g2.html?highlight=elitebook>
|
||||
|
||||
In this page it talks about HP's own bootblock and EC firmware. These are in
|
||||
the final 4MB of the flash. You must *not* modify these, because you will brick
|
||||
your machine unless the IFD is modified;
|
||||
|
||||
This is why Libreboot provides 12MB images. The IFD in Libreboot is modified, as
|
||||
per this coreboot documentation, to make the BIOS region *end* at the last byte
|
||||
of the first 12MB in flash, bypassing HP's security entirely. In other words,
|
||||
you can run whatever you want (such as Libreboot) in the first 12MB of flash,
|
||||
so long as the upper 4MB is untouched and the private 2MB flash has been erased.
|
||||
|
||||
With Libreboot's modified IFD, HP's own bootblock is never executed, but the
|
||||
EC firmware *is*, and must be left alone. You do not to insert it in your
|
||||
Libreboot ROM because it's already in flash, within that last 4MB.
|
||||
|
||||
Flash a ROM image (hardware)
|
||||
-----------------
|
||||
|
||||
**REMOVE all power sources like battery, charger and so on, before doing this.
|
||||
This is to prevent short circuiting and power surges while flashing.**
|
||||
|
||||
For general information, please refer to [25xx NOR flash
|
||||
instructions](../install/spi.md).
|
||||
|
||||
Remove the bottom cover via the latch, and the flashes are accessible.
|
||||
First, dump both flashes for backup, using the `-r` option (instead of `-w`)
|
||||
in flashrom. Two dumps of each flash, make sure both dumps match for each chip.
|
||||
|
||||
We will assume that your system flash (16MB) dump is named `dump.bin`. This is
|
||||
the dump of your 16MB flash, containing HP's firmware, including the final
|
||||
bootblock and EC firmware.
|
||||
|
||||
This gives you everything, including the final 4MB. Now insert your new ROM
|
||||
into a copy of `dump.bin`:
|
||||
|
||||
```
|
||||
cp -R dump.bin new.bin
|
||||
dd if=libreboot.rom of=new.bin bs=12M count=1 conv=notrunc
|
||||
```
|
||||
|
||||
Flash `new.bin` to system flash (16MB IC) using the `-w` option in flashrom,
|
||||
and erase the private (2MB) flash IC,
|
||||
using the `--erase` option (instead of `-w filename.rom`) in flashrom.
|
||||
|
||||
In the above example, you replaced the first 12MB of the HP dump with that of
|
||||
your Libreboot image, but leaving the final 4MB intact which contains the EC
|
||||
firmware. Libreboot's custom IFD sets everything so that all regions, from
|
||||
IFD to GbE, ME and then BIOS region, exist within the first 12MB of flash.
|
||||
This makes the machine boot from the end of the 12MB section, containing the
|
||||
coreboot bootblock, instead of the HP bootblock (which is never executed but
|
||||
must remain intact).
|
||||
|
||||
It's very important that you *erase* the 2MB flash. Be careful *not* to
|
||||
erase the system (16MB flash). This is yet another reason why you should keep
|
||||
a backup of both flash ICs, just in case (dumped using `-r` in flashrom).
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
And that's all. Refer to other documents on Libreboot's website for how
|
||||
to handle Linux/BSD systems and generally use your machine.
|
||||
|
||||
TPM 2.0 potentially supported
|
||||
==============================
|
||||
|
||||
The onboard TPM is an SLB 9660, which supports TPM 1.2 but it is known to be
|
||||
compatible with TPM 2.0 via firmware upgrade. Although not yet tested, we have
|
||||
some notes about that here:
|
||||
|
||||
[../../tasks/#hp-820-g2-tpm](../../tasks/#hp-820-g2-tpm)
|
||||
|
||||
Not yet used meaningfully by Libreboot itself, but the TPM can be used to
|
||||
implement things like measured boot.
|
||||
|
||||
References
|
||||
==========
|
||||
|
||||
See: <https://doc.coreboot.org/soc/intel/broadwell/blobs.html>
|
||||
|
||||
Libreboot's build system automatically pulls down the MRC/refcode files, and
|
||||
modifies the refcode to enable the onboard Intel Gigabit Ethernet (GbE). You
|
||||
don't need to mess with this at all, when you build Libreboot yourself.
|
||||
|
||||
You can see how this works, by looking at the patch which added 820 G2 support:
|
||||
<https://browse.libreboot.org/lbmk.git/commit/?id=401c0882aaec059eab62b5ce467d3efbc1472d1f>
|
||||
|
||||
If you're using release builds, the MRC, refcode and (neutered) ME images are
|
||||
missing from flash, and must be re-inserted, using the instructions
|
||||
on [this page](../install/ivy_has_common.md).
|
||||
|
|
@ -24,14 +24,6 @@ OR YOU MIGHT BRICK YOUR MACHINE: [SAFETY PRECAUTIONS](../../news/safety.md)**
|
|||
| **Intel ME/AMD PSP** | Present, neutered |
|
||||
| **Flash chip** | SOIC-16 16MiB |
|
||||
|
||||
Disable security before flashing
|
||||
================================
|
||||
|
||||
Before internal flashing, you must first disable `/dev/mem` protections. Make
|
||||
sure to re-enable them after you're finished.
|
||||
|
||||
See: [Disabling /dev/mem protection](../install/devmem.md)
|
||||
|
||||
# Introduction
|
||||
|
||||
This is a small but powerful desktop using Sandy or Ivy Bridge CPUs
|
||||
|
|
@ -79,7 +71,8 @@ crystal (small metal cylinder) and the power cable for the optical drive.
|
|||
|
||||
|
||||
|
||||
Boot into an OS of your choice (that has flashprog support).
|
||||
Boot into an OS of your choice (that has flashprog support). When using Linux,
|
||||
you need to supply the kernel parameter `iomem=relaxed`.
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
|
@ -69,7 +69,7 @@ Build ROM image from source
|
|||
|
||||
The build target, when building from source, is thus:
|
||||
|
||||
./mk -b coreboot hp8460pintel_8mb
|
||||
./build roms hp8460pintel_8mb
|
||||
|
||||
Installation
|
||||
============
|
||||
|
|
@ -72,7 +72,7 @@ Build ROM image from source
|
|||
|
||||
The build target, when building from source, is thus:
|
||||
|
||||
./mk -b coreboot hp8470pintel_16mb
|
||||
./build roms hp8470pintel_16mb
|
||||
|
||||
Installation
|
||||
============
|
||||
|
|
@ -62,8 +62,6 @@ source](../build/), or use a release newer than 20240126.**
|
|||
|
||||
This is a beastly 15" Sandy Bridge mobile workstation from HP.
|
||||
|
||||
**Wi-Fi does not work. It shows correctly in lspci, but stays hard blocked.**
|
||||
|
||||
GPU
|
||||
---
|
||||
|
||||
|
|
@ -94,7 +92,7 @@ Build ROM image from source
|
|||
|
||||
The build target, when building from source, is thus:
|
||||
|
||||
./mk -b coreboot hp8560w_8mb
|
||||
./build roms hp8560w_8mb
|
||||
|
||||
Installation
|
||||
============
|
||||
|
|
@ -47,7 +47,7 @@ Installation of Libreboot
|
|||
|
||||
You must first compile the Libreboot ROM
|
||||
|
||||
./mk -b coreboot hp9470m_16mb
|
||||
./build roms hp9470m_16mb
|
||||
|
||||
More information about building ROM images can be found in
|
||||
the [build guide](../build).
|
||||
|
|
@ -0,0 +1,24 @@
|
|||
# biosdecode 2.12
|
||||
VPD present.
|
||||
BIOS Build ID: 6DET65WW
|
||||
Box Serial Number: L3AAR0B
|
||||
Motherboard Serial Number: 1ZFDS89N4DD
|
||||
Machine Type/Model: 7459GW4
|
||||
SMBIOS 2.4 present.
|
||||
Structure Table Length: 2464 bytes
|
||||
Structure Table Address: 0x000E0010
|
||||
Number Of Structures: 68
|
||||
Maximum Structure Size: 120 bytes
|
||||
BIOS32 Service Directory present.
|
||||
Revision: 0
|
||||
Calling Interface Address: 0x000FDC80
|
||||
ACPI 2.0 present.
|
||||
OEM Identifier: LENOVO
|
||||
RSD Table 32-bit Address: 0x79B5B843
|
||||
XSD Table 64-bit Address: 0x0000000079B5B8AB
|
||||
PNP BIOS 1.0 present.
|
||||
Event Notification: Not Supported
|
||||
Real Mode 16-bit Code Address: E2CA:1868
|
||||
Real Mode 16-bit Data Address: 0040:0000
|
||||
16-bit Protected Mode Code Address: 0x000F97BD
|
||||
16-bit Protected Mode Data Address: 0x00000400
|
||||
|
|
@ -0,0 +1,208 @@
|
|||
Codec: Conexant CX20561 (Hermosa)
|
||||
Address: 0
|
||||
AFG Function Id: 0x1 (unsol 1)
|
||||
MFG Function Id: 0x2 (unsol 1)
|
||||
Vendor Id: 0x14f15051
|
||||
Subsystem Id: 0x17aa20ff
|
||||
Revision Id: 0x100000
|
||||
Modem Function Group: 0x2
|
||||
Default PCM:
|
||||
rates [0x160]: 44100 48000 96000
|
||||
bits [0xe]: 16 20 24
|
||||
formats [0x1]: PCM
|
||||
Default Amp-In caps: N/A
|
||||
Default Amp-Out caps: N/A
|
||||
State of AFG node 0x01:
|
||||
Power states: D0 D1 D2 D3 CLKSTOP
|
||||
Power: setting=D0, actual=D0
|
||||
GPIO: io=4, o=0, i=0, unsolicited=1, wake=0
|
||||
IO[0]: enable=0, dir=0, wake=0, sticky=0, data=0, unsol=0
|
||||
IO[1]: enable=0, dir=0, wake=0, sticky=0, data=0, unsol=0
|
||||
IO[2]: enable=0, dir=0, wake=0, sticky=0, data=0, unsol=0
|
||||
IO[3]: enable=0, dir=0, wake=0, sticky=0, data=0, unsol=0
|
||||
Node 0x10 [Audio Output] wcaps 0xc1d: Stereo Amp-Out R/L
|
||||
Control: name="Speaker Playback Volume", index=0, device=0
|
||||
ControlAmp: chs=3, dir=Out, idx=0, ofs=0
|
||||
Control: name="Speaker Playback Switch", index=0, device=0
|
||||
ControlAmp: chs=3, dir=Out, idx=0, ofs=0
|
||||
Device: name="CX20561 Analog", type="Audio", device=0
|
||||
Amp-Out caps: ofs=0x4a, nsteps=0x4a, stepsize=0x03, mute=0
|
||||
Amp-Out vals: [0x4a 0x4a]
|
||||
Converter: stream=8, channel=0
|
||||
PCM:
|
||||
rates [0x560]: 44100 48000 96000 192000
|
||||
bits [0xe]: 16 20 24
|
||||
formats [0x1]: PCM
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Node 0x11 [Audio Output] wcaps 0xc1d: Stereo Amp-Out R/L
|
||||
Control: name="Headphone Playback Volume", index=0, device=0
|
||||
ControlAmp: chs=3, dir=Out, idx=0, ofs=0
|
||||
Control: name="Headphone Playback Switch", index=0, device=0
|
||||
ControlAmp: chs=3, dir=Out, idx=0, ofs=0
|
||||
Amp-Out caps: ofs=0x4a, nsteps=0x4a, stepsize=0x03, mute=0
|
||||
Amp-Out vals: [0x4a 0x4a]
|
||||
Converter: stream=8, channel=0
|
||||
PCM:
|
||||
rates [0x560]: 44100 48000 96000 192000
|
||||
bits [0xe]: 16 20 24
|
||||
formats [0x1]: PCM
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Node 0x12 [Audio Output] wcaps 0x211: Stereo Digital
|
||||
Control: name="IEC958 Playback Con Mask", index=0, device=0
|
||||
Control: name="IEC958 Playback Pro Mask", index=0, device=0
|
||||
Control: name="IEC958 Playback Default", index=0, device=0
|
||||
Control: name="IEC958 Playback Switch", index=0, device=0
|
||||
Control: name="IEC958 Default PCM Playback Switch", index=0, device=0
|
||||
Device: name="CX20561 Digital", type="SPDIF", device=1
|
||||
Converter: stream=8, channel=0
|
||||
Digital:
|
||||
Digital category: 0x0
|
||||
IEC Coding Type: 0x0
|
||||
PCM:
|
||||
rates [0x160]: 44100 48000 96000
|
||||
bits [0xe]: 16 20 24
|
||||
formats [0x5]: PCM AC3
|
||||
Node 0x13 [Beep Generator Widget] wcaps 0x70000c: Mono Amp-Out
|
||||
Control: name="Beep Playback Volume", index=0, device=0
|
||||
ControlAmp: chs=1, dir=Out, idx=0, ofs=0
|
||||
Control: name="Beep Playback Switch", index=0, device=0
|
||||
ControlAmp: chs=1, dir=Out, idx=0, ofs=0
|
||||
Amp-Out caps: ofs=0x03, nsteps=0x03, stepsize=0x17, mute=0
|
||||
Amp-Out vals: [0x00]
|
||||
Node 0x14 [Audio Input] wcaps 0x100d1b: Stereo Amp-In R/L
|
||||
Device: name="CX20561 Analog", type="Audio", device=0
|
||||
Amp-In caps: ofs=0x4a, nsteps=0x50, stepsize=0x03, mute=0
|
||||
Amp-In vals: [0x50 0x50] [0x50 0x50]
|
||||
Converter: stream=4, channel=0
|
||||
SDI-Select: 0
|
||||
PCM:
|
||||
rates [0x160]: 44100 48000 96000
|
||||
bits [0xe]: 16 20 24
|
||||
formats [0x1]: PCM
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Connection: 2
|
||||
0x1d* 0x17
|
||||
Node 0x15 [Audio Input] wcaps 0x100d1b: Stereo Amp-In R/L
|
||||
Control: name="Capture Volume", index=0, device=0
|
||||
ControlAmp: chs=3, dir=In, idx=1, ofs=0
|
||||
Amp-In caps: ofs=0x4a, nsteps=0x50, stepsize=0x03, mute=0
|
||||
Amp-In vals: [0x50 0x50]
|
||||
Converter: stream=0, channel=0
|
||||
SDI-Select: 0
|
||||
PCM:
|
||||
rates [0x160]: 44100 48000 96000
|
||||
bits [0xe]: 16 20 24
|
||||
formats [0x1]: PCM
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Connection: 1
|
||||
0x18
|
||||
Node 0x16 [Pin Complex] wcaps 0x400581: Stereo
|
||||
Control: name="Headphone Jack", index=0, device=0
|
||||
Pincap 0x0000001c: OUT HP Detect
|
||||
Pin Default 0x042140f0: [Jack] HP Out at Ext Right
|
||||
Conn = 1/8, Color = Green
|
||||
DefAssociation = 0xf, Sequence = 0x0
|
||||
Pin-ctls: 0xc0: OUT HP
|
||||
Unsolicited: tag=02, enabled=1
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Connection: 2
|
||||
0x10 0x11*
|
||||
Node 0x17 [Pin Complex] wcaps 0x40048b: Stereo Amp-In
|
||||
Control: name="Dock Mic Boost Volume", index=0, device=0
|
||||
ControlAmp: chs=3, dir=In, idx=0, ofs=0
|
||||
Control: name="Dock Mic Jack", index=0, device=0
|
||||
Amp-In caps: ofs=0x00, nsteps=0x04, stepsize=0x27, mute=0
|
||||
Amp-In vals: [0x00 0x00]
|
||||
Pincap 0x00001224: IN Detect
|
||||
Vref caps: 50 80
|
||||
Pin Default 0x61a190f0: [N/A] Mic at Sep Rear
|
||||
Conn = 1/8, Color = Pink
|
||||
DefAssociation = 0xf, Sequence = 0x0
|
||||
Pin-ctls: 0x24: IN VREF_80
|
||||
Unsolicited: tag=03, enabled=1
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Node 0x18 [Pin Complex] wcaps 0x40048b: Stereo Amp-In
|
||||
Control: name="Mic Boost Volume", index=0, device=0
|
||||
ControlAmp: chs=3, dir=In, idx=0, ofs=0
|
||||
Control: name="Mic Jack", index=0, device=0
|
||||
Amp-In caps: ofs=0x00, nsteps=0x04, stepsize=0x27, mute=0
|
||||
Amp-In vals: [0x00 0x00]
|
||||
Pincap 0x00001224: IN Detect
|
||||
Vref caps: 50 80
|
||||
Pin Default 0x04a190f0: [Jack] Mic at Ext Right
|
||||
Conn = 1/8, Color = Pink
|
||||
DefAssociation = 0xf, Sequence = 0x0
|
||||
Pin-ctls: 0x24: IN VREF_80
|
||||
Unsolicited: tag=04, enabled=1
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Node 0x19 [Pin Complex] wcaps 0x400581: Stereo
|
||||
Control: name="Dock Headphone Jack", index=0, device=0
|
||||
Pincap 0x00000014: OUT Detect
|
||||
Pin Default 0x612140f0: [N/A] HP Out at Sep Rear
|
||||
Conn = 1/8, Color = Green
|
||||
DefAssociation = 0xf, Sequence = 0x0
|
||||
Pin-ctls: 0x40: OUT
|
||||
Unsolicited: tag=01, enabled=1
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Connection: 2
|
||||
0x10 0x11*
|
||||
Node 0x1a [Pin Complex] wcaps 0x400501: Stereo
|
||||
Control: name="Speaker Phantom Jack", index=0, device=0
|
||||
Pincap 0x00010010: OUT EAPD
|
||||
EAPD 0x2: EAPD
|
||||
Pin Default 0x901701f0: [Fixed] Speaker at Int N/A
|
||||
Conn = Analog, Color = Unknown
|
||||
DefAssociation = 0xf, Sequence = 0x0
|
||||
Misc = NO_PRESENCE
|
||||
Pin-ctls: 0x40: OUT
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Connection: 2
|
||||
0x10* 0x11
|
||||
Node 0x1b [Pin Complex] wcaps 0x400500: Mono
|
||||
Pincap 0x00010010: OUT EAPD
|
||||
EAPD 0x2: EAPD
|
||||
Pin Default 0x40f001f0: [N/A] Other at Ext N/A
|
||||
Conn = Unknown, Color = Unknown
|
||||
DefAssociation = 0xf, Sequence = 0x0
|
||||
Misc = NO_PRESENCE
|
||||
Pin-ctls: 0x40: OUT
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Connection: 2
|
||||
0x10* 0x11
|
||||
Node 0x1c [Pin Complex] wcaps 0x400701: Stereo Digital
|
||||
Control: name="SPDIF Phantom Jack", index=0, device=0
|
||||
Pincap 0x00000010: OUT
|
||||
Pin Default 0x40f001f0: [N/A] Other at Ext N/A
|
||||
Conn = Unknown, Color = Unknown
|
||||
DefAssociation = 0xf, Sequence = 0x0
|
||||
Misc = NO_PRESENCE
|
||||
Pin-ctls: 0x40: OUT
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Connection: 1
|
||||
0x12
|
||||
Node 0x1d [Pin Complex] wcaps 0x40040b: Stereo Amp-In
|
||||
Control: name="Internal Mic Boost Volume", index=0, device=0
|
||||
ControlAmp: chs=3, dir=In, idx=0, ofs=0
|
||||
Control: name="Internal Mic Phantom Jack", index=0, device=0
|
||||
Amp-In caps: ofs=0x00, nsteps=0x04, stepsize=0x2f, mute=0
|
||||
Amp-In vals: [0x00 0x00]
|
||||
Pincap 0x00000020: IN
|
||||
Pin Default 0x90a601f0: [Fixed] Mic at Int N/A
|
||||
Conn = Digital, Color = Unknown
|
||||
DefAssociation = 0xf, Sequence = 0x0
|
||||
Misc = NO_PRESENCE
|
||||
Pin-ctls: 0x20: IN
|
||||
Power states: D0 D1 D2 D3
|
||||
Power: setting=D0, actual=D0
|
||||
Node 0x1e [Vendor Defined Widget] wcaps 0xf00000: Mono
|
||||
|
|
@ -0,0 +1,52 @@
|
|||
processor : 0
|
||||
vendor_id : GenuineIntel
|
||||
cpu family : 6
|
||||
model : 23
|
||||
model name : Intel(R) Core(TM)2 Duo CPU P8600 @ 2.40GHz
|
||||
stepping : 6
|
||||
microcode : 0x60c
|
||||
cpu MHz : 800.000
|
||||
cache size : 3072 KB
|
||||
physical id : 0
|
||||
siblings : 2
|
||||
core id : 0
|
||||
cpu cores : 2
|
||||
apicid : 0
|
||||
initial apicid : 0
|
||||
fpu : yes
|
||||
fpu_exception : yes
|
||||
cpuid level : 10
|
||||
wp : yes
|
||||
flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss ht tm pbe syscall nx lm constant_tsc arch_perfmon pebs bts nopl aperfmperf pni dtes64 monitor ds_cpl vmx smx est tm2 ssse3 cx16 xtpr pdcm sse4_1 lahf_lm dtherm tpr_shadow vnmi flexpriority
|
||||
bogomips : 4787.97
|
||||
clflush size : 64
|
||||
cache_alignment : 64
|
||||
address sizes : 36 bits physical, 48 bits virtual
|
||||
power management:
|
||||
|
||||
processor : 1
|
||||
vendor_id : GenuineIntel
|
||||
cpu family : 6
|
||||
model : 23
|
||||
model name : Intel(R) Core(TM)2 Duo CPU P8600 @ 2.40GHz
|
||||
stepping : 6
|
||||
microcode : 0x60c
|
||||
cpu MHz : 1600.000
|
||||
cache size : 3072 KB
|
||||
physical id : 0
|
||||
siblings : 2
|
||||
core id : 1
|
||||
cpu cores : 2
|
||||
apicid : 1
|
||||
initial apicid : 1
|
||||
fpu : yes
|
||||
fpu_exception : yes
|
||||
cpuid level : 10
|
||||
wp : yes
|
||||
flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss ht tm pbe syscall nx lm constant_tsc arch_perfmon pebs bts nopl aperfmperf pni dtes64 monitor ds_cpl vmx smx est tm2 ssse3 cx16 xtpr pdcm sse4_1 lahf_lm dtherm tpr_shadow vnmi flexpriority
|
||||
bogomips : 4787.97
|
||||
clflush size : 64
|
||||
cache_alignment : 64
|
||||
address sizes : 36 bits physical, 48 bits virtual
|
||||
power management:
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
|
|
@ -0,0 +1,587 @@
|
|||
# dmidecode 2.12
|
||||
SMBIOS 2.4 present.
|
||||
68 structures occupying 2464 bytes.
|
||||
Table at 0x000E0010.
|
||||
|
||||
Handle 0x0000, DMI type 0, 24 bytes
|
||||
BIOS Information
|
||||
Vendor: LENOVO
|
||||
Version: 6DET65WW (3.15 )
|
||||
Release Date: 08/24/2010
|
||||
Address: 0xE0000
|
||||
Runtime Size: 128 kB
|
||||
ROM Size: 8192 kB
|
||||
Characteristics:
|
||||
PCI is supported
|
||||
PC Card (PCMCIA) is supported
|
||||
PNP is supported
|
||||
BIOS is upgradeable
|
||||
BIOS shadowing is allowed
|
||||
ESCD support is available
|
||||
Boot from CD is supported
|
||||
Selectable boot is supported
|
||||
BIOS ROM is socketed
|
||||
EDD is supported
|
||||
ACPI is supported
|
||||
USB legacy is supported
|
||||
BIOS boot specification is supported
|
||||
Targeted content distribution is supported
|
||||
BIOS Revision: 3.21
|
||||
Firmware Revision: 1.6
|
||||
|
||||
Handle 0x0001, DMI type 1, 27 bytes
|
||||
System Information
|
||||
Manufacturer: LENOVO
|
||||
Product Name: 7459GW4
|
||||
Version: ThinkPad X200
|
||||
Serial Number: L3AAR0B
|
||||
UUID: 93861E01-4A15-11CB-8F2C-D4BC407E0839
|
||||
Wake-up Type: Power Switch
|
||||
SKU Number: Not Specified
|
||||
Family: ThinkPad X200
|
||||
|
||||
Handle 0x0002, DMI type 2, 8 bytes
|
||||
Base Board Information
|
||||
Manufacturer: LENOVO
|
||||
Product Name: 7459GW4
|
||||
Version: Not Available
|
||||
Serial Number: 1ZFDS89N4DD
|
||||
|
||||
Handle 0x0003, DMI type 3, 13 bytes
|
||||
Chassis Information
|
||||
Manufacturer: LENOVO
|
||||
Type: Notebook
|
||||
Lock: Not Present
|
||||
Version: Not Available
|
||||
Serial Number: Not Available
|
||||
Asset Tag: 1S7459GW4L3AAR0B
|
||||
Boot-up State: Unknown
|
||||
Power Supply State: Unknown
|
||||
Thermal State: Unknown
|
||||
Security Status: Unknown
|
||||
|
||||
Handle 0x0004, DMI type 126, 13 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x0005, DMI type 126, 13 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x0006, DMI type 4, 35 bytes
|
||||
Processor Information
|
||||
Socket Designation: None
|
||||
Type: Central Processor
|
||||
Family: Other
|
||||
Manufacturer: GenuineIntel
|
||||
ID: 76 06 01 00 FF FB EB BF
|
||||
Signature: Type 0, Family 6, Model 23, Stepping 6
|
||||
Flags:
|
||||
FPU (Floating-point unit on-chip)
|
||||
VME (Virtual mode extension)
|
||||
DE (Debugging extension)
|
||||
PSE (Page size extension)
|
||||
TSC (Time stamp counter)
|
||||
MSR (Model specific registers)
|
||||
PAE (Physical address extension)
|
||||
MCE (Machine check exception)
|
||||
CX8 (CMPXCHG8 instruction supported)
|
||||
APIC (On-chip APIC hardware supported)
|
||||
SEP (Fast system call)
|
||||
MTRR (Memory type range registers)
|
||||
PGE (Page global enable)
|
||||
MCA (Machine check architecture)
|
||||
CMOV (Conditional move instruction supported)
|
||||
PAT (Page attribute table)
|
||||
PSE-36 (36-bit page size extension)
|
||||
CLFSH (CLFLUSH instruction supported)
|
||||
DS (Debug store)
|
||||
ACPI (ACPI supported)
|
||||
MMX (MMX technology supported)
|
||||
FXSR (FXSAVE and FXSTOR instructions supported)
|
||||
SSE (Streaming SIMD extensions)
|
||||
SSE2 (Streaming SIMD extensions 2)
|
||||
SS (Self-snoop)
|
||||
HTT (Multi-threading)
|
||||
TM (Thermal monitor supported)
|
||||
PBE (Pending break enabled)
|
||||
Version: Intel(R) Core(TM)2 Duo CPU P8600 @ 2.40GHz
|
||||
Voltage: 1.2 V
|
||||
External Clock: 266 MHz
|
||||
Max Speed: 2400 MHz
|
||||
Current Speed: 2400 MHz
|
||||
Status: Populated, Enabled
|
||||
Upgrade: None
|
||||
L1 Cache Handle: 0x000A
|
||||
L2 Cache Handle: 0x000C
|
||||
L3 Cache Handle: Not Provided
|
||||
Serial Number: Not Specified
|
||||
Asset Tag: Not Specified
|
||||
Part Number: Not Specified
|
||||
|
||||
Handle 0x0007, DMI type 5, 20 bytes
|
||||
Memory Controller Information
|
||||
Error Detecting Method: None
|
||||
Error Correcting Capabilities:
|
||||
None
|
||||
Supported Interleave: One-way Interleave
|
||||
Current Interleave: One-way Interleave
|
||||
Maximum Memory Module Size: 4096 MB
|
||||
Maximum Total Memory Size: 8192 MB
|
||||
Supported Speeds:
|
||||
Other
|
||||
Supported Memory Types:
|
||||
DIMM
|
||||
SDRAM
|
||||
Memory Module Voltage: 2.9 V
|
||||
Associated Memory Slots: 2
|
||||
0x0008
|
||||
0x0009
|
||||
Enabled Error Correcting Capabilities:
|
||||
Unknown
|
||||
|
||||
Handle 0x0008, DMI type 6, 12 bytes
|
||||
Memory Module Information
|
||||
Socket Designation: DIMM Slot 1
|
||||
Bank Connections: 0 1
|
||||
Current Speed: 42 ns
|
||||
Type: DIMM SDRAM
|
||||
Installed Size: 2048 MB (Double-bank Connection)
|
||||
Enabled Size: 2048 MB (Double-bank Connection)
|
||||
Error Status: OK
|
||||
|
||||
Handle 0x0009, DMI type 6, 12 bytes
|
||||
Memory Module Information
|
||||
Socket Designation: DIMM Slot 2
|
||||
Bank Connections: 2 3
|
||||
Current Speed: 42 ns
|
||||
Type: DIMM SDRAM
|
||||
Installed Size: Not Installed
|
||||
Enabled Size: Not Installed
|
||||
Error Status: OK
|
||||
|
||||
Handle 0x000A, DMI type 7, 19 bytes
|
||||
Cache Information
|
||||
Socket Designation: Internal L1 Cache
|
||||
Configuration: Enabled, Socketed, Level 1
|
||||
Operational Mode: Write Back
|
||||
Location: Internal
|
||||
Installed Size: 64 kB
|
||||
Maximum Size: 64 kB
|
||||
Supported SRAM Types:
|
||||
Synchronous
|
||||
Installed SRAM Type: Synchronous
|
||||
Speed: Unknown
|
||||
Error Correction Type: Single-bit ECC
|
||||
System Type: Instruction
|
||||
Associativity: 8-way Set-associative
|
||||
|
||||
Handle 0x000B, DMI type 7, 19 bytes
|
||||
Cache Information
|
||||
Socket Designation: Internal L1 Cache
|
||||
Configuration: Enabled, Socketed, Level 1
|
||||
Operational Mode: Write Back
|
||||
Location: Internal
|
||||
Installed Size: 64 kB
|
||||
Maximum Size: 64 kB
|
||||
Supported SRAM Types:
|
||||
Synchronous
|
||||
Installed SRAM Type: Synchronous
|
||||
Speed: Unknown
|
||||
Error Correction Type: Single-bit ECC
|
||||
System Type: Data
|
||||
Associativity: 8-way Set-associative
|
||||
|
||||
Handle 0x000C, DMI type 7, 19 bytes
|
||||
Cache Information
|
||||
Socket Designation: Internal L2 Cache
|
||||
Configuration: Enabled, Socketed, Level 2
|
||||
Operational Mode: Write Back
|
||||
Location: Internal
|
||||
Installed Size: 3072 kB
|
||||
Maximum Size: 3072 kB
|
||||
Supported SRAM Types:
|
||||
Burst
|
||||
Installed SRAM Type: Burst
|
||||
Speed: Unknown
|
||||
Error Correction Type: Single-bit ECC
|
||||
System Type: Unified
|
||||
Associativity: 8-way Set-associative
|
||||
|
||||
Handle 0x000D, DMI type 8, 9 bytes
|
||||
Port Connector Information
|
||||
Internal Reference Designator: Not Available
|
||||
Internal Connector Type: None
|
||||
External Reference Designator: External Monitor
|
||||
External Connector Type: DB-15 female
|
||||
Port Type: Video Port
|
||||
|
||||
Handle 0x000E, DMI type 8, 9 bytes
|
||||
Port Connector Information
|
||||
Internal Reference Designator: Not Available
|
||||
Internal Connector Type: None
|
||||
External Reference Designator: Microphone Jack
|
||||
External Connector Type: Mini Jack (headphones)
|
||||
Port Type: Audio Port
|
||||
|
||||
Handle 0x000F, DMI type 8, 9 bytes
|
||||
Port Connector Information
|
||||
Internal Reference Designator: Not Available
|
||||
Internal Connector Type: None
|
||||
External Reference Designator: Headphone Jack
|
||||
External Connector Type: Mini Jack (headphones)
|
||||
Port Type: Audio Port
|
||||
|
||||
Handle 0x0010, DMI type 8, 9 bytes
|
||||
Port Connector Information
|
||||
Internal Reference Designator: Not Available
|
||||
Internal Connector Type: None
|
||||
External Reference Designator: Modem
|
||||
External Connector Type: RJ-11
|
||||
Port Type: Modem Port
|
||||
|
||||
Handle 0x0011, DMI type 8, 9 bytes
|
||||
Port Connector Information
|
||||
Internal Reference Designator: Not Available
|
||||
Internal Connector Type: None
|
||||
External Reference Designator: Ethernet
|
||||
External Connector Type: RJ-45
|
||||
Port Type: Network Port
|
||||
|
||||
Handle 0x0012, DMI type 8, 9 bytes
|
||||
Port Connector Information
|
||||
Internal Reference Designator: Not Available
|
||||
Internal Connector Type: None
|
||||
External Reference Designator: USB 1
|
||||
External Connector Type: Access Bus (USB)
|
||||
Port Type: USB
|
||||
|
||||
Handle 0x0013, DMI type 8, 9 bytes
|
||||
Port Connector Information
|
||||
Internal Reference Designator: Not Available
|
||||
Internal Connector Type: None
|
||||
External Reference Designator: USB 2
|
||||
External Connector Type: Access Bus (USB)
|
||||
Port Type: USB
|
||||
|
||||
Handle 0x0014, DMI type 8, 9 bytes
|
||||
Port Connector Information
|
||||
Internal Reference Designator: Not Available
|
||||
Internal Connector Type: None
|
||||
External Reference Designator: USB 3
|
||||
External Connector Type: Access Bus (USB)
|
||||
Port Type: USB
|
||||
|
||||
Handle 0x0015, DMI type 126, 9 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x0016, DMI type 126, 9 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x0017, DMI type 126, 9 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x0018, DMI type 126, 9 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x0019, DMI type 126, 9 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x001A, DMI type 126, 9 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x001B, DMI type 126, 13 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x001C, DMI type 10, 6 bytes
|
||||
On Board Device Information
|
||||
Type: Other
|
||||
Status: Disabled
|
||||
Description: IBM Embedded Security hardware
|
||||
|
||||
Handle 0x001D, DMI type 11, 5 bytes
|
||||
OEM Strings
|
||||
String 1: IBM ThinkPad Embedded Controller -[7XHT24WW-1.06 ]-
|
||||
|
||||
Handle 0x001E, DMI type 13, 22 bytes
|
||||
BIOS Language Information
|
||||
Language Description Format: Abbreviated
|
||||
Installable Languages: 1
|
||||
enUS
|
||||
Currently Installed Language: enUS
|
||||
|
||||
Handle 0x001F, DMI type 15, 25 bytes
|
||||
System Event Log
|
||||
Area Length: 0 bytes
|
||||
Header Start Offset: 0x0000
|
||||
Header Length: 16 bytes
|
||||
Data Start Offset: 0x0010
|
||||
Access Method: General-purpose non-volatile data functions
|
||||
Access Address: 0x0000
|
||||
Status: Valid, Not Full
|
||||
Change Token: 0x000000FC
|
||||
Header Format: Type 1
|
||||
Supported Log Type Descriptors: 1
|
||||
Descriptor 1: POST error
|
||||
Data Format 1: POST results bitmap
|
||||
|
||||
Handle 0x0020, DMI type 16, 15 bytes
|
||||
Physical Memory Array
|
||||
Location: System Board Or Motherboard
|
||||
Use: System Memory
|
||||
Error Correction Type: None
|
||||
Maximum Capacity: 4 GB
|
||||
Error Information Handle: Not Provided
|
||||
Number Of Devices: 2
|
||||
|
||||
Handle 0x0021, DMI type 17, 27 bytes
|
||||
Memory Device
|
||||
Array Handle: 0x0020
|
||||
Error Information Handle: No Error
|
||||
Total Width: 64 bits
|
||||
Data Width: 64 bits
|
||||
Size: 2048 MB
|
||||
Form Factor: SODIMM
|
||||
Set: None
|
||||
Locator: DIMM 1
|
||||
Bank Locator: Bank 0/1
|
||||
Type: DDR3
|
||||
Type Detail: Synchronous
|
||||
Speed: 1066 MHz
|
||||
Manufacturer: 02FE
|
||||
Serial Number: F4BB7CA2
|
||||
Asset Tag: 0839
|
||||
Part Number: EBJ21UE8BASA-AE-E
|
||||
|
||||
Handle 0x0022, DMI type 17, 27 bytes
|
||||
Memory Device
|
||||
Array Handle: 0x0020
|
||||
Error Information Handle: No Error
|
||||
Total Width: Unknown
|
||||
Data Width: Unknown
|
||||
Size: No Module Installed
|
||||
Form Factor: SODIMM
|
||||
Set: None
|
||||
Locator: DIMM 2
|
||||
Bank Locator: Bank 2/3
|
||||
Type: DDR2
|
||||
Type Detail: Synchronous
|
||||
Speed: 1066 MHz
|
||||
Manufacturer:
|
||||
Serial Number:
|
||||
Asset Tag:
|
||||
Part Number:
|
||||
|
||||
Handle 0x0023, DMI type 18, 23 bytes
|
||||
32-bit Memory Error Information
|
||||
Type: OK
|
||||
Granularity: Unknown
|
||||
Operation: Unknown
|
||||
Vendor Syndrome: Unknown
|
||||
Memory Array Address: Unknown
|
||||
Device Address: Unknown
|
||||
Resolution: Unknown
|
||||
|
||||
Handle 0x0024, DMI type 19, 15 bytes
|
||||
Memory Array Mapped Address
|
||||
Starting Address: 0x00000000000
|
||||
Ending Address: 0x0007FFFFFFF
|
||||
Range Size: 2 GB
|
||||
Physical Array Handle: 0x0020
|
||||
Partition Width: 2
|
||||
|
||||
Handle 0x0025, DMI type 20, 19 bytes
|
||||
Memory Device Mapped Address
|
||||
Starting Address: 0x00000000000
|
||||
Ending Address: 0x0007FFFFFFF
|
||||
Range Size: 2 GB
|
||||
Physical Device Handle: 0x0021
|
||||
Memory Array Mapped Address Handle: 0x0024
|
||||
Partition Row Position: 1
|
||||
|
||||
Handle 0x0026, DMI type 20, 19 bytes
|
||||
Memory Device Mapped Address
|
||||
Starting Address: 0x0007FFFFC00
|
||||
Ending Address: 0x0007FFFFFFF
|
||||
Range Size: 1 kB
|
||||
Physical Device Handle: 0x0022
|
||||
Memory Array Mapped Address Handle: 0x0024
|
||||
Partition Row Position: 1
|
||||
|
||||
Handle 0x0027, DMI type 21, 7 bytes
|
||||
Built-in Pointing Device
|
||||
Type: Track Point
|
||||
Interface: PS/2
|
||||
Buttons: 3
|
||||
|
||||
Handle 0x0028, DMI type 126, 26 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x0029, DMI type 126, 26 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x002A, DMI type 24, 5 bytes
|
||||
Hardware Security
|
||||
Power-On Password Status: Disabled
|
||||
Keyboard Password Status: Disabled
|
||||
Administrator Password Status: Disabled
|
||||
Front Panel Reset Status: Unknown
|
||||
|
||||
Handle 0x002B, DMI type 32, 11 bytes
|
||||
System Boot Information
|
||||
Status: No errors detected
|
||||
|
||||
Handle 0x002C, DMI type 131, 17 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
83 11 2C 00 01 02 03 FF FF 1F 00 00 00 00 00 02
|
||||
00
|
||||
Strings:
|
||||
BOOTINF 20h
|
||||
BOOTDEV 21h
|
||||
KEYPTRS 23h
|
||||
|
||||
Handle 0x002D, DMI type 131, 22 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
83 16 2D 00 01 00 00 00 00 00 00 00 00 00 00 00
|
||||
00 00 00 00 00 01
|
||||
Strings:
|
||||
TVT-Enablement
|
||||
|
||||
Handle 0x002E, DMI type 132, 7 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
84 07 2E 00 02 D8 36
|
||||
|
||||
Handle 0x002F, DMI type 133, 5 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
85 05 2F 00 01
|
||||
Strings:
|
||||
KHOIHGIUCCHHII
|
||||
|
||||
Handle 0x0030, DMI type 134, 13 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
86 0D 30 00 30 10 08 20 00 00 00 00 00
|
||||
|
||||
Handle 0x0031, DMI type 134, 16 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
86 10 31 00 00 49 4E 54 43 01 01 00 00 02 01 02
|
||||
Strings:
|
||||
TPM INFO
|
||||
System Reserved
|
||||
|
||||
Handle 0x0032, DMI type 135, 13 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
87 0D 32 00 54 50 07 00 01 00 00 00 00
|
||||
|
||||
Handle 0x0033, DMI type 135, 18 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
87 12 33 00 54 50 07 01 01 B9 05 00 00 00 00 00
|
||||
00 00
|
||||
|
||||
Handle 0x0034, DMI type 135, 35 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
87 23 34 00 54 50 07 02 42 41 59 20 49 2F 4F 20
|
||||
01 00 02 00 00 0B 00 48 1C 3E 18 02 00 0B 00 40
|
||||
1C 3A 18
|
||||
|
||||
Handle 0x0035, DMI type 135, 34 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
87 22 35 00 54 50 07 04 01 06 01 01 02 00 02 01
|
||||
02 00 03 01 02 00 04 01 02 00 05 01 02 00 06 01
|
||||
02 00
|
||||
|
||||
Handle 0x0036, DMI type 135, 10 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
87 0A 36 00 54 50 07 03 01 0A
|
||||
|
||||
Handle 0x0037, DMI type 136, 6 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
88 06 37 00 5A 5A
|
||||
|
||||
Handle 0x0038, DMI type 126, 28 bytes
|
||||
Inactive
|
||||
|
||||
Handle 0x0039, DMI type 138, 40 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
8A 28 39 00 14 01 02 01 40 02 01 40 02 01 40 02
|
||||
01 40 01 40 42 49 4F 53 20 50 61 73 73 77 6F 72
|
||||
64 20 46 6F 72 6D 61 74
|
||||
|
||||
Handle 0x003A, DMI type 139, 37 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
8B 25 3A 00 11 01 0A 00 00 00 00 00 00 00 00 00
|
||||
00 50 57 4D 53 20 4B 65 79 20 49 6E 66 6F 72 6D
|
||||
61 74 69 6F 6E
|
||||
|
||||
Handle 0x003B, DMI type 140, 67 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
8C 43 3B 00 4C 45 4E 4F 56 4F 0B 00 01 9A 13 CD
|
||||
C4 7A 2A 8E 76 C3 C4 4E B9 B1 DD 4E 7C 01 00 00
|
||||
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|
||||
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|
||||
00 00 00
|
||||
|
||||
Handle 0x003C, DMI type 140, 47 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
8C 2F 3C 00 4C 45 4E 4F 56 4F 0B 01 01 08 00 BF
|
||||
DA 3C 04 5C 72 D9 7D 0D 79 DE 46 98 23 10 B1 00
|
||||
00 00 00 10 00 10 00 10 01 D0 00 20 01 00 01
|
||||
|
||||
Handle 0x003D, DMI type 140, 63 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
8C 3F 3D 00 4C 45 4E 4F 56 4F 0B 02 01 00 00 00
|
||||
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|
||||
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|
||||
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|
||||
|
||||
Handle 0x003E, DMI type 140, 17 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
8C 11 3E 00 4C 45 4E 4F 56 4F 0B 03 01 00 00 00
|
||||
00
|
||||
|
||||
Handle 0x003F, DMI type 140, 19 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
8C 13 3F 00 4C 45 4E 4F 56 4F 0B 04 01 B2 00 53
|
||||
4D 20 00
|
||||
|
||||
Handle 0x0040, DMI type 129, 8 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
81 08 40 00 01 01 02 01
|
||||
Strings:
|
||||
Intel_ASF
|
||||
Intel_ASF_001
|
||||
|
||||
Handle 0x0041, DMI type 130, 20 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
82 14 41 00 24 41 4D 54 01 01 01 01 01 A5 0B 04
|
||||
00 00 00 00
|
||||
|
||||
Handle 0x0042, DMI type 131, 64 bytes
|
||||
OEM-specific Type
|
||||
Header and Data:
|
||||
83 40 42 00 14 00 00 00 00 00 40 2A 00 00 00 00
|
||||
F8 00 17 29 00 00 00 00 2D 00 00 00 00 00 04 00
|
||||
64 04 03 00 01 00 01 15 C8 00 F5 10 00 00 00 00
|
||||
00 00 00 00 07 00 00 00 76 50 72 6F 00 00 00 00
|
||||
|
||||
Handle 0x0043, DMI type 127, 4 bytes
|
||||
End Of Table
|
||||
|
||||
|
|
@ -0,0 +1 @@
|
|||
bash: ectool: command not found
|
||||
|
|
@ -0,0 +1,14 @@
|
|||
========================================================================
|
||||
WARNING! You seem to be running flashrom on an unsupported laptop.
|
||||
Laptops, notebooks and netbooks are difficult to support and we
|
||||
recommend to use the vendor flashing utility. The embedded controller
|
||||
(EC) in these machines often interacts badly with flashing.
|
||||
See http://www.flashrom.org/Laptops for details.
|
||||
|
||||
If flash is shared with the EC, erase is guaranteed to brick your laptop
|
||||
and write may brick your laptop.
|
||||
Read and probe may irritate your EC and cause fan failure, backlight
|
||||
failure and sudden poweroff.
|
||||
You have been warned.
|
||||
========================================================================
|
||||
Proceeding anyway because user forced us to.
|
||||
|
|
@ -0,0 +1,289 @@
|
|||
flashrom v0.9.6.1-r1563 on Linux 3.13.0-39-lowlatency (x86_64)
|
||||
flashrom is free software, get the source code at http://www.flashrom.org
|
||||
|
||||
flashrom was built with libpci 3.1.9, GCC 4.7.1, little endian
|
||||
Command line (3 args): flashrom -V -p internal:laptop=force_I_want_a_brick
|
||||
Calibrating delay loop... OS timer resolution is 1 usecs, 1578M loops per second, 10 myus = 11 us, 100 myus = 114 us, 1000 myus = 1002 us, 10000 myus = 10004 us, 4 myus = 5 us, OK.
|
||||
Initializing internal programmer
|
||||
No coreboot table found.
|
||||
DMI string system-manufacturer: "LENOVO"
|
||||
DMI string system-product-name: "7459GW4"
|
||||
DMI string system-version: "ThinkPad X200"
|
||||
DMI string baseboard-manufacturer: "LENOVO"
|
||||
DMI string baseboard-product-name: "7459GW4"
|
||||
DMI string baseboard-version: "Not Available"
|
||||
DMI string chassis-type: "Notebook"
|
||||
Laptop detected via DMI.
|
||||
Found chipset "Intel ICH9M-E" with PCI ID 8086:2917. Enabling flash write...
|
||||
0xfff80000/0xffb80000 FWH IDSEL: 0x0
|
||||
0xfff00000/0xffb00000 FWH IDSEL: 0x0
|
||||
0xffe80000/0xffa80000 FWH IDSEL: 0x0
|
||||
0xffe00000/0xffa00000 FWH IDSEL: 0x0
|
||||
0xffd80000/0xff980000 FWH IDSEL: 0x0
|
||||
0xffd00000/0xff900000 FWH IDSEL: 0x0
|
||||
0xffc80000/0xff880000 FWH IDSEL: 0x0
|
||||
0xffc00000/0xff800000 FWH IDSEL: 0x0
|
||||
0xff700000/0xff300000 FWH IDSEL: 0x4
|
||||
0xff600000/0xff200000 FWH IDSEL: 0x5
|
||||
0xff500000/0xff100000 FWH IDSEL: 0x6
|
||||
0xff400000/0xff000000 FWH IDSEL: 0x7
|
||||
0xfff80000/0xffb80000 FWH decode enabled
|
||||
0xfff00000/0xffb00000 FWH decode enabled
|
||||
0xffe80000/0xffa80000 FWH decode enabled
|
||||
0xffe00000/0xffa00000 FWH decode enabled
|
||||
0xffd80000/0xff980000 FWH decode enabled
|
||||
0xffd00000/0xff900000 FWH decode enabled
|
||||
0xffc80000/0xff880000 FWH decode enabled
|
||||
0xffc00000/0xff800000 FWH decode enabled
|
||||
0xff700000/0xff300000 FWH decode disabled
|
||||
0xff600000/0xff200000 FWH decode disabled
|
||||
0xff500000/0xff100000 FWH decode disabled
|
||||
0xff400000/0xff000000 FWH decode disabled
|
||||
Maximum FWH chip size: 0x400000 bytes
|
||||
BIOS Lock Enable: disabled, BIOS Write Enable: disabled, BIOS_CNTL is 0x0
|
||||
Root Complex Register Block address = 0xfed1c000
|
||||
GCS = 0x7b0461: BIOS Interface Lock-Down: enabled, Boot BIOS Straps: 0x1 (SPI)
|
||||
Top Swap : not enabled
|
||||
SPIBAR = 0xfed1c000 + 0x3800
|
||||
0x04: 0xe008 (HSFS)
|
||||
HSFS: FDONE=0, FCERR=0, AEL=0, BERASE=1, SCIP=0, FDOPSS=1, FDV=1, FLOCKDN=1
|
||||
WARNING: SPI Configuration Lockdown activated.
|
||||
Reading OPCODES... done
|
||||
0x06: 0x3f04 (HSFC)
|
||||
HSFC: FGO=0, FCYCLE=2, FDBC=63, SME=0
|
||||
0x08: 0x00001000 (FADDR)
|
||||
0x50: 0x00001a1b (FRAP)
|
||||
BMWAG 0x00, BMRAG 0x00, BRWA 0x1a, BRRA 0x1b
|
||||
0x54: 0x00000000 FREG0: WARNING: Flash Descriptor region (0x00000000-0x00000fff) is read-only.
|
||||
0x58: 0x07ff0600 FREG1: BIOS region (0x00600000-0x007fffff) is read-write.
|
||||
0x5C: 0x05f50001 FREG2: WARNING: Management Engine region (0x00001000-0x005f5fff) is locked.
|
||||
0x60: 0x05f705f6 FREG3: Gigabit Ethernet region (0x005f6000-0x005f7fff) is read-write.
|
||||
0x64: 0x05ff05f8 FREG4: Platform Data region (0x005f8000-0x005fffff) is read-write.
|
||||
0x74: 0x9fff07e0 PR0: WARNING: 0x007e0000-0x01ffffff is read-only.
|
||||
0x84: 0x85ff85f8 PR4: WARNING: 0x005f8000-0x005fffff is locked.
|
||||
Please send a verbose log to flashrom@flashrom.org if this board is not listed on
|
||||
http://flashrom.org/Supported_hardware#Supported_mainboards yet.
|
||||
Writes have been disabled. You can enforce write support with the
|
||||
ich_spi_force programmer option, but it will most likely harm your hardware!
|
||||
If you force flashrom you will get no support if something breaks.
|
||||
0x90: 0x04 (SSFS)
|
||||
SSFS: SCIP=0, FDONE=1, FCERR=0, AEL=0
|
||||
0x91: 0x000000 (SSFC)
|
||||
SSFC: SCGO=0, ACS=0, SPOP=0, COP=0, DBC=0, SME=0, SCF=0
|
||||
0x94: 0x5006 (PREOP)
|
||||
0x96: 0x143b (OPTYPE)
|
||||
0x98: 0x05200302 (OPMENU)
|
||||
0x9C: 0x0601209f (OPMENU+4)
|
||||
0xA0: 0x00000000 (BBAR)
|
||||
0xC4: 0x00002005 (LVSCC)
|
||||
LVSCC: BES=0x1, WG=1, WSR=0, WEWS=0, EO=0x20, VCL=0
|
||||
0xC8: 0x00002005 (UVSCC)
|
||||
UVSCC: BES=0x1, WG=1, WSR=0, WEWS=0, EO=0x20, VCL=0
|
||||
0xD0: 0x00000000 (FPB)
|
||||
|
||||
SPI Read Configuration: prefetching disabled, caching enabled, OK.
|
||||
The following protocols are supported: FWH, SPI.
|
||||
Probing for AMIC A25L05PT, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L05PU, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L10PT, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L10PU, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L20PT, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L20PU, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L40PT, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L40PU, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L80P, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L16PT, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L16PU, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L512, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L010, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L020, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L040, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L080, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L016, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L032, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25LQ032, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF021, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF041A, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF081, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF081A, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF161, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF321, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF321A, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF641(A), 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DQ161, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25F512B, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25FS010, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25FS040, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT26DF041, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT26DF081A, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT26DF161, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT26DF161A, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT26F004, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45CS1282, 16896 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB011D, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB021D, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB041D, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB081D, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB161D, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB321C, 4224 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB321D, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB642D, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for EMST F25L008A, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B05, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B05T, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B10, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B10T, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B20T, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B40T, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B80T, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B16T, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B32T, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B64T, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F05, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F10, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q80(A), 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q32(A/B), 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q128, 16384 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25QH16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25QH32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q128, 16384 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L512, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L1005, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L2005, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L4005, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L8005, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L1605, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L1635D, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L1635E, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L3205, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L3235D, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L6405, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Chip status register is 00
|
||||
Chip status register: Status Register Write Disable (SRWD) is not set
|
||||
Chip status register: Bit 6 is not set
|
||||
Chip status register: Block Protect 3 (BP3) is not set
|
||||
Chip status register: Block Protect 2 (BP2) is not set
|
||||
Chip status register: Block Protect 1 (BP1) is not set
|
||||
Chip status register: Block Protect 0 (BP0) is not set
|
||||
Chip status register: Write Enable Latch (WEL) is not set
|
||||
Chip status register: Write In Progress (WIP/BUSY) is not set
|
||||
Found Macronix flash chip "MX25L6405" (8192 kB, SPI) at physical address 0xff800000.
|
||||
Probing for Macronix MX25L12805, 16384 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx M25PE10, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx M25PE20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx M25PE40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx M25PE80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx M25PE16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx N25Q064, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV010, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV016B, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV020, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV040, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV080B, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV512, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Sanyo LF25FW203A, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Spansion S25FL004A, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Spansion S25FL008A, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Spansion S25FL016A, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Spansion S25FL032A, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Spansion S25FL064A, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST SST25LF040A, 512 kB: Invalid OPCODE 0xab, will not execute.
|
||||
Probing for SST SST25LF080A, 1024 kB: Invalid OPCODE 0xab, will not execute.
|
||||
Probing for SST SST25VF010, 128 kB: Invalid OPCODE 0x90, will not execute.
|
||||
Probing for SST SST25VF016B, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST SST25VF032B, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST SST25VF064C, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST SST25VF040, 512 kB: Invalid OPCODE 0x90, will not execute.
|
||||
Probing for SST SST25VF040B, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST SST25VF040B.REMS, 512 kB: Invalid OPCODE 0x90, will not execute.
|
||||
Probing for SST SST25VF080B, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P05-A, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P05, 64 kB: Ignoring RES in favour of RDID.
|
||||
Probing for ST M25P10-A, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P10, 128 kB: Ignoring RES in favour of RDID.
|
||||
Probing for ST M25P20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P40-old, 512 kB: Ignoring RES in favour of RDID.
|
||||
Probing for ST M25P80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P128, 16384 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25PX16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25PX32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25PX64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25Q80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25Q16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25Q32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25Q64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25Q128, 16384 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X10, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Unknown SFDP-capable chip, 0 kB: Invalid OPCODE 0x5a, will not execute.
|
||||
Receiving SFDP signature failed.
|
||||
Probing for AMIC unknown AMIC SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel unknown Atmel SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon unknown Eon SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix unknown Macronix SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC unknown PMC SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST unknown SST SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST unknown ST SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Sanyo unknown Sanyo SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Generic unknown SPI chip (RDID), 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Generic unknown SPI chip (REMS), 0 kB: Invalid OPCODE 0x90, will not execute.
|
||||
Probing for Atmel AT49LH002, 256 kB: probe_82802ab: id1 0xff, id2 0xff, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Intel 82802AB, 512 kB: probe_82802ab: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Intel 82802AC, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for PMC Pm49FL002, 256 kB: probe_jedec_common: id1 0xff, id2 0xff, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for PMC Pm49FL004, 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Sharp LHF00L04, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF002A/B, 256 kB: probe_jedec_common: id1 0xff, id2 0xff, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF003A/B, 384 kB: probe_jedec_common: id1 0x0a, id2 0xce, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF004A/B, 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF004C, 512 kB: probe_82802ab: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF008A, 1024 kB: probe_jedec_common: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF008C, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF016C, 2048 kB: probe_82802ab: id1 0x4e, id2 0x41, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FLW040A, 512 kB: probe_82802ab: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FLW040B, 512 kB: probe_82802ab: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FLW080A, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FLW080B, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FW002, 256 kB: probe_82802ab: id1 0xff, id2 0xff, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FW016, 2048 kB: probe_82802ab: id1 0x4e, id2 0x41, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FW040, 512 kB: probe_82802ab: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FW080, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W39V040FA, 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W39V040FB, 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W39V040FC, 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W49V002FA, 256 kB: probe_jedec_common: id1 0xff, id2 0xff, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W39V080FA, 1024 kB: probe_jedec_common: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W39V080FA (dual mode), 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Found Macronix flash chip "MX25L6405" (8192 kB, SPI).
|
||||
No operations were specified.
|
||||
Restoring MMIO space at 0x7f9c951da8a0
|
||||
Restoring PCI config space for 00:1f:0 reg 0xdc
|
||||
|
|
@ -0,0 +1,16 @@
|
|||
========================================================================
|
||||
WARNING! You seem to be running flashrom on an unsupported laptop.
|
||||
Laptops, notebooks and netbooks are difficult to support and we
|
||||
recommend to use the vendor flashing utility. The embedded controller
|
||||
(EC) in these machines often interacts badly with flashing.
|
||||
See http://www.flashrom.org/Laptops for details.
|
||||
|
||||
If flash is shared with the EC, erase is guaranteed to brick your laptop
|
||||
and write may brick your laptop.
|
||||
Read and probe may irritate your EC and cause fan failure, backlight
|
||||
failure and sudden poweroff.
|
||||
You have been warned.
|
||||
========================================================================
|
||||
Proceeding anyway because user forced us to.
|
||||
Transaction error!
|
||||
Read operation failed!
|
||||
|
|
@ -0,0 +1,292 @@
|
|||
flashrom v0.9.6.1-r1563 on Linux 3.13.0-39-lowlatency (x86_64)
|
||||
flashrom is free software, get the source code at http://www.flashrom.org
|
||||
|
||||
flashrom was built with libpci 3.1.9, GCC 4.7.1, little endian
|
||||
Command line (5 args): flashrom -V -p internal:laptop=force_I_want_a_brick -r rom.bin
|
||||
Calibrating delay loop... OS timer resolution is 2 usecs, 1579M loops per second, 10 myus = 10 us, 100 myus = 100 us, 1000 myus = 1004 us, 10000 myus = 10014 us, 8 myus = 9 us, OK.
|
||||
Initializing internal programmer
|
||||
No coreboot table found.
|
||||
DMI string system-manufacturer: "LENOVO"
|
||||
DMI string system-product-name: "7459GW4"
|
||||
DMI string system-version: "ThinkPad X200"
|
||||
DMI string baseboard-manufacturer: "LENOVO"
|
||||
DMI string baseboard-product-name: "7459GW4"
|
||||
DMI string baseboard-version: "Not Available"
|
||||
DMI string chassis-type: "Notebook"
|
||||
Laptop detected via DMI.
|
||||
Found chipset "Intel ICH9M-E" with PCI ID 8086:2917. Enabling flash write...
|
||||
0xfff80000/0xffb80000 FWH IDSEL: 0x0
|
||||
0xfff00000/0xffb00000 FWH IDSEL: 0x0
|
||||
0xffe80000/0xffa80000 FWH IDSEL: 0x0
|
||||
0xffe00000/0xffa00000 FWH IDSEL: 0x0
|
||||
0xffd80000/0xff980000 FWH IDSEL: 0x0
|
||||
0xffd00000/0xff900000 FWH IDSEL: 0x0
|
||||
0xffc80000/0xff880000 FWH IDSEL: 0x0
|
||||
0xffc00000/0xff800000 FWH IDSEL: 0x0
|
||||
0xff700000/0xff300000 FWH IDSEL: 0x4
|
||||
0xff600000/0xff200000 FWH IDSEL: 0x5
|
||||
0xff500000/0xff100000 FWH IDSEL: 0x6
|
||||
0xff400000/0xff000000 FWH IDSEL: 0x7
|
||||
0xfff80000/0xffb80000 FWH decode enabled
|
||||
0xfff00000/0xffb00000 FWH decode enabled
|
||||
0xffe80000/0xffa80000 FWH decode enabled
|
||||
0xffe00000/0xffa00000 FWH decode enabled
|
||||
0xffd80000/0xff980000 FWH decode enabled
|
||||
0xffd00000/0xff900000 FWH decode enabled
|
||||
0xffc80000/0xff880000 FWH decode enabled
|
||||
0xffc00000/0xff800000 FWH decode enabled
|
||||
0xff700000/0xff300000 FWH decode disabled
|
||||
0xff600000/0xff200000 FWH decode disabled
|
||||
0xff500000/0xff100000 FWH decode disabled
|
||||
0xff400000/0xff000000 FWH decode disabled
|
||||
Maximum FWH chip size: 0x400000 bytes
|
||||
BIOS Lock Enable: disabled, BIOS Write Enable: disabled, BIOS_CNTL is 0x0
|
||||
Root Complex Register Block address = 0xfed1c000
|
||||
GCS = 0x7b0461: BIOS Interface Lock-Down: enabled, Boot BIOS Straps: 0x1 (SPI)
|
||||
Top Swap : not enabled
|
||||
SPIBAR = 0xfed1c000 + 0x3800
|
||||
0x04: 0xe008 (HSFS)
|
||||
HSFS: FDONE=0, FCERR=0, AEL=0, BERASE=1, SCIP=0, FDOPSS=1, FDV=1, FLOCKDN=1
|
||||
WARNING: SPI Configuration Lockdown activated.
|
||||
Reading OPCODES... done
|
||||
0x06: 0x3f04 (HSFC)
|
||||
HSFC: FGO=0, FCYCLE=2, FDBC=63, SME=0
|
||||
0x08: 0x00000000 (FADDR)
|
||||
0x50: 0x00001a1b (FRAP)
|
||||
BMWAG 0x00, BMRAG 0x00, BRWA 0x1a, BRRA 0x1b
|
||||
0x54: 0x00000000 FREG0: WARNING: Flash Descriptor region (0x00000000-0x00000fff) is read-only.
|
||||
0x58: 0x07ff0600 FREG1: BIOS region (0x00600000-0x007fffff) is read-write.
|
||||
0x5C: 0x05f50001 FREG2: WARNING: Management Engine region (0x00001000-0x005f5fff) is locked.
|
||||
0x60: 0x05f705f6 FREG3: Gigabit Ethernet region (0x005f6000-0x005f7fff) is read-write.
|
||||
0x64: 0x05ff05f8 FREG4: Platform Data region (0x005f8000-0x005fffff) is read-write.
|
||||
0x74: 0x9fff07e0 PR0: WARNING: 0x007e0000-0x01ffffff is read-only.
|
||||
0x84: 0x85ff85f8 PR4: WARNING: 0x005f8000-0x005fffff is locked.
|
||||
Please send a verbose log to flashrom@flashrom.org if this board is not listed on
|
||||
http://flashrom.org/Supported_hardware#Supported_mainboards yet.
|
||||
Writes have been disabled. You can enforce write support with the
|
||||
ich_spi_force programmer option, but it will most likely harm your hardware!
|
||||
If you force flashrom you will get no support if something breaks.
|
||||
0x90: 0x04 (SSFS)
|
||||
SSFS: SCIP=0, FDONE=1, FCERR=0, AEL=0
|
||||
0x91: 0x004240 (SSFC)
|
||||
SSFC: SCGO=0, ACS=0, SPOP=0, COP=4, DBC=2, SME=0, SCF=0
|
||||
0x94: 0x5006 (PREOP)
|
||||
0x96: 0x143b (OPTYPE)
|
||||
0x98: 0x05200302 (OPMENU)
|
||||
0x9C: 0x0601209f (OPMENU+4)
|
||||
0xA0: 0x00000000 (BBAR)
|
||||
0xC4: 0x00002005 (LVSCC)
|
||||
LVSCC: BES=0x1, WG=1, WSR=0, WEWS=0, EO=0x20, VCL=0
|
||||
0xC8: 0x00002005 (UVSCC)
|
||||
UVSCC: BES=0x1, WG=1, WSR=0, WEWS=0, EO=0x20, VCL=0
|
||||
0xD0: 0x00000000 (FPB)
|
||||
|
||||
SPI Read Configuration: prefetching disabled, caching enabled, OK.
|
||||
The following protocols are supported: FWH, SPI.
|
||||
Probing for AMIC A25L05PT, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L05PU, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L10PT, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L10PU, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L20PT, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L20PU, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L40PT, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L40PU, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L80P, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L16PT, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L16PU, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L512, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L010, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L020, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L040, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L080, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L016, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25L032, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for AMIC A25LQ032, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF021, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF041A, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF081, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF081A, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF161, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF321, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF321A, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DF641(A), 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25DQ161, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25F512B, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25FS010, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT25FS040, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT26DF041, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT26DF081A, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT26DF161, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT26DF161A, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT26F004, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45CS1282, 16896 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB011D, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB021D, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB041D, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB081D, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB161D, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB321C, 4224 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB321D, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel AT45DB642D, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for EMST F25L008A, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B05, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B05T, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B10, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B10T, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B20T, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B40T, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B80T, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B16T, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B32T, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25B64T, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F05, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F10, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25F32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q80(A), 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q32(A/B), 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25Q128, 16384 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25QH16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon EN25QH32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for GigaDevice GD25Q128, 16384 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L512, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L1005, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L2005, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L4005, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L8005, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L1605, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L1635D, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L1635E, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L3205, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L3235D, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix MX25L6405, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Chip status register is 00
|
||||
Chip status register: Status Register Write Disable (SRWD) is not set
|
||||
Chip status register: Bit 6 is not set
|
||||
Chip status register: Block Protect 3 (BP3) is not set
|
||||
Chip status register: Block Protect 2 (BP2) is not set
|
||||
Chip status register: Block Protect 1 (BP1) is not set
|
||||
Chip status register: Block Protect 0 (BP0) is not set
|
||||
Chip status register: Write Enable Latch (WEL) is not set
|
||||
Chip status register: Write In Progress (WIP/BUSY) is not set
|
||||
Found Macronix flash chip "MX25L6405" (8192 kB, SPI) at physical address 0xff800000.
|
||||
Probing for Macronix MX25L12805, 16384 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx M25PE10, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx M25PE20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx M25PE40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx M25PE80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx M25PE16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Numonyx N25Q064, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV010, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV016B, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV020, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV040, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV080B, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC Pm25LV512, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Sanyo LF25FW203A, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Spansion S25FL004A, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Spansion S25FL008A, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Spansion S25FL016A, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Spansion S25FL032A, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Spansion S25FL064A, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST SST25LF040A, 512 kB: Invalid OPCODE 0xab, will not execute.
|
||||
Probing for SST SST25LF080A, 1024 kB: Invalid OPCODE 0xab, will not execute.
|
||||
Probing for SST SST25VF010, 128 kB: Invalid OPCODE 0x90, will not execute.
|
||||
Probing for SST SST25VF016B, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST SST25VF032B, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST SST25VF064C, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST SST25VF040, 512 kB: Invalid OPCODE 0x90, will not execute.
|
||||
Probing for SST SST25VF040B, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST SST25VF040B.REMS, 512 kB: Invalid OPCODE 0x90, will not execute.
|
||||
Probing for SST SST25VF080B, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P05-A, 64 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P05, 64 kB: Ignoring RES in favour of RDID.
|
||||
Probing for ST M25P10-A, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P10, 128 kB: Ignoring RES in favour of RDID.
|
||||
Probing for ST M25P20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P40-old, 512 kB: Ignoring RES in favour of RDID.
|
||||
Probing for ST M25P80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25P128, 16384 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25PX16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25PX32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST M25PX64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25Q80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25Q16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25Q32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25Q64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25Q128, 16384 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X10, 128 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X20, 256 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X40, 512 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X80, 1024 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X16, 2048 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X32, 4096 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Winbond W25X64, 8192 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Unknown SFDP-capable chip, 0 kB: Invalid OPCODE 0x5a, will not execute.
|
||||
Receiving SFDP signature failed.
|
||||
Probing for AMIC unknown AMIC SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Atmel unknown Atmel SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Eon unknown Eon SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Macronix unknown Macronix SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for PMC unknown PMC SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for SST unknown SST SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for ST unknown ST SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Sanyo unknown Sanyo SPI chip, 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Generic unknown SPI chip (RDID), 0 kB: probe_spi_rdid_generic: id1 0xc2, id2 0x2017
|
||||
Probing for Generic unknown SPI chip (REMS), 0 kB: Invalid OPCODE 0x90, will not execute.
|
||||
Probing for Atmel AT49LH002, 256 kB: probe_82802ab: id1 0xff, id2 0xff, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Intel 82802AB, 512 kB: probe_82802ab: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Intel 82802AC, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for PMC Pm49FL002, 256 kB: probe_jedec_common: id1 0xff, id2 0xff, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for PMC Pm49FL004, 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Sharp LHF00L04, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF002A/B, 256 kB: probe_jedec_common: id1 0xff, id2 0xff, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF003A/B, 384 kB: probe_jedec_common: id1 0x0a, id2 0xce, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF004A/B, 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF004C, 512 kB: probe_82802ab: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF008A, 1024 kB: probe_jedec_common: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF008C, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for SST SST49LF016C, 2048 kB: probe_82802ab: id1 0x4e, id2 0x41, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FLW040A, 512 kB: probe_82802ab: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FLW040B, 512 kB: probe_82802ab: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FLW080A, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FLW080B, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FW002, 256 kB: probe_82802ab: id1 0xff, id2 0xff, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FW016, 2048 kB: probe_82802ab: id1 0x4e, id2 0x41, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FW040, 512 kB: probe_82802ab: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for ST M50FW080, 1024 kB: probe_82802ab: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W39V040FA, 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W39V040FB, 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W39V040FC, 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W49V002FA, 256 kB: probe_jedec_common: id1 0xff, id2 0xff, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W39V080FA, 1024 kB: probe_jedec_common: id1 0xba, id2 0x8e, id1 is normal flash content, id2 is normal flash content
|
||||
Probing for Winbond W39V080FA (dual mode), 512 kB: probe_jedec_common: id1 0x50, id2 0x09, id1 parity violation, id1 is normal flash content, id2 is normal flash content
|
||||
Found Macronix flash chip "MX25L6405" (8192 kB, SPI).
|
||||
Reading flash... SSFS: SCIP=0, FDONE=1, FCERR=1, AEL=0
|
||||
SSFC: SCGO=0, ACS=0, SPOP=0, COP=1, DBC=63, SME=0, SCF=0
|
||||
Running OPCODE 0x03 failed at address 0x001000 (payload length was 64).
|
||||
FAILED.
|
||||
Restoring MMIO space at 0x7f53b721c8a0
|
||||
Restoring PCI config space for 00:1f:0 reg 0xdc
|
||||
|
|
@ -0,0 +1,11 @@
|
|||
0019
|
||||
0000
|
||||
0000
|
||||
0019
|
||||
0019
|
||||
0011
|
||||
0011
|
||||
0019
|
||||
0019
|
||||
0000
|
||||
0000
|
||||
|
|
@ -0,0 +1 @@
|
|||
bash: inteltool: command not found
|
||||
|
|
@ -0,0 +1,60 @@
|
|||
0000-0cf7 : PCI Bus 0000:00
|
||||
0000-001f : dma1
|
||||
0020-0021 : pic1
|
||||
0040-0043 : timer0
|
||||
0050-0053 : timer1
|
||||
0060-0060 : keyboard
|
||||
0062-0062 : EC data
|
||||
0064-0064 : keyboard
|
||||
0066-0066 : EC cmd
|
||||
0070-0071 : rtc0
|
||||
0080-008f : dma page reg
|
||||
00a0-00a1 : pic2
|
||||
00c0-00df : dma2
|
||||
00f0-00ff : fpu
|
||||
03c0-03df : vga+
|
||||
0800-080f : pnp 00:01
|
||||
0cf8-0cff : PCI conf1
|
||||
0d00-ffff : PCI Bus 0000:00
|
||||
1000-1003 : ACPI PM1a_EVT_BLK
|
||||
1004-1005 : ACPI PM1a_CNT_BLK
|
||||
1008-100b : ACPI PM_TMR
|
||||
1010-1015 : ACPI CPU throttle
|
||||
1020-102f : ACPI GPE0_BLK
|
||||
1030-1033 : iTCO_wdt
|
||||
1050-1050 : ACPI PM2_CNT_BLK
|
||||
1060-107f : iTCO_wdt
|
||||
1180-11ff : pnp 00:01
|
||||
15e0-15ef : pnp 00:01
|
||||
1600-167f : pnp 00:01
|
||||
1680-169f : pnp 00:01
|
||||
1800-1807 : 0000:00:02.0
|
||||
1830-1837 : 0000:00:03.3
|
||||
1830-1837 : serial
|
||||
1838-183b : 0000:00:1f.2
|
||||
1838-183b : ahci
|
||||
183c-183f : 0000:00:1f.2
|
||||
183c-183f : ahci
|
||||
1840-185f : 0000:00:19.0
|
||||
1860-187f : 0000:00:1a.0
|
||||
1860-187f : uhci_hcd
|
||||
1880-189f : 0000:00:1a.1
|
||||
1880-189f : uhci_hcd
|
||||
18a0-18bf : 0000:00:1a.2
|
||||
18a0-18bf : uhci_hcd
|
||||
18c0-18df : 0000:00:1d.0
|
||||
18c0-18df : uhci_hcd
|
||||
18e0-18ff : 0000:00:1d.1
|
||||
18e0-18ff : uhci_hcd
|
||||
1c00-1c1f : 0000:00:1d.2
|
||||
1c00-1c1f : uhci_hcd
|
||||
1c20-1c3f : 0000:00:1f.2
|
||||
1c20-1c3f : ahci
|
||||
1c40-1c47 : 0000:00:1f.2
|
||||
1c40-1c47 : ahci
|
||||
1c48-1c4f : 0000:00:1f.2
|
||||
1c48-1c4f : ahci
|
||||
1c60-1c7f : 0000:00:1f.3
|
||||
2000-2fff : PCI Bus 0000:05
|
||||
3000-3fff : PCI Bus 0000:02
|
||||
4000-4fff : PCI Bus 0000:03
|
||||
File diff suppressed because it is too large
Load Diff
|
|
@ -0,0 +1 @@
|
|||
bash: lspnp: command not found
|
||||
|
|
@ -0,0 +1,820 @@
|
|||
|
||||
Bus 002 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
|
||||
Device Descriptor:
|
||||
bLength 18
|
||||
bDescriptorType 1
|
||||
bcdUSB 2.00
|
||||
bDeviceClass 9 Hub
|
||||
bDeviceSubClass 0 Unused
|
||||
bDeviceProtocol 0 Full speed (or root) hub
|
||||
bMaxPacketSize0 64
|
||||
idVendor 0x1d6b Linux Foundation
|
||||
idProduct 0x0002 2.0 root hub
|
||||
bcdDevice 3.13
|
||||
iManufacturer 3 Linux 3.13.0-39-lowlatency ehci_hcd
|
||||
iProduct 2 EHCI Host Controller
|
||||
iSerial 1 0000:00:1d.7
|
||||
bNumConfigurations 1
|
||||
Configuration Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 2
|
||||
wTotalLength 25
|
||||
bNumInterfaces 1
|
||||
bConfigurationValue 1
|
||||
iConfiguration 0
|
||||
bmAttributes 0xe0
|
||||
Self Powered
|
||||
Remote Wakeup
|
||||
MaxPower 0mA
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 0
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 1
|
||||
bInterfaceClass 9 Hub
|
||||
bInterfaceSubClass 0 Unused
|
||||
bInterfaceProtocol 0 Full speed (or root) hub
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x81 EP 1 IN
|
||||
bmAttributes 3
|
||||
Transfer Type Interrupt
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0004 1x 4 bytes
|
||||
bInterval 12
|
||||
Hub Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 41
|
||||
nNbrPorts 6
|
||||
wHubCharacteristic 0x000a
|
||||
No power switching (usb 1.0)
|
||||
Per-port overcurrent protection
|
||||
bPwrOn2PwrGood 10 * 2 milli seconds
|
||||
bHubContrCurrent 0 milli Ampere
|
||||
DeviceRemovable 0x38
|
||||
PortPwrCtrlMask 0xff
|
||||
Hub Port Status:
|
||||
Port 1: 0000.0100 power
|
||||
Port 2: 0000.0100 power
|
||||
Port 3: 0000.0100 power
|
||||
Port 4: 0000.0100 power
|
||||
Port 5: 0000.0100 power
|
||||
Port 6: 0000.0100 power
|
||||
Device Status: 0x0001
|
||||
Self Powered
|
||||
|
||||
Bus 008 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Device Descriptor:
|
||||
bLength 18
|
||||
bDescriptorType 1
|
||||
bcdUSB 1.10
|
||||
bDeviceClass 9 Hub
|
||||
bDeviceSubClass 0 Unused
|
||||
bDeviceProtocol 0 Full speed (or root) hub
|
||||
bMaxPacketSize0 64
|
||||
idVendor 0x1d6b Linux Foundation
|
||||
idProduct 0x0001 1.1 root hub
|
||||
bcdDevice 3.13
|
||||
iManufacturer 3 Linux 3.13.0-39-lowlatency uhci_hcd
|
||||
iProduct 2 UHCI Host Controller
|
||||
iSerial 1 0000:00:1d.2
|
||||
bNumConfigurations 1
|
||||
Configuration Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 2
|
||||
wTotalLength 25
|
||||
bNumInterfaces 1
|
||||
bConfigurationValue 1
|
||||
iConfiguration 0
|
||||
bmAttributes 0xe0
|
||||
Self Powered
|
||||
Remote Wakeup
|
||||
MaxPower 0mA
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 0
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 1
|
||||
bInterfaceClass 9 Hub
|
||||
bInterfaceSubClass 0 Unused
|
||||
bInterfaceProtocol 0 Full speed (or root) hub
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x81 EP 1 IN
|
||||
bmAttributes 3
|
||||
Transfer Type Interrupt
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0002 1x 2 bytes
|
||||
bInterval 255
|
||||
Hub Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 41
|
||||
nNbrPorts 2
|
||||
wHubCharacteristic 0x000a
|
||||
No power switching (usb 1.0)
|
||||
Per-port overcurrent protection
|
||||
bPwrOn2PwrGood 1 * 2 milli seconds
|
||||
bHubContrCurrent 0 milli Ampere
|
||||
DeviceRemovable 0x02
|
||||
PortPwrCtrlMask 0xff
|
||||
Hub Port Status:
|
||||
Port 1: 0000.0100 power
|
||||
Port 2: 0000.0100 power
|
||||
Device Status: 0x0001
|
||||
Self Powered
|
||||
|
||||
Bus 007 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Device Descriptor:
|
||||
bLength 18
|
||||
bDescriptorType 1
|
||||
bcdUSB 1.10
|
||||
bDeviceClass 9 Hub
|
||||
bDeviceSubClass 0 Unused
|
||||
bDeviceProtocol 0 Full speed (or root) hub
|
||||
bMaxPacketSize0 64
|
||||
idVendor 0x1d6b Linux Foundation
|
||||
idProduct 0x0001 1.1 root hub
|
||||
bcdDevice 3.13
|
||||
iManufacturer 3 Linux 3.13.0-39-lowlatency uhci_hcd
|
||||
iProduct 2 UHCI Host Controller
|
||||
iSerial 1 0000:00:1d.1
|
||||
bNumConfigurations 1
|
||||
Configuration Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 2
|
||||
wTotalLength 25
|
||||
bNumInterfaces 1
|
||||
bConfigurationValue 1
|
||||
iConfiguration 0
|
||||
bmAttributes 0xe0
|
||||
Self Powered
|
||||
Remote Wakeup
|
||||
MaxPower 0mA
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 0
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 1
|
||||
bInterfaceClass 9 Hub
|
||||
bInterfaceSubClass 0 Unused
|
||||
bInterfaceProtocol 0 Full speed (or root) hub
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x81 EP 1 IN
|
||||
bmAttributes 3
|
||||
Transfer Type Interrupt
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0002 1x 2 bytes
|
||||
bInterval 255
|
||||
Hub Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 41
|
||||
nNbrPorts 2
|
||||
wHubCharacteristic 0x000a
|
||||
No power switching (usb 1.0)
|
||||
Per-port overcurrent protection
|
||||
bPwrOn2PwrGood 1 * 2 milli seconds
|
||||
bHubContrCurrent 0 milli Ampere
|
||||
DeviceRemovable 0x06
|
||||
PortPwrCtrlMask 0xff
|
||||
Hub Port Status:
|
||||
Port 1: 0000.0100 power
|
||||
Port 2: 0000.0100 power
|
||||
Device Status: 0x0001
|
||||
Self Powered
|
||||
|
||||
Bus 006 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Device Descriptor:
|
||||
bLength 18
|
||||
bDescriptorType 1
|
||||
bcdUSB 1.10
|
||||
bDeviceClass 9 Hub
|
||||
bDeviceSubClass 0 Unused
|
||||
bDeviceProtocol 0 Full speed (or root) hub
|
||||
bMaxPacketSize0 64
|
||||
idVendor 0x1d6b Linux Foundation
|
||||
idProduct 0x0001 1.1 root hub
|
||||
bcdDevice 3.13
|
||||
iManufacturer 3 Linux 3.13.0-39-lowlatency uhci_hcd
|
||||
iProduct 2 UHCI Host Controller
|
||||
iSerial 1 0000:00:1d.0
|
||||
bNumConfigurations 1
|
||||
Configuration Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 2
|
||||
wTotalLength 25
|
||||
bNumInterfaces 1
|
||||
bConfigurationValue 1
|
||||
iConfiguration 0
|
||||
bmAttributes 0xe0
|
||||
Self Powered
|
||||
Remote Wakeup
|
||||
MaxPower 0mA
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 0
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 1
|
||||
bInterfaceClass 9 Hub
|
||||
bInterfaceSubClass 0 Unused
|
||||
bInterfaceProtocol 0 Full speed (or root) hub
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x81 EP 1 IN
|
||||
bmAttributes 3
|
||||
Transfer Type Interrupt
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0002 1x 2 bytes
|
||||
bInterval 255
|
||||
Hub Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 41
|
||||
nNbrPorts 2
|
||||
wHubCharacteristic 0x000a
|
||||
No power switching (usb 1.0)
|
||||
Per-port overcurrent protection
|
||||
bPwrOn2PwrGood 1 * 2 milli seconds
|
||||
bHubContrCurrent 0 milli Ampere
|
||||
DeviceRemovable 0x00
|
||||
PortPwrCtrlMask 0xff
|
||||
Hub Port Status:
|
||||
Port 1: 0000.0100 power
|
||||
Port 2: 0000.0100 power
|
||||
Device Status: 0x0001
|
||||
Self Powered
|
||||
|
||||
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
|
||||
Device Descriptor:
|
||||
bLength 18
|
||||
bDescriptorType 1
|
||||
bcdUSB 2.00
|
||||
bDeviceClass 9 Hub
|
||||
bDeviceSubClass 0 Unused
|
||||
bDeviceProtocol 0 Full speed (or root) hub
|
||||
bMaxPacketSize0 64
|
||||
idVendor 0x1d6b Linux Foundation
|
||||
idProduct 0x0002 2.0 root hub
|
||||
bcdDevice 3.13
|
||||
iManufacturer 3 Linux 3.13.0-39-lowlatency ehci_hcd
|
||||
iProduct 2 EHCI Host Controller
|
||||
iSerial 1 0000:00:1a.7
|
||||
bNumConfigurations 1
|
||||
Configuration Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 2
|
||||
wTotalLength 25
|
||||
bNumInterfaces 1
|
||||
bConfigurationValue 1
|
||||
iConfiguration 0
|
||||
bmAttributes 0xe0
|
||||
Self Powered
|
||||
Remote Wakeup
|
||||
MaxPower 0mA
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 0
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 1
|
||||
bInterfaceClass 9 Hub
|
||||
bInterfaceSubClass 0 Unused
|
||||
bInterfaceProtocol 0 Full speed (or root) hub
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x81 EP 1 IN
|
||||
bmAttributes 3
|
||||
Transfer Type Interrupt
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0004 1x 4 bytes
|
||||
bInterval 12
|
||||
Hub Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 41
|
||||
nNbrPorts 6
|
||||
wHubCharacteristic 0x000a
|
||||
No power switching (usb 1.0)
|
||||
Per-port overcurrent protection
|
||||
bPwrOn2PwrGood 10 * 2 milli seconds
|
||||
bHubContrCurrent 0 milli Ampere
|
||||
DeviceRemovable 0x58
|
||||
PortPwrCtrlMask 0xff
|
||||
Hub Port Status:
|
||||
Port 1: 0000.0100 power
|
||||
Port 2: 0000.0100 power
|
||||
Port 3: 0000.0100 power
|
||||
Port 4: 0000.0100 power
|
||||
Port 5: 0000.0100 power
|
||||
Port 6: 0000.0100 power
|
||||
Device Status: 0x0001
|
||||
Self Powered
|
||||
|
||||
Bus 005 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Device Descriptor:
|
||||
bLength 18
|
||||
bDescriptorType 1
|
||||
bcdUSB 1.10
|
||||
bDeviceClass 9 Hub
|
||||
bDeviceSubClass 0 Unused
|
||||
bDeviceProtocol 0 Full speed (or root) hub
|
||||
bMaxPacketSize0 64
|
||||
idVendor 0x1d6b Linux Foundation
|
||||
idProduct 0x0001 1.1 root hub
|
||||
bcdDevice 3.13
|
||||
iManufacturer 3 Linux 3.13.0-39-lowlatency uhci_hcd
|
||||
iProduct 2 UHCI Host Controller
|
||||
iSerial 1 0000:00:1a.2
|
||||
bNumConfigurations 1
|
||||
Configuration Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 2
|
||||
wTotalLength 25
|
||||
bNumInterfaces 1
|
||||
bConfigurationValue 1
|
||||
iConfiguration 0
|
||||
bmAttributes 0xe0
|
||||
Self Powered
|
||||
Remote Wakeup
|
||||
MaxPower 0mA
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 0
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 1
|
||||
bInterfaceClass 9 Hub
|
||||
bInterfaceSubClass 0 Unused
|
||||
bInterfaceProtocol 0 Full speed (or root) hub
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x81 EP 1 IN
|
||||
bmAttributes 3
|
||||
Transfer Type Interrupt
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0002 1x 2 bytes
|
||||
bInterval 255
|
||||
Hub Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 41
|
||||
nNbrPorts 2
|
||||
wHubCharacteristic 0x000a
|
||||
No power switching (usb 1.0)
|
||||
Per-port overcurrent protection
|
||||
bPwrOn2PwrGood 1 * 2 milli seconds
|
||||
bHubContrCurrent 0 milli Ampere
|
||||
DeviceRemovable 0x04
|
||||
PortPwrCtrlMask 0xff
|
||||
Hub Port Status:
|
||||
Port 1: 0000.0100 power
|
||||
Port 2: 0000.0100 power
|
||||
Device Status: 0x0001
|
||||
Self Powered
|
||||
|
||||
Bus 004 Device 002: ID 0a5c:2145 Broadcom Corp. BCM2045B (BDC-2.1) [Bluetooth Controller]
|
||||
Device Descriptor:
|
||||
bLength 18
|
||||
bDescriptorType 1
|
||||
bcdUSB 2.00
|
||||
bDeviceClass 224 Wireless
|
||||
bDeviceSubClass 1 Radio Frequency
|
||||
bDeviceProtocol 1 Bluetooth
|
||||
bMaxPacketSize0 64
|
||||
idVendor 0x0a5c Broadcom Corp.
|
||||
idProduct 0x2145 BCM2045B (BDC-2.1) [Bluetooth Controller]
|
||||
bcdDevice 3.52
|
||||
iManufacturer 1 Lenovo Computer Corp
|
||||
iProduct 2 ThinkPad Bluetooth with Enhanced Data Rate II
|
||||
iSerial 0
|
||||
bNumConfigurations 1
|
||||
Configuration Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 2
|
||||
wTotalLength 216
|
||||
bNumInterfaces 4
|
||||
bConfigurationValue 1
|
||||
iConfiguration 0
|
||||
bmAttributes 0xe0
|
||||
Self Powered
|
||||
Remote Wakeup
|
||||
MaxPower 100mA
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 0
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 3
|
||||
bInterfaceClass 224 Wireless
|
||||
bInterfaceSubClass 1 Radio Frequency
|
||||
bInterfaceProtocol 1 Bluetooth
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x81 EP 1 IN
|
||||
bmAttributes 3
|
||||
Transfer Type Interrupt
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0010 1x 16 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x82 EP 2 IN
|
||||
bmAttributes 2
|
||||
Transfer Type Bulk
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0040 1x 64 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x02 EP 2 OUT
|
||||
bmAttributes 2
|
||||
Transfer Type Bulk
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0040 1x 64 bytes
|
||||
bInterval 1
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 1
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 2
|
||||
bInterfaceClass 224 Wireless
|
||||
bInterfaceSubClass 1 Radio Frequency
|
||||
bInterfaceProtocol 1 Bluetooth
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x83 EP 3 IN
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0000 1x 0 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x03 EP 3 OUT
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0000 1x 0 bytes
|
||||
bInterval 1
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 1
|
||||
bAlternateSetting 1
|
||||
bNumEndpoints 2
|
||||
bInterfaceClass 224 Wireless
|
||||
bInterfaceSubClass 1 Radio Frequency
|
||||
bInterfaceProtocol 1 Bluetooth
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x83 EP 3 IN
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0009 1x 9 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x03 EP 3 OUT
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0009 1x 9 bytes
|
||||
bInterval 1
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 1
|
||||
bAlternateSetting 2
|
||||
bNumEndpoints 2
|
||||
bInterfaceClass 224 Wireless
|
||||
bInterfaceSubClass 1 Radio Frequency
|
||||
bInterfaceProtocol 1 Bluetooth
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x83 EP 3 IN
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0011 1x 17 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x03 EP 3 OUT
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0011 1x 17 bytes
|
||||
bInterval 1
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 1
|
||||
bAlternateSetting 3
|
||||
bNumEndpoints 2
|
||||
bInterfaceClass 224 Wireless
|
||||
bInterfaceSubClass 1 Radio Frequency
|
||||
bInterfaceProtocol 1 Bluetooth
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x83 EP 3 IN
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0020 1x 32 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x03 EP 3 OUT
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0020 1x 32 bytes
|
||||
bInterval 1
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 1
|
||||
bAlternateSetting 4
|
||||
bNumEndpoints 2
|
||||
bInterfaceClass 224 Wireless
|
||||
bInterfaceSubClass 1 Radio Frequency
|
||||
bInterfaceProtocol 1 Bluetooth
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x83 EP 3 IN
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0040 1x 64 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x03 EP 3 OUT
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0040 1x 64 bytes
|
||||
bInterval 1
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 1
|
||||
bAlternateSetting 5
|
||||
bNumEndpoints 2
|
||||
bInterfaceClass 224 Wireless
|
||||
bInterfaceSubClass 1 Radio Frequency
|
||||
bInterfaceProtocol 1 Bluetooth
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x83 EP 3 IN
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0040 1x 64 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x03 EP 3 OUT
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0040 1x 64 bytes
|
||||
bInterval 1
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 2
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 2
|
||||
bInterfaceClass 255 Vendor Specific Class
|
||||
bInterfaceSubClass 255 Vendor Specific Subclass
|
||||
bInterfaceProtocol 255 Vendor Specific Protocol
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x84 EP 4 IN
|
||||
bmAttributes 2
|
||||
Transfer Type Bulk
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0020 1x 32 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x04 EP 4 OUT
|
||||
bmAttributes 2
|
||||
Transfer Type Bulk
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0020 1x 32 bytes
|
||||
bInterval 1
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 3
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 0
|
||||
bInterfaceClass 254 Application Specific Interface
|
||||
bInterfaceSubClass 1 Device Firmware Update
|
||||
bInterfaceProtocol 0
|
||||
iInterface 0
|
||||
Device Firmware Upgrade Interface Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 33
|
||||
bmAttributes 7
|
||||
Will Not Detach
|
||||
Manifestation Tolerant
|
||||
Upload Supported
|
||||
Download Supported
|
||||
wDetachTimeout 5000 milliseconds
|
||||
wTransferSize 64 bytes
|
||||
Device Status: 0x0001
|
||||
Self Powered
|
||||
|
||||
Bus 004 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Device Descriptor:
|
||||
bLength 18
|
||||
bDescriptorType 1
|
||||
bcdUSB 1.10
|
||||
bDeviceClass 9 Hub
|
||||
bDeviceSubClass 0 Unused
|
||||
bDeviceProtocol 0 Full speed (or root) hub
|
||||
bMaxPacketSize0 64
|
||||
idVendor 0x1d6b Linux Foundation
|
||||
idProduct 0x0001 1.1 root hub
|
||||
bcdDevice 3.13
|
||||
iManufacturer 3 Linux 3.13.0-39-lowlatency uhci_hcd
|
||||
iProduct 2 UHCI Host Controller
|
||||
iSerial 1 0000:00:1a.1
|
||||
bNumConfigurations 1
|
||||
Configuration Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 2
|
||||
wTotalLength 25
|
||||
bNumInterfaces 1
|
||||
bConfigurationValue 1
|
||||
iConfiguration 0
|
||||
bmAttributes 0xe0
|
||||
Self Powered
|
||||
Remote Wakeup
|
||||
MaxPower 0mA
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 0
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 1
|
||||
bInterfaceClass 9 Hub
|
||||
bInterfaceSubClass 0 Unused
|
||||
bInterfaceProtocol 0 Full speed (or root) hub
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x81 EP 1 IN
|
||||
bmAttributes 3
|
||||
Transfer Type Interrupt
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0002 1x 2 bytes
|
||||
bInterval 255
|
||||
Hub Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 41
|
||||
nNbrPorts 2
|
||||
wHubCharacteristic 0x000a
|
||||
No power switching (usb 1.0)
|
||||
Per-port overcurrent protection
|
||||
bPwrOn2PwrGood 1 * 2 milli seconds
|
||||
bHubContrCurrent 0 milli Ampere
|
||||
DeviceRemovable 0x06
|
||||
PortPwrCtrlMask 0xff
|
||||
Hub Port Status:
|
||||
Port 1: 0000.0100 power
|
||||
Port 2: 0000.0103 power enable connect
|
||||
Device Status: 0x0001
|
||||
Self Powered
|
||||
|
||||
Bus 003 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Device Descriptor:
|
||||
bLength 18
|
||||
bDescriptorType 1
|
||||
bcdUSB 1.10
|
||||
bDeviceClass 9 Hub
|
||||
bDeviceSubClass 0 Unused
|
||||
bDeviceProtocol 0 Full speed (or root) hub
|
||||
bMaxPacketSize0 64
|
||||
idVendor 0x1d6b Linux Foundation
|
||||
idProduct 0x0001 1.1 root hub
|
||||
bcdDevice 3.13
|
||||
iManufacturer 3 Linux 3.13.0-39-lowlatency uhci_hcd
|
||||
iProduct 2 UHCI Host Controller
|
||||
iSerial 1 0000:00:1a.0
|
||||
bNumConfigurations 1
|
||||
Configuration Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 2
|
||||
wTotalLength 25
|
||||
bNumInterfaces 1
|
||||
bConfigurationValue 1
|
||||
iConfiguration 0
|
||||
bmAttributes 0xe0
|
||||
Self Powered
|
||||
Remote Wakeup
|
||||
MaxPower 0mA
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 0
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 1
|
||||
bInterfaceClass 9 Hub
|
||||
bInterfaceSubClass 0 Unused
|
||||
bInterfaceProtocol 0 Full speed (or root) hub
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0x81 EP 1 IN
|
||||
bmAttributes 3
|
||||
Transfer Type Interrupt
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0x0002 1x 2 bytes
|
||||
bInterval 255
|
||||
Hub Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 41
|
||||
nNbrPorts 2
|
||||
wHubCharacteristic 0x000a
|
||||
No power switching (usb 1.0)
|
||||
Per-port overcurrent protection
|
||||
bPwrOn2PwrGood 1 * 2 milli seconds
|
||||
bHubContrCurrent 0 milli Ampere
|
||||
DeviceRemovable 0x00
|
||||
PortPwrCtrlMask 0xff
|
||||
Hub Port Status:
|
||||
Port 1: 0000.0100 power
|
||||
Port 2: 0000.0100 power
|
||||
Device Status: 0x0001
|
||||
Self Powered
|
||||
|
|
@ -0,0 +1 @@
|
|||
bash: msrtool: command not found
|
||||
|
|
@ -0,0 +1 @@
|
|||
bash: nvramtool: command not found
|
||||
|
|
@ -0,0 +1,8 @@
|
|||
0x16 0x042140f0
|
||||
0x17 0x61a190f0
|
||||
0x18 0x04a190f0
|
||||
0x19 0x612140f0
|
||||
0x1a 0x901701f0
|
||||
0x1b 0x40f001f0
|
||||
0x1c 0x40f001f0
|
||||
0x1d 0x90a601f0
|
||||
|
|
@ -0,0 +1 @@
|
|||
bash: superiotool: command not found
|
||||
|
|
@ -0,0 +1,54 @@
|
|||
---
|
||||
title: Apple iMac 5,2
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
iMac5,2
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Apple |
|
||||
| **Name** | iMac 17-inch "Core 2 Duo" 1.83 |
|
||||
| **Released** | 2006 |
|
||||
| **Chipset** | Intel Calistoga 945GM |
|
||||
| **CPU** | Intel Core 2 Duo T5600 |
|
||||
| **Graphics** | Intel GMA 950 |
|
||||
| **Display** | 1440x900 TFT |
|
||||
| **Memory** | 512MB, 1GB (upgradable to 2GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | Proprietary |
|
||||
| **Original boot firmware** | Apple EFI |
|
||||
| **Intel ME/AMD PSP** | Not present. |
|
||||
| **Flash chip** | SOIC-8 2MiB (Probably upgradable to 16MiB) |
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|----------------|---------------------------------------|
|
||||
| **Internal flashing with original boot firmware** | U |
|
||||
| **Display** | U |
|
||||
| **Audio** | U |
|
||||
| **RAM Init** | U |
|
||||
| **External output** | U |
|
||||
| **Display brightness** | U |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Information to be written soon, but this board is merged in libreboot.
|
||||
|
||||
This board is very similar to the [MacBook2,1](./macbook21.md).
|
||||
|
||||
Just refer back to the [hardware section](./) and [install guides](../install/)
|
||||
|
|
@ -0,0 +1,201 @@
|
|||
---
|
||||
title: Hardware compatibility list
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
Need help?
|
||||
==========
|
||||
|
||||
Help is available on [Libreboot IRC](../../contact.md) and other channels.
|
||||
|
||||
If you want professional installation, Minifree Ltd sells [Libreboot
|
||||
pre-installed](https://minifree.org/) on select hardware, and it also provides
|
||||
a [Libreboot preinstall service](https://minifree.org/product/installation-service/)
|
||||
if you want to send your machine in to have Libreboot installed for you.
|
||||
|
||||
Leah Rowe, the founder and lead developer of Libreboot, also owns and
|
||||
operates Minifree Ltd; sales provide funding for the Libreboot project.
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
**IMPORTANT ADVICE: [PLEASE READ THESE INSTRUCTIONS BEFORE INSTALLING/UPDATING
|
||||
LIBREBOOT](../../news/safety.md).**
|
||||
|
||||
This sections relates to known hardware compatibility in libreboot.
|
||||
|
||||
For installation instructions, refer to [../install/](../install/).
|
||||
|
||||
Supported hardware
|
||||
==================
|
||||
|
||||
libreboot currently supports the following systems in this release:
|
||||
|
||||
### Servers (AMD, x86)
|
||||
|
||||
- [ASUS KFSN4-DRE motherboard](kfsn4-dre.md)
|
||||
- [ASUS KGPE-D16 motherboard](kgpe-d16.md)
|
||||
|
||||
### Desktops (AMD, Intel, x86)
|
||||
|
||||
- **[Dell OptiPlex 7020/9020 MT and SFF](dell9020.md) - Also [available to buy
|
||||
with Libreboot preinstalled](https://minifree.org/product/libreboot-9020/)** - Dell OptiPlex XE2 MT/SFF also known to work
|
||||
- [Acer G43T-AM3](acer_g43t-am3.md)
|
||||
- [Apple iMac 5,2](imac52.md)
|
||||
- [ASUS KCMA-D8 motherboard](kcma-d8.md)
|
||||
- Dell OptiPlex 7010 **MT** (known to work, using the T1650 ROM, but more
|
||||
research is needed)
|
||||
- [Dell Precision T1650](t1650.md)
|
||||
- [Gigabyte GA-G41M-ES2L motherboard](ga-g41m-es2l.md)
|
||||
- [HP Elite 8200 SFF/MT](hp8200sff.md) (HP 6200 Pro Business probably works too)
|
||||
- [HP Elite 8300 USDT](hp8300usdt.md)
|
||||
- [Intel D510MO and D410PT motherboards](d510mo.md)
|
||||
- [Intel D945GCLF](d945gclf.md)
|
||||
|
||||
### Laptops (Intel, x86)
|
||||
|
||||
- **[HP EliteBook 820 G2](hp820g2.md) - Also [available to buy with Libreboot
|
||||
preinstalled](https://minifree.org/product/libreboot-820/)**
|
||||
- **[Lenovo ThinkPad T440p](../install/t440p_external.md) - Also [available
|
||||
to buy with Libreboot preinstalled](https://minifree.org/product/libreboot-t440p/)**
|
||||
- **[Lenovo ThinkPad W541](../install/ivy_has_common.md) - Also [available to
|
||||
buy with Libreboot preinstalled](https://minifree.org/product/libreboot-w541/)**
|
||||
- [Apple MacBook1,1 and MacBook2,1](macbook21.md)
|
||||
- [Dell Latitude E6400, E6400 XFR and E6400 ATG, all with Nvidia or Intel
|
||||
GPU](e6400.md)
|
||||
- [Dell Latitude E6420 (Intel GPU](e6420.md)
|
||||
- [Dell Latitude E6430 (Intel GPU](e6430.md)
|
||||
- [Dell Latitude E5520 (Intel GPU](e5520.md)
|
||||
- [Dell Latitude E5530 (Intel GPU](e5530.md)
|
||||
- [Dell Latitude E6520 (Intel GPU](e6520.md)
|
||||
- [Dell Latitude E6530 (Intel GPU](e6530.md)
|
||||
- [HP EliteBook 2170p](hp2170p.md)
|
||||
- [HP EliteBook 2560p](hp2560p.md)
|
||||
- [HP EliteBook 2570p](hp2570p.md)
|
||||
- [HP EliteBook 8460p](hp8460p.md)
|
||||
- [HP EliteBook 8470p](hp8470p.md)
|
||||
- [HP EliteBook 8560w](hp8560w.md)
|
||||
- [HP EliteBook Folio 9470m](hp9470m.md)
|
||||
- [Lenovo ThinkPad R400](r400.md)
|
||||
- [Lenovo ThinkPad R500](r500.md)
|
||||
- [Lenovo ThinkPad T400 / T400S](t400.md)
|
||||
- [Lenovo Thinkpad T420](../install/ivy_has_common.md) (no install docs yet)
|
||||
- [Lenovo ThinkPad T420S](../install/ivy_has_common.md) (no install docs yet)
|
||||
- [Lenovo ThinkPad T430](../install/ivy_has_common.md) (no install docs yet)
|
||||
- [Lenovo ThinkPad T500](t500.md)
|
||||
- [Lenovo ThinkPad T520 / W520](../install/ivy_has_common.md) (no install guide yet)
|
||||
- [Lenovo ThinkPad T530 / W530](../install/ivy_has_common.md) (no install
|
||||
- Lenovo ThinkPad T60 (with Intel GPU)
|
||||
- [Lenovo ThinkPad W500](t500.md)
|
||||
- [Lenovo ThinkPad X200 / X200S / X200 Tablet](x200.md)
|
||||
- [Lenovo Thinkpad X220](../install/ivy_has_common.md)
|
||||
- [Lenovo Thinkpad X220t](../install/ivy_has_common.md)
|
||||
- Lenovo ThinkPad X230
|
||||
- [Lenovo Thinkpad X230](../install/x230_external.md)
|
||||
- [Lenovo Thinkpad X230t](../install/x230_external.md)
|
||||
- Lenovo ThinkPad X301
|
||||
- Lenovo ThinkPad X60 / X60S / X60 Tablet
|
||||
|
||||
### Laptops (ARM, with U-Boot payload)
|
||||
|
||||
- [ASUS Chromebook Flip C101 (gru-bob)](../install/chromebooks.md)
|
||||
- [Samsung Chromebook Plus (v1) (gru-kevin)](../install/chromebooks.md)
|
||||
|
||||
## Removed boards
|
||||
|
||||
These boards were in Libreboot, but have been removed with the intention of
|
||||
re-adding them at a later date. They were removed due to issues. List:
|
||||
|
||||
- [Acer Chromebook 13 (CB5-311, C810) (nyan-big)](../install/chromebooks.md)
|
||||
- [ASUS Chromebit CS10 (veyron-mickey)](../install/chromebooks.md)
|
||||
- [ASUS Chromebook C201PA (veyron-speedy)](../install/c201.md)
|
||||
- [ASUS Chromebook Flip C100PA (veyron-minnie)](../install/chromebooks.md)
|
||||
- [Hisense Chromebook C11 and more (veyron-jerry)](../install/chromebooks.md)
|
||||
- [HP Chromebook 11 G1 (daisy-spring)](../install/chromebooks.md)
|
||||
- [HP Chromebook 14 G3 (nyan-blaze)](../install/chromebooks.md)
|
||||
- [Samsung Chromebook 2 11" (peach-pit)](../install/chromebooks.md)
|
||||
- [Samsung Chromebook 2 13" (peach-pi)](../install/chromebooks.md)
|
||||
- [Samsung Chromebook XE303 (daisy-snow)](../install/chromebooks.md)
|
||||
|
||||
### NOTES about removed boards:
|
||||
|
||||
**WARNING: veyron speedy boards (e.g. C201) have non-functional video init as
|
||||
of 19 February 2023, and no fix is yet available on that date. See:
|
||||
<https://notabug.org/libreboot/lbmk/issues/136> - the last tested revision
|
||||
from 2021.01 is known to work, for u-boot on this board. See:\
|
||||
<https://wiki.postmarketos.org/wiki/ASUS_Chromebook_C201_(google-veyron-speedy)>
|
||||
(alpernebbi on IRC is looking into this, to bisect uboot and update the latest
|
||||
revisions) - for now, ROM images deleted from the Libreboot 20221214
|
||||
and 20230319 releases.**
|
||||
|
||||
**WARNING: daisy- and peach- boards require a BL1 bootloader firmware, but the
|
||||
one from coreboot 3rdparty is a fake/placeholder file. We need logic in the
|
||||
Libreboot build system for properly fetching/extracting these, plus docs to
|
||||
cover it. For now, assume that these are broken - ROM images are excluded,
|
||||
for now, and have been deleted from the Libreboot 20221214 and 20230319
|
||||
releases. - see: <https://review.coreboot.org/plugins/gitiles/blobs/+/4c0dcf96ae73ba31bf9aa689768a5ecd47bac19e>
|
||||
and <https://review.coreboot.org/plugins/gitiles/blobs/+/b36cc7e08f7337f76997b25ee7344ab8824e268d>**
|
||||
|
||||
d945gclf: Doesn't boot at all, according to last report. D510MO is still in
|
||||
lbmk but still was reported problematic; other boards should be fine (see list
|
||||
above).
|
||||
|
||||
WARNING: Support for these boards is at a proof-of-concept stage. Refer
|
||||
to [docs/uboot/](../uboot/) for more info about the U-Boot payload.
|
||||
|
||||
### Emulation
|
||||
|
||||
- [Qemu x86](../misc/emulation.md)
|
||||
- [Qemu arm64](../misc/emulation.md)
|
||||
|
||||
|
||||
TODO: More hardware is supported. See `config/coreboot/` in lbmk. Update
|
||||
the above list!
|
||||
|
||||
'Supported' means that the build scripts know how to build ROM images
|
||||
for these systems, and that the systems have been tested (confirmed
|
||||
working). There may be exceptions; in other words, this is a list of
|
||||
'officially' supported systems.
|
||||
|
||||
EC update on i945 (X60, T60) and GM45 (X200, X301, T400, T500, R400, W500, R500)
|
||||
==============================================================
|
||||
|
||||
It is recommended that you update to the latest EC firmware version. The
|
||||
[EC firmware](../../faq.md#ec-embedded-controller-firmware) is separate from
|
||||
libreboot, so we don't actually provide that, but if you still have
|
||||
Lenovo BIOS then you can just run the Lenovo BIOS update utility, which
|
||||
will update both the BIOS and EC version. See:
|
||||
|
||||
- [../install/#flashprog](../install/#flashprog)
|
||||
- <http://www.thinkwiki.org/wiki/BIOS_update_without_optical_disk>
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
||||
NOTE: this can only be done when you are using Lenovo BIOS. How to
|
||||
update the EC firmware while running libreboot is unknown. libreboot
|
||||
only replaces the BIOS firmware, not EC.
|
||||
|
||||
Updated EC firmware has several advantages e.g. better battery
|
||||
handling.
|
||||
|
||||
How to find what EC version you have (i945/GM45)
|
||||
------------------------------------------------
|
||||
|
||||
In Linux, you can try this:
|
||||
|
||||
grep 'at EC' /proc/asound/cards
|
||||
|
||||
Sample output:
|
||||
|
||||
ThinkPad Console Audio Control at EC reg 0x30, fw 7WHT19WW-3.6
|
||||
|
||||
7WHT19WW is the version in different notation, use search engine to find
|
||||
out regular version - in this case it's a 1.06 for x200 tablet
|
||||
|
||||
Alternatively, if `dmidecode` is available, run the following command (as `root`) to
|
||||
find the currently flashed BIOS version:
|
||||
|
||||
dmidecode -s bios-version
|
||||
|
||||
On a T400 running the latest BIOS this would give `7UET94WW (3.24 )` as result.
|
||||
|
|
@ -0,0 +1,181 @@
|
|||
---
|
||||
title: 兼容硬件列表
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
Need help?
|
||||
==========
|
||||
|
||||
Help is available on [Libreboot IRC](../../contact.md) and other channels.
|
||||
|
||||
If you want professional installation, Minifree Ltd sells [Libreboot
|
||||
pre-installed](https://minifree.org/) on select hardware, and it also provides
|
||||
a [Libreboot preinstall service](https://minifree.org/product/installation-service/)
|
||||
if you want to send your machine in to have Libreboot installed for you.
|
||||
|
||||
Leah Rowe, the founder and lead developer of Libreboot, also owns and
|
||||
operates Minifree Ltd; sales provide funding for the Libreboot project.
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
**[安装之前请先阅读这些指示](../../news/safety.md),否则你的机器可能会变砖:[安全措施](../../news/safety.md)**
|
||||
|
||||
这一部分说明了 libreboot 已知兼容的硬件。
|
||||
|
||||
安装指南,请参看 [../install/](../install/)。
|
||||
|
||||
注意:对 T60/R60 thinkpad 而言,请确认它拥有的是 Intel GPU 而非 ATI GUI,因为 coreboot 对这些机器缺少 ATI GPU 的原生图像初始化。
|
||||
|
||||
(对 T500、T400 等后续机器而言,有 ATI GPU 也没问题,因为它也有 Intel GPU,而 libreboot 会用 Intel 的)
|
||||
|
||||
更新 LIBREBOOT 前请先阅读这里,否则你的机器可能会成变砖
|
||||
====================================================================
|
||||
|
||||
**有些新的 Intel 平台需要 Intel ME 和/或 MRC 固件(例如 ThinkPad X230 或 T440p),还有些 HP 笔记本需要 KBC1126 EC 固件。对上述机器而言,Libreboot 官方发布的 ROM 缺少了特定的文件,你必须自己加入进去。如果无视这则警告,而坚持在不修改的情况下刷入官方发布的 ROM,那你可能会让你的机器变砖(导致它无法启动)。详请阅读:**
|
||||
|
||||
**[在 Sandybridge/Ivybridge/Haswell 插入二进制 blob](../install/ivy_has_common.md)**
|
||||
|
||||
注意:如果你是自己使用 lbmk 编译的 ROM,则不用在意这条警告。它只针对官方发布的 ROM,因为这些 ROM 里删除了 ME/MRC/EC 固件。上面的链接讲解了怎么把它们加回去。如果是自己从源代码构建 ROM 镜像,Libreboot 的构建系统会自动处理的。见:[Libreboot 构建指南](../build/)
|
||||
|
||||
已支持的硬件
|
||||
==================
|
||||
|
||||
该版本的 libreboot 目前支持以下机器:
|
||||
|
||||
### 服务器(AMD,x86)
|
||||
|
||||
- [ASUS KFSN4-DRE 主板](kfsn4-dre.md)
|
||||
- [ASUS KGPE-D16 主板](kgpe-d16.md)
|
||||
|
||||
### Desktops (AMD, Intel, x86)
|
||||
|
||||
- **Dell OptiPlex 7020/9020 MT and SFF (no guides yet) - [Available to buy
|
||||
with Libreboot preinstalled](https://minifree.org/product/libreboot-9020/)**
|
||||
- [Acer G43T-AM3](acer_g43t-am3.md)
|
||||
- [Apple iMac 5,2](imac52.md)
|
||||
- [ASUS KCMA-D8 主板](kcma-d8.md)
|
||||
- Dell OptiPlex 7010 **MT** (known to work, using the T1650 ROM, but more
|
||||
research is needed)
|
||||
- [Dell Precision T1650](t1650.md)
|
||||
- [Gigabyte GA-G41M-ES2L 主板](ga-g41m-es2l.md)
|
||||
- [HP Elite 8200 SFF/MT](hp8200sff.md)(HP 6200 Pro Business 多半也能用)
|
||||
- [HP Elite 8300 USDT](hp8300usdt.md)
|
||||
- [Intel D510MO 及 D410PT 主板](d510mo.md)
|
||||
- [Intel D945GCLF](d945gclf.md)(移出 lbmk,计划:重新加入支持)
|
||||
|
||||
### 笔记本(Intel,x86)
|
||||
|
||||
- **[HP EliteBook 820 G2](hp820g2.md) - Also [available to buy with Libreboot
|
||||
preinstalled](https://minifree.org/product/libreboot-820/)**
|
||||
- **[Lenovo ThinkPad T440p](../install/t440p_external.md) - Also [available
|
||||
to buy with Libreboot preinstalled](https://minifree.org/product/libreboot-t440p/)**
|
||||
- **[Lenovo ThinkPad W541](../install/ivy_has_common.md) - Also [available to
|
||||
buy with Libreboot preinstalled](https://minifree.org/product/libreboot-w541/)**
|
||||
- [Apple MacBook1,1 及 MacBook2,1](macbook21.md)
|
||||
- [Dell Latitude E6400, E6400 XFR 及 E6400 ATG,皆支持 Nvidia 或 Intel GPU](e6400.md)
|
||||
- Dell Latitude E6420 (Intel GPU) - no guide yet.
|
||||
- [Dell Latitude E6430, Intel GPU](e6430.md)
|
||||
- Dell Latitude E5530 (Intel GPU) - no guide yet.
|
||||
- Dell Latitude E6520 (Intel GPU) - no guide yet.
|
||||
- [HP EliteBook 2170p](hp2170p.md)
|
||||
- [HP EliteBook 2560p](hp2560p.md)
|
||||
- [HP EliteBook 2570p](hp2570p.md)
|
||||
- [HP EliteBook 8460p](hp8460p.md)
|
||||
- [HP EliteBook 8470p](hp8470p.md)
|
||||
- [HP EliteBook 8560w](hp8560w.md)
|
||||
- [HP EliteBook Folio 9470m](hp9470m.md)
|
||||
- [Lenovo ThinkPad R400](r400.md)
|
||||
- [Lenovo ThinkPad R500](r500.md)
|
||||
- [Lenovo ThinkPad T400 / T400S](t400.md)
|
||||
- [Lenovo Thinkpad T420](../install/ivy_has_common.md)(暂无安装文档)
|
||||
- [Lenovo ThinkPad T420S](../install/ivy_has_common.md)(暂无安装文档)
|
||||
- [Lenovo ThinkPad T430](../install/ivy_has_common.md)(暂无安装文档)
|
||||
- [Lenovo ThinkPad T500](t500.md)
|
||||
- [Lenovo ThinkPad T530 / W530](../install/ivy_has_common.md)(暂无安装文档)
|
||||
- Lenovo ThinkPad T60(Intel GPU 款)
|
||||
- [Lenovo ThinkPad W500](t500.md)
|
||||
- [Lenovo ThinkPad X200 / X200S / X200 Tablet](x200.md)
|
||||
- [Lenovo Thinkpad X220](../install/ivy_has_common.md)
|
||||
- [Lenovo Thinkpad X220t](../install/ivy_has_common.md)
|
||||
- Lenovo ThinkPad X230
|
||||
- [Lenovo Thinkpad X230](../install/x230_external.md)
|
||||
- [Lenovo Thinkpad X230t](../install/x230_external.md)
|
||||
- Lenovo ThinkPad X301
|
||||
- Lenovo ThinkPad X60 / X60S / X60 Tablet
|
||||
|
||||
### 笔记本(ARM,配 U-Boot payload)
|
||||
|
||||
- [ASUS Chromebook Flip C101 (gru-bob)](../install/chromebooks.md)
|
||||
- [Samsung Chromebook Plus (v1) (gru-kevin)](../install/chromebooks.md)
|
||||
|
||||
## 已移除的主板
|
||||
|
||||
这些主板 Libreboot 以前支持,但现在移除了,计划在以后重新加回来。它们之所以被移除,是因为出现了问题。主板列表:
|
||||
|
||||
- [HP Chromebook 14 G3 (nyan-blaze)](../install/chromebooks.md)
|
||||
- [Acer Chromebook 13 (CB5-311, C810) (nyan-big)](../install/chromebooks.md)
|
||||
- [Hisense Chromebook C11 and more (veyron-jerry)](../install/chromebooks.md)
|
||||
- [Samsung Chromebook 2 13" (peach-pi)](../install/chromebooks.md)
|
||||
- [Samsung Chromebook 2 11" (peach-pit)](../install/chromebooks.md)
|
||||
- [HP Chromebook 11 G1 (daisy-spring)](../install/chromebooks.md)
|
||||
- [Samsung Chromebook XE303 (daisy-snow)](../install/chromebooks.md)
|
||||
- [ASUS Chromebit CS10 (veyron-mickey)](../install/chromebooks.md)
|
||||
- [ASUS Chromebook Flip C100PA (veyron-minnie)](../install/chromebooks.md)
|
||||
- [ASUS Chromebook C201PA (veyron-speedy)](../install/c201.md)
|
||||
|
||||
### 关于已移除的主板
|
||||
|
||||
**警告:2023 年 2 月 19 日,veyron speedy 主板(例如 C201)的图像初始化无法工作,截至该时还没有解决方案。见 <https://notabug.org/libreboot/lbmk/issues/136> —— 2021.01 的最后一个测试过的版本,这个带 u-boot 的主板是可以工作的。见:\
|
||||
<https://wiki.postmarketos.org/wiki/ASUS_Chromebook_C201_(google-veyron-speedy)>
|
||||
(IRC 上的 alpernebbi 正在研究这个问题,二分法排查 uboot 并更新最新的版本)——目前,Libreboot 20221214 和 20230309 的 ROM 镜像已经删除。**
|
||||
|
||||
**警告:daisy- 和 peach- 主板需要 B1 bootloader blob,但 coreboot 第三方有一个假的/占位的 blob。我们需要在 Libreboot 构建系统中实现一套逻辑,正确获取/提取这些 blob,并为其编写文档。目前的话,就假定它们是损坏的——ROM 镜像目前已经排除,并在 Libreboot 20221214 和 20230309 中删除。——见:<https://review.coreboot.org/plugins/gitiles/blobs/+/4c0dcf96ae73ba31bf9aa689768a5ecd47bac19e> 及 <https://review.coreboot.org/plugins/gitiles/blobs/+/b36cc7e08f7337f76997b25ee7344ab8824e268d>**
|
||||
|
||||
d945gclf:据上次报告,根本无法启动。D510MO 仍在 lbmk 中,但仍然报告有问题;其他主板应该没问题(见上方列表)。
|
||||
|
||||
警告:这些主板的支持,还处于概念验证阶段。参考 [docs/uboot/](../uboot/) 了解 U-boot payload 的更多信息。
|
||||
|
||||
### 模拟
|
||||
|
||||
- [Qemu x86](../misc/emulation.md)
|
||||
- [Qemu arm64](../misc/emulation.md)
|
||||
|
||||
|
||||
计划:支持更多硬件。见 lbmk 中的 `config/coreboot/`。更新上面的列表!
|
||||
|
||||
所谓“支持”,即指构建脚本知道如何构建这些机器的 ROM 镜像,并且机器经过测试(确认能够工作)。也可能会有例外;换言之,这是“官方”支持的机器列表。
|
||||
|
||||
在 i945(X60、T60)及 GM45(X200、X301、T400、T500、R400、W500、R500)上更新 EC
|
||||
==============================================================
|
||||
|
||||
建议更新到最新 EC 固件版本。[EC 固件](../../faq.md#ec-embedded-controller-firmware) 与 libreboot 是独立的,所以我们实际上并不会提供这些固件,但如果你仍还有 Lenovo BIOS,那你可以直接运行 Lenovo BIOS 更新工具,它会同时更新 BIOS 和 EC 版本。见:
|
||||
|
||||
- [../install/#flashprog](../install/#flashprog)
|
||||
- <http://www.thinkwiki.org/wiki/BIOS_update_without_optical_disk>
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
||||
注意:只有在运行 Lenovo BIOS 的时候,你才能这样做。如何在运行 libreboot 的时候更新 EC 固件尚不清楚。libreboot 只会替换 BIOS 固件,而不会替换 EC。
|
||||
|
||||
更新的 EC 固件有一些好处,例如电池管理更加好。
|
||||
|
||||
如何得知你的 EC 版本(i945/GM45)
|
||||
------------------------------------------------
|
||||
|
||||
在 Linux,你可以试试这条命令:
|
||||
|
||||
grep 'at EC' /proc/asound/cards
|
||||
|
||||
输出样例:
|
||||
|
||||
ThinkPad Console Audio Control at EC reg 0x30, fw 7WHT19WW-3.6
|
||||
|
||||
7WHT19WW 另一种形式的版本号,使用搜索引擎来找出正常的版本号——这个例子中的 x200 tablet,版本号是 1.06。
|
||||
|
||||
或者,如果能用 `dmidecode`,则(以 `root`)运行以下命令,来得知目前刷入的 BIOS 版本:
|
||||
|
||||
dmidecode -s bios-version
|
||||
|
||||
运行最新 BIOS 的 T400 上,它的输出结果为 `7UET94WW (3.24 )`。
|
||||
|
|
@ -0,0 +1,215 @@
|
|||
---
|
||||
title: ASUS KGPE-D16 server/workstation board
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
TODO: OLD page. TODO: check that all the info is still valid.
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
This is a server board using AMD hardware (Fam10h *and Fam15h* CPUs
|
||||
available). It can also be used for building a high-powered workstation.
|
||||
Powered by libreboot. The coreboot port was done by Timothy Pearson of
|
||||
Raptor Engineering Inc. and, working with them (and sponsoring the
|
||||
work), merged into libreboot.
|
||||
|
||||
*Memory initialization is still problematic, for some modules. We
|
||||
recommend avoiding Kingston modules.*
|
||||
*For working configurations see <https://www.coreboot.org/Board:asus/kgpe-d16>.*
|
||||
|
||||
Flashing instructions can be found at
|
||||
[../install/\#flashprog](../install/#flashprog) - note that external
|
||||
flashing is required, if the proprietary (ASUS) firmware is
|
||||
currently installed. If you already have libreboot, by default it is
|
||||
possible to re-flash using software running in Linux on the
|
||||
KGPE-D16, without using external hardware.
|
||||
|
||||
CPU compatibility
|
||||
=================
|
||||
|
||||
Opteron 62xx and 63xx CPUs work just fine.
|
||||
|
||||
Board status (compatibility) {#boardstatus}
|
||||
============================
|
||||
|
||||
See <https://raptorengineeringinc.com/coreboot/kgpe-d16-status.php>.
|
||||
|
||||
Form factor {#formfactor}
|
||||
===========
|
||||
|
||||
These boards use the SSI EEB 3.61 form factor; make sure that your case
|
||||
supports this. This form factor is similar to E-ATX in that the size is
|
||||
identical, but the position of the screws are different.
|
||||
|
||||
IPMI iKVM module add-on {#ipmi}
|
||||
=======================
|
||||
|
||||
Don't use it. It uses proprietary firmware and adds a backdoor (remote
|
||||
out-of-band management chip, similar to the [Intel Management
|
||||
Engine](../../faq.md#intelme). Fortunately, the firmware is
|
||||
unsigned (possibly to replace) and physically separate from the
|
||||
mainboard since it's on the add-on module, which you don't have to
|
||||
install.
|
||||
|
||||
Flash chips {#flashchips}
|
||||
===========
|
||||
|
||||
2MiB flash chips are included by default, on these boards. It's on a
|
||||
P-DIP 8 slot (SPI chip). The flash chip can be upgraded to higher sizes:
|
||||
4MiB, 8MiB or 16MiB. With at least 8MiB, you could feasibly fit a
|
||||
compressed linux+initramfs image (BusyBox+Linux system) into CBFS and
|
||||
boot that, loading it into memory.
|
||||
|
||||
libreboot has configs for 2, 4, 8 and 16 MiB flash chip sizes (default
|
||||
flash chip is 2MiB).
|
||||
|
||||
*DO NOT hot-swap the chip with your bare hands. Use a P-DIP 8 chip
|
||||
extractor. These can be found online. See
|
||||
<http://www.coreboot.org/Developer_Manual/Tools#Chip_removal_tools>*
|
||||
|
||||
This guide shows how to flash the chip:\
|
||||
[25xx NOR flashing guide](../install/spi.md)
|
||||
|
||||
Native graphics initialization {#graphics}
|
||||
==============================
|
||||
|
||||
Only text-mode is known to work, but linux(kernel) can initialize the
|
||||
framebuffer display (if it has KMS - kernel mode setting).
|
||||
|
||||
Current issues {#issues}
|
||||
==============
|
||||
|
||||
- LRDIMM memory modules are currently incompatible
|
||||
(IT MAY WORK NOWADAYS, TODO TEST)
|
||||
- SAS (via PIKE 2008 module) requires a vendor option ROM (and
|
||||
SeaBIOS) to boot from it (theoretically possible to replace, but you
|
||||
can put a kernel in CBFS or on SATA and boot from that, which
|
||||
can be on a SAS drive. The linux kernel can use those SAS drives
|
||||
(via PIKE module) without an option ROM).
|
||||
- SeaBIOS lacked serial console support out-of-the-box in release 20160907
|
||||
and as such a workaround using SGABIOS is necessary. You can find
|
||||
instructions on how to do this on the
|
||||
[Notabug issue tracker](http://web.archive.org/web/20210416011941/https://notabug.org/libreboot/libreboot/issues/736)
|
||||
- IPMI iKVM module (optional add-on card) uses proprietary firmware.
|
||||
Since it's for remote out-of-band management, it's theoretically a
|
||||
backdoor similar to the Intel Management Engine. Fortunately, unlike
|
||||
the ME, this firmware is unsigned which means that a free
|
||||
replacement is theoretically possible. For now, the libreboot
|
||||
project recommends not installing the module. [This
|
||||
project](https://github.com/facebook/openbmc) might be interesting
|
||||
to derive from, for those who want to work on a free replacement. In
|
||||
practise, out-of-band management isn't very useful anyway (or at
|
||||
the very least, it's not a major inconvenience to not have it).
|
||||
- Graphics: only text-mode works. See [\#graphics](#graphics)
|
||||
|
||||
Hardware specifications {#specifications}
|
||||
-----------------------
|
||||
|
||||
The information here is adapted, from the ASUS website.
|
||||
|
||||
### Processor / system bus
|
||||
|
||||
- 2 CPU sockets (G34 compatible)
|
||||
- HyperTransport™ Technology 3.0
|
||||
- CPUs supported:
|
||||
- AMD Opteron 6100 series (Fam10h. No IOMMU support. *Not*
|
||||
recommended - old. View errata datasheet here:
|
||||
<http://support.amd.com/TechDocs/41322_10h_Rev_Gd.pdf>)
|
||||
- AMD Opteron 6200 series (Fam15h, with full IOMMU support in
|
||||
libreboot.
|
||||
- AMD Opteron 6300 series (Fam15h, with full IOMMU support in
|
||||
libreboot.
|
||||
- 6.4 GT/s per link (triple link)
|
||||
|
||||
### Core logic
|
||||
|
||||
- AMD SR5690
|
||||
- AMD SP5100
|
||||
|
||||
### Memory compatibility (with libreboot)
|
||||
|
||||
- *Total Slots:* 16 (4-channel per CPU, 8 DIMM per CPU), ECC
|
||||
- *Capacity:* Maximum up to 256GB RDIMM (Tested max 128GB)
|
||||
- *Memory Type that is compatible:*
|
||||
- DDR3 1600/1333/1066/800 UDIMM\*
|
||||
- DDR3 1600/1333/1066/800 RDIMM\*
|
||||
- *Compatible sizes per memory module:*
|
||||
- 16GB, 8GB, 4GB, 3GB, 2GB, 1GB RDIMM
|
||||
- 8GB, 4GB, 2GB, 1GB UDIMM
|
||||
|
||||
### Expansion slots
|
||||
|
||||
- *Total slot:* 6
|
||||
- *Slot Location 1:* PCI 32bit/33MHz
|
||||
- *Slot Location 2:* PCI-E x16 (Gen2 X8 Link)
|
||||
- *Slot Location 3:* PCI-E x16 (Gen2 X16 Link), Auto switch to x8
|
||||
link if slot 2 is occupied
|
||||
- *Slot Location 4:* PCI-E x8 (Gen2 X4 Link)
|
||||
- *Slot Location 5:* PCI-E x16 (Gen2 X16 Link)
|
||||
- *Slot Location 6:* PCI-E x16 (Gen2 X16 Link), Auto turn off if
|
||||
slot 5 is occupied, For 1U FH/FL Card, MIO supported
|
||||
- *Additional Slot 1:* PIKE slot (for SAS drives. See notes above)
|
||||
- Follow SSI Location\#
|
||||
|
||||
### Form factor {#form-factor}
|
||||
|
||||
- SSI EEB 3.61 (12"x13")
|
||||
|
||||
### ASUS features
|
||||
|
||||
- Fan Speed Control
|
||||
- Rack Ready (Rack and Pedestal dual use)
|
||||
|
||||
### Storage
|
||||
|
||||
- *SATA controller:*
|
||||
- AMD SP5100
|
||||
- 6 x SATA2 300MB/s
|
||||
- *SAS/SATA Controller:*
|
||||
- ASUS PIKE2008 3Gbps 8-port SAS card included
|
||||
|
||||
### Networking
|
||||
|
||||
- 2 x Intel® 82574L + 1 x Mgmt LAN
|
||||
|
||||
### Graphics
|
||||
|
||||
- Aspeed AST2050 with 8MB VRAM
|
||||
|
||||
### On board I/O
|
||||
|
||||
- 1 x PSU Power Connector (24-pin SSI power connector + 8-pin SSI
|
||||
12V + 8-pin SSI 12V power connector)
|
||||
- 1 x Management Connector , Onboard socket for management card
|
||||
- 3 x USB pin header , Up to 6 Devices
|
||||
- 1 x Internal A Type USB Port
|
||||
- 8 x Fan Header , 4pin (3pin/4pin fan dual support)
|
||||
- 2 x SMBus
|
||||
- 1 x Serial Port Header
|
||||
- 1 x TPM header
|
||||
- 1 x PS/2 KB/MS port
|
||||
|
||||
### Back I/O ports
|
||||
|
||||
- 1 x External Serial Port
|
||||
- 2 x External USB Port
|
||||
- 1 x VGA Port
|
||||
- 2 x RJ-45
|
||||
- 1 x PS/2 KB/Mouse
|
||||
|
||||
### Environment
|
||||
|
||||
- *Operation temperature:* 10C \~ 35C
|
||||
- *Non operation temperature:* -40C \~ 70C
|
||||
- *Non operation humidity:* 20% \~ 90% ( Non condensing)
|
||||
|
||||
### Monitoring
|
||||
|
||||
- CPU temperatures
|
||||
- Fan speed (RPM)
|
||||
|
||||
### Note:
|
||||
|
||||
- \* DDR3 1600 can only be supported with AMD Opteron 6300/6200 series
|
||||
processor
|
||||
|
|
@ -0,0 +1,108 @@
|
|||
---
|
||||
title: ThinkPad R400
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
![ThinkPad R400]()
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Lenovo |
|
||||
| **Name** | ThinkPad R400 |
|
||||
| **Released** | 2009 |
|
||||
| **Chipset** | Intel Cantiga GM45 |
|
||||
| **CPU** | Intel Core 2 Duo (Penryn/Merom family) or
|
||||
Celeron M (Merom L family) |
|
||||
| **Graphics** | Intel GMA 4500MHD (and ATI Mobility Radeon HD
|
||||
3470 or nVIDIA
|
||||
GeForce 9300M on some models) |
|
||||
| **Display** | 1280x800/1440x900 TFT |
|
||||
| **Memory** | Up to 8GB |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | Proprietary |
|
||||
| **Original boot firmware** | LenovoBIOS |
|
||||
| **Intel ME/AMD PSP** | Present. Can be completly disabled. |
|
||||
| **Flash chip** | SOIC-8/SOIC-16 4MiB/8MiB (Upgradable to 16MiB) |
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|----------------|---------------------------------------|
|
||||
| **Internal flashing with original boot firmware** | N |
|
||||
| **Display** | W+ |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Dell Latitude E6400
|
||||
===================
|
||||
|
||||
**If you haven't bought an R400 yet: the [Dell Latitude
|
||||
E6400](../../news/e6400.md) is much easier to flash; no disassembly required,
|
||||
it can be flashed entirely in software from Dell BIOS to Libreboot. It is the
|
||||
same hardware generation (GM45), with same CPUs, video processor, etc.**
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
It is believed that all or most R400 laptops are compatible. See notes
|
||||
about [CPU
|
||||
compatibility](../install/r400_external.html#cpu_compatibility) for
|
||||
potential incompatibilities.
|
||||
|
||||
There are two possible flash chip sizes for the R400: 4MiB (32Mbit) or
|
||||
8MiB (64Mbit). This can be identified by the type of flash chip below
|
||||
the palmrest: 4MiB is SOIC-8, 8MiB is SOIC-16.
|
||||
|
||||
*The R400 laptops come with the ME (and sometimes AMT in addition)
|
||||
before flashing libreboot. libreboot disables and removes it by using a
|
||||
modified descriptor: see [../install/ich9utils.md](../install/ich9utils.md)*
|
||||
(contains notes, plus instructions)
|
||||
|
||||
Flashing instructions can be found at
|
||||
[../install/\#flashprog](../install/#flashprog)
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
||||
EC update {#ecupdate}
|
||||
=========
|
||||
|
||||
It is recommended that you update to the latest EC firmware version. The
|
||||
[EC firmware](../../faq.md#ec-embedded-controller-firmware) is separate from
|
||||
libreboot, so we don't actually provide that, but if you still have
|
||||
Lenovo BIOS then you can just run the Lenovo BIOS update utility, which
|
||||
will update both the BIOS and EC version. See:
|
||||
|
||||
- [../install/#flashprog](../install/#flashprog)
|
||||
- <http://www.thinkwiki.org/wiki/BIOS_update_without_optical_disk>
|
||||
|
||||
NOTE: this can only be done when you are using Lenovo BIOS. How to
|
||||
update the EC firmware while running libreboot is unknown. libreboot
|
||||
only replaces the BIOS firmware, not EC.
|
||||
|
||||
Updated EC firmware has several advantages e.g. bettery battery
|
||||
handling.
|
||||
|
||||
The R400 is almost identical to the X200, code-wise. See
|
||||
[x200.md](x200.md).
|
||||
|
||||
TODO: put hardware register logs here like on the [X200](x200.md) and
|
||||
[T400](t400.md) page.
|
||||
|
|
@ -0,0 +1,81 @@
|
|||
---
|
||||
title: ThinkPad R500
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
![ThinkPad R500]()
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Lenovo |
|
||||
| **Name** | ThinkPad R500 |
|
||||
| **Released** | 2009 |
|
||||
| **Chipset** | Intel Cantiga GM45 |
|
||||
| **CPU** | Intel Core 2 Duo (Penryn/Merom family) or
|
||||
Celeron M (Merom L family) |
|
||||
| **Graphics** | Intel GMA 4500MHD (or ATI Mobility Radeon HD
|
||||
3470 on some models) |
|
||||
| **Display** | 1280x800/1680x1050 TFT |
|
||||
| **Memory** | 512MB, 2GB or 4GB (Upgradable to 8GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | Proprietary |
|
||||
| **Original boot firmware** | LenovoBIOS |
|
||||
| **Intel ME/AMD PSP** | Present. Can be completly disabled. |
|
||||
| **Flash chip** | SOIC-8/SOIC-16/WSON-8 4MiB/8MiB (Upgradable
|
||||
to 16MiB) |
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|----------------|---------------------------------------|
|
||||
| **Internal flashing with original boot firmware** | N |
|
||||
| **Display** | W+ |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Dell Latitude E6400
|
||||
===================
|
||||
|
||||
**If you haven't bought an R500 yet: the [Dell Latitude
|
||||
E6400](../../news/e6400.md) is much easier to flash; no disassembly required,
|
||||
it can be flashed entirely in software from Dell BIOS to Libreboot. It is the
|
||||
same hardware generation (GM45), with same CPUs, video processor, etc.**
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
This board as basically identical to the T500, and has very similar disassembly.
|
||||
You must take it apart and flash the chip externally.
|
||||
|
||||
The chip is 4MiB NOR flash (SPI protocol) is SOIC8 form factory.
|
||||
|
||||
Refer to the following guide:\
|
||||
[Externally rewrite 25xx NOR flash via SPI protocol](../install/spi.md)
|
||||
|
||||
Unlike other GM45+ICH9M thinkpads in libreboot, the R500 doesn't have an Intel
|
||||
PHY (for Gigabit Ethernet). However, libreboot still includes an Intel flash
|
||||
descriptor, but with just the descriptor and BIOS region. The `ich9gen` program
|
||||
supports this fully.
|
||||
|
||||
Therefore, you do not have to worry about the MAC address. The onboard NIC for
|
||||
ethernet is made by Broadcom (and works in linux-libre).
|
||||
|
||||
Refer to T500 disassembly guide. The R500 disassembly procedure is almost
|
||||
identical.
|
||||
|
|
@ -70,7 +70,7 @@ Build ROM image from source
|
|||
|
||||
The build target, when building from source, is thus:
|
||||
|
||||
./mk -b coreboot t1650_12mb
|
||||
./build roms t1650_12mb
|
||||
|
||||
Installation
|
||||
============
|
||||
|
|
@ -0,0 +1,104 @@
|
|||
---
|
||||
title: ThinkPad T400
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
<img tabindex=1 alt="ThinkPad T400" class="p" src="https://av.libreboot.org/t400/boot1.jpg" /><span class="f"><img src="https://av.libreboot.org/t400/boot1.jpg" /></span>
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Lenovo |
|
||||
| **Name** | ThinkPad T400 |
|
||||
| **Released** | 2009 |
|
||||
| **Chipset** | Intel Cantiga GM45 |
|
||||
| **CPU** | Intel Core 2 Duo (Penryn family). A Quad-core
|
||||
mod exists, replacing the Core 2 Duo with a Core Quad |
|
||||
| **Graphics** | Intel GMA 4500MHD (and ATI Mobility Radeon HD
|
||||
3650 on some models) |
|
||||
| **Display** | 1280x800/1440x900 TFT |
|
||||
| **Memory** | 2 or 4GB (Upgradable to 8GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | Proprietary |
|
||||
| **Original boot firmware** | LenovoBIOS |
|
||||
| **Intel ME/AMD PSP** | Present. Can be completly disabled. |
|
||||
| **Flash chip** | SOIC-8/SOIC-16/WSON-8 4MiB/8MiB (Upgradable
|
||||
to 16MiB) |
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|----------------|---------------------------------------|
|
||||
| **Internal flashing with original boot firmware** | N |
|
||||
| **Display** | W+ |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Dell Latitude E6400
|
||||
===================
|
||||
|
||||
**If you haven't bought an T400 yet: the [Dell Latitude
|
||||
E6400](../../news/e6400.md) is much easier to flash; no disassembly required,
|
||||
it can be flashed entirely in software from Dell BIOS to Libreboot. It is the
|
||||
same hardware generation (GM45), with same CPUs, video processor, etc.**
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
It is believed that all or most laptops of the model T400 are compatible. See notes
|
||||
about [CPU
|
||||
compatibility](../install/t400_external.html#cpu_compatibility) for
|
||||
potential incompatibilities.
|
||||
|
||||
There are two possible flash chip sizes for the T400: 4MiB (32Mbit) or
|
||||
8MiB (64Mbit). This can be identified by the type of flash chip below
|
||||
the palmrest: 4MiB is SOIC-8, 8MiB is SOIC-16.
|
||||
|
||||
*The T400 laptops come with the ME (and sometimes AMT in addition)
|
||||
before flashing libreboot. libreboot disables and removes it by using a
|
||||
modified descriptor: see [../install/ich9utils.md](../install/ich9utils.md)*
|
||||
(contains notes, plus instructions)
|
||||
|
||||
Flashing instructions can be found at
|
||||
[../install/\#flashprog](../install/#flashprog)
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
||||
EC update {#ecupdate}
|
||||
=========
|
||||
|
||||
It is recommended that you update to the latest EC firmware version. The
|
||||
[EC firmware](../../faq.md#ec-embedded-controller-firmware) is separate from
|
||||
libreboot, so we don't actually provide that, but if you still have
|
||||
Lenovo BIOS then you can just run the Lenovo BIOS update utility, which
|
||||
will update both the BIOS and EC version. See:
|
||||
|
||||
- [../install/#flashprog](../install/#flashprog)
|
||||
- <http://www.thinkwiki.org/wiki/BIOS_update_without_optical_disk>
|
||||
|
||||
NOTE: this can only be done when you are using Lenovo BIOS. How to
|
||||
update the EC firmware while running libreboot is unknown. libreboot
|
||||
only replaces the BIOS firmware, not EC.
|
||||
|
||||
Updated EC firmware has several advantages e.g. bettery battery
|
||||
handling.
|
||||
|
||||
The T400 is almost identical to the X200, code-wise. See
|
||||
[x200.md](x200.md).
|
||||
|
|
@ -0,0 +1,106 @@
|
|||
---
|
||||
title: ThinkPad T500
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
<img tabindex=1 alt="ThinkPad T500" class="p" src="https://av.libreboot.org/t500/0062.jpg" /><span class="f"><img src="https://av.libreboot.org/t500/0062.jpg" /></span>
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Lenovo |
|
||||
| **Name** | ThinkPad T500 |
|
||||
| **Released** | 2009 |
|
||||
| **Chipset** | Intel Cantiga GM45 |
|
||||
| **CPU** | Intel Core 2 Duo (Penryn family). A Quad-core
|
||||
mod exists, replacing the Core 2 Duo with a Core Quad |
|
||||
| **Graphics** | Intel GMA 4500MHD (and ATI Mobility Radeon HD
|
||||
3650 on some models) |
|
||||
| **Display** | 1280x800/1680x1050/1920x1200 TFT |
|
||||
| **Memory** | 2 or 4GB (Upgradable to 8GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | Proprietary |
|
||||
| **Original boot firmware** | LenovoBIOS |
|
||||
| **Intel ME/AMD PSP** | Present. Can be completly disabled. |
|
||||
| **Flash chip** | SOIC-8/SOIC-16/WSON-8 4MiB/8MiB (Upgradable
|
||||
to 16MiB) |
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|----------------|---------------------------------------|
|
||||
| **Internal flashing with original boot firmware** | N |
|
||||
| **Display** | W+ |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | P+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
Dell Latitude E6400
|
||||
===================
|
||||
|
||||
**If you haven't bought an T500 yet: the [Dell Latitude
|
||||
E6400](../../news/e6400.md) is much easier to flash; no disassembly required,
|
||||
it can be flashed entirely in software from Dell BIOS to Libreboot. It is the
|
||||
same hardware generation (GM45), with same CPUs, video processor, etc.**
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
It is believed that all or most T500 laptops are compatible. See notes
|
||||
about [CPU
|
||||
compatibility](../install/t500_external.html#cpu_compatibility) for
|
||||
potential incompatibilities.
|
||||
|
||||
W500 is also compatible, and mostly the same design as T500.
|
||||
|
||||
There are two possible flash chip sizes for the T500: 4MiB (32Mbit) or
|
||||
8MiB (64Mbit). This can be identified by the type of flash chip below
|
||||
the palmrest: 4MiB is SOIC-8, 8MiB is SOIC-16.
|
||||
|
||||
*The T500 laptops come with the ME (and sometimes AMT in addition)
|
||||
before flashing libreboot. libreboot disables and removes it by using a
|
||||
modified descriptor: see [../install/ich9utils.md](../install/ich9utils.md)*
|
||||
(contains notes, plus instructions)
|
||||
|
||||
Flashing instructions can be found at
|
||||
[../install/\#flashprog](../install/#flashprog)
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
||||
EC update {#ecupdate}
|
||||
=========
|
||||
|
||||
It is recommended that you update to the latest EC firmware version. The
|
||||
[EC firmware](../../faq.md#ec-embedded-controller-firmware) is separate from
|
||||
libreboot, so we don't actually provide that, but if you still have
|
||||
Lenovo BIOS then you can just run the Lenovo BIOS update utility, which
|
||||
will update both the BIOS and EC version. See:
|
||||
|
||||
- [../install/#flashprog](../install/#flashprog)
|
||||
- <http://www.thinkwiki.org/wiki/BIOS_update_without_optical_disk>
|
||||
|
||||
NOTE: this can only be done when you are using Lenovo BIOS. How to
|
||||
update the EC firmware while running libreboot is unknown. libreboot
|
||||
only replaces the BIOS firmware, not EC.
|
||||
|
||||
Updated EC firmware has several advantages e.g. bettery battery
|
||||
handling.
|
||||
|
||||
The T500 is almost identical to the X200, code-wise. See
|
||||
[x200.md](x200.md).
|
||||
File diff suppressed because it is too large
Load Diff
|
|
@ -0,0 +1,196 @@
|
|||
USB
|
||||
|
||||
|
||||
coreboot-4.0-7318-g129462d Mon Dec 8 22:08:18 GMT 2014 starting...
|
||||
running main(bist = 0)
|
||||
WARNING: Ignoring S4-assertion-width violation.
|
||||
Stepping B3
|
||||
2 CPU cores
|
||||
AMT enabled
|
||||
capable of DDR2 of 800 MHz or lower
|
||||
VT-d enabled
|
||||
GMCH: GS45, using low power mode by default
|
||||
TXT enabled
|
||||
Render frequency: 533 MHz
|
||||
IGD enabled
|
||||
PCIe-to-GMCH enabled
|
||||
GMCH supports DDR3 with 1067 MT or less
|
||||
GMCH supports FSB with up to 1067 MHz
|
||||
SMBus controller enabled.
|
||||
0:50:b
|
||||
2:51:b
|
||||
DDR mask 5, DDR 3
|
||||
Bank 0 populated:
|
||||
Raw card type: F
|
||||
Row addr bits: 14
|
||||
Col addr bits: 10
|
||||
byte width: 1
|
||||
page size: 1024
|
||||
banks: 8
|
||||
ranks: 2
|
||||
tAAmin: 105
|
||||
tCKmin: 15
|
||||
Max clock: 533 MHz
|
||||
CAS: 0x01c0
|
||||
Bank 1 populated:
|
||||
Raw card type: B
|
||||
Row addr bits: 15
|
||||
Col addr bits: 10
|
||||
byte width: 1
|
||||
page size: 1024
|
||||
banks: 8
|
||||
ranks: 1
|
||||
tAAmin: 105
|
||||
tCKmin: 12
|
||||
Max clock: 666 MHz
|
||||
CAS: 0x07e0
|
||||
Trying CAS 7, tCK 15.
|
||||
Found compatible clock / CAS pair: 533 / 7.
|
||||
Timing values:
|
||||
tCLK: 15
|
||||
tRAS: 20
|
||||
tRP: 7
|
||||
tRCD: 7
|
||||
tRFC: 104
|
||||
tWR: 8
|
||||
tRD: 11
|
||||
tRRD: 4
|
||||
tFAW: 20
|
||||
tWL: 6
|
||||
Changing memory frequency: old 3, new 6.
|
||||
Setting IGD memory frequencies for VCO #1.
|
||||
SFF platform unsupported in RCOMP initialization.
|
||||
USB
|
||||
|
||||
|
||||
coreboot-4.0-7318-g129462d Mon Dec 8 22:08:18 GMT 2014 starting...
|
||||
running main(bist = 0)
|
||||
Interrupted RAM init, reset required.
|
||||
USB
|
||||
|
||||
|
||||
coreboot-4.0-7318-g129462d Mon Dec 8 22:08:18 GMT 2014 starting...
|
||||
running main(bist = 0)
|
||||
Stepping B3
|
||||
2 CPU cores
|
||||
AMT enabled
|
||||
capable of DDR2 of 800 MHz or lower
|
||||
VT-d enabled
|
||||
GMCH: GS45, using low power mode by default
|
||||
TXT enabled
|
||||
Render frequency: 533 MHz
|
||||
IGD enabled
|
||||
PCIe-to-GMCH enabled
|
||||
GMCH supports DDR3 with 1067 MT or less
|
||||
GMCH supports FSB with up to 1067 MHz
|
||||
SMBus controller enabled.
|
||||
0:50:b
|
||||
2:51:b
|
||||
DDR mask 5, DDR 3
|
||||
Bank 0 populated:
|
||||
Raw card type: F
|
||||
Row addr bits: 14
|
||||
Col addr bits: 10
|
||||
byte width: 1
|
||||
page size: 1024
|
||||
banks: 8
|
||||
ranks: 2
|
||||
tAAmin: 105
|
||||
tCKmin: 15
|
||||
Max clock: 533 MHz
|
||||
CAS: 0x01c0
|
||||
Bank 1 populated:
|
||||
Raw card type: B
|
||||
Row addr bits: 15
|
||||
Col addr bits: 10
|
||||
byte width: 1
|
||||
page size: 1024
|
||||
banks: 8
|
||||
ranks: 1
|
||||
tAAmin: 105
|
||||
tCKmin: 12
|
||||
Max clock: 666 MHz
|
||||
CAS: 0x07e0
|
||||
Trying CAS 7, tCK 15.
|
||||
Found compatible clock / CAS pair: 533 / 7.
|
||||
Timing values:
|
||||
tCLK: 15
|
||||
tRAS: 20
|
||||
tRP: 7
|
||||
tRCD: 7
|
||||
tRFC: 104
|
||||
tWR: 8
|
||||
tRD: 11
|
||||
tRRD: 4
|
||||
tFAW: 20
|
||||
tWL: 6
|
||||
Changing memory frequency: old 3, new 6.
|
||||
Setting IGD memory frequencies for VCO #1.
|
||||
SFF platform unsupported in RCOMP initialization.
|
||||
USB
|
||||
|
||||
|
||||
coreboot-4.0-7318-g129462d Mon Dec 8 22:08:18 GMT 2014 starting...
|
||||
running main(bist = 0)
|
||||
Interrupted RAM init, reset required.
|
||||
USB
|
||||
|
||||
|
||||
coreboot-4.0-7318-g129462d Mon Dec 8 22:08:18 GMT 2014 starting...
|
||||
running main(bist = 0)
|
||||
Stepping B3
|
||||
2 CPU cores
|
||||
AMT enabled
|
||||
capable of DDR2 of 800 MHz or lower
|
||||
VT-d enabled
|
||||
GMCH: GS45, using low power mode by default
|
||||
TXT enabled
|
||||
Render frequency: 533 MHz
|
||||
IGD enabled
|
||||
PCIe-to-GMCH enabled
|
||||
GMCH supports DDR3 with 1067 MT or less
|
||||
GMCH supports FSB with up to 1067 MHz
|
||||
SMBus controller enabled.
|
||||
0:50:b
|
||||
2:51:b
|
||||
DDR mask 5, DDR 3
|
||||
Bank 0 populated:
|
||||
Raw card type: F
|
||||
Row addr bits: 14
|
||||
Col addr bits: 10
|
||||
byte width: 1
|
||||
page size: 1024
|
||||
banks: 8
|
||||
ranks: 2
|
||||
tAAmin: 105
|
||||
tCKmin: 15
|
||||
Max clock: 533 MHz
|
||||
CAS: 0x01c0
|
||||
Bank 1 populated:
|
||||
Raw card type: B
|
||||
Row addr bits: 15
|
||||
Col addr bits: 10
|
||||
byte width: 1
|
||||
page size: 1024
|
||||
banks: 8
|
||||
ranks: 1
|
||||
tAAmin: 105
|
||||
tCKmin: 12
|
||||
Max clock: 666 MHz
|
||||
CAS: 0x07e0
|
||||
Trying CAS 7, tCK 15.
|
||||
Found compatible clock / CAS pair: 533 / 7.
|
||||
Timing values:
|
||||
tCLK: 15
|
||||
tRAS: 20
|
||||
tRP: 7
|
||||
tRCD: 7
|
||||
tRFC: 104
|
||||
tWR: 8
|
||||
tRD: 11
|
||||
tRRD: 4
|
||||
tFAW: 20
|
||||
tWL: 6
|
||||
Changing memory frequency: old 3, new 6.
|
||||
Setting IGD memory frequencies for VCO #1.
|
||||
SFF platform unsupported in RCOMP initialization.
|
||||
File diff suppressed because it is too large
Load Diff
|
|
@ -0,0 +1,77 @@
|
|||
USB
|
||||
|
||||
|
||||
coreboot-4.0-7551-ge420139-dirty Wed Dec 10 16:34:05 GMT 2014 starting...
|
||||
running main(bist = 0)
|
||||
WARNING: Ignoring S4-assertion-width violation.
|
||||
Stepping B3
|
||||
2 CPU cores
|
||||
AMT enabled
|
||||
capable of DDR2 of 800 MHz or lower
|
||||
VT-d enabled
|
||||
GMCH: GS45, using high performance mode by default
|
||||
TXT enabled
|
||||
Render frequency: 533 MHz
|
||||
IGD enabled
|
||||
PCIe-to-GMCH enabled
|
||||
GMCH supports DDR3 with 1067 MT or less
|
||||
GMCH supports FSB with up to 1067 MHz
|
||||
SMBus controller enabled.
|
||||
0:50:b
|
||||
2:51:b
|
||||
DDR mask 5, DDR 3
|
||||
Bank 0 populated:
|
||||
Raw card type: F
|
||||
Row addr bits: 14
|
||||
Col addr bits: 10
|
||||
byte width: 1
|
||||
page size: 1024
|
||||
banks: 8
|
||||
ranks: 2
|
||||
tAAmin: 105
|
||||
tCKmin: 15
|
||||
Max clock: 533 MHz
|
||||
CAS: 0x01c0
|
||||
Bank 1 populated:
|
||||
Raw card type: B
|
||||
Row addr bits: 15
|
||||
Col addr bits: 10
|
||||
byte width: 1
|
||||
page size: 1024
|
||||
banks: 8
|
||||
ranks: 1
|
||||
tAAmin: 105
|
||||
tCKmin: 12
|
||||
Max clock: 666 MHz
|
||||
CAS: 0x07e0
|
||||
Trying CAS 7, tCK 15.
|
||||
Found compatible clock / CAS pair: 533 / 7.
|
||||
Timing values:
|
||||
tCLK: 15
|
||||
tRAS: 20
|
||||
tRP: 7
|
||||
tRCD: 7
|
||||
tRFC: 104
|
||||
tWR: 8
|
||||
tRD: 11
|
||||
tRRD: 4
|
||||
tFAW: 20
|
||||
tWL: 6
|
||||
Changing memory frequency: old 3, new 6.
|
||||
Setting IGD memory frequencies for VCO #1.
|
||||
Memory configured in dual-channel assymetric mode.
|
||||
Memory map:
|
||||
TOM = 384MB
|
||||
TOLUD = 384MB
|
||||
TOUUD = 384MB
|
||||
REMAP: base = 65535MB
|
||||
limit = 0MB
|
||||
usedMEsize: 0MB
|
||||
Performing Jedec initialization at address 0x00000000.
|
||||
Performing Jedec initialization at address 0x08000000.
|
||||
Performing Jedec initialization at address 0x10000000.
|
||||
Final timings for group 0 on channel 0: 6.1.0.3.2
|
||||
Final timings for group 1 on channel 0: 6.0.2.6.3
|
||||
Final timings for group 2 on channel 0: 6.1.2.0.1
|
||||
Final timings for group 3 on channel 0: 6.1.0.7.3
|
||||
Timing under-/overflow during receive-enable calibration.
|
||||
|
|
@ -0,0 +1,158 @@
|
|||
USB
|
||||
|
||||
|
||||
coreboot-4.0-7551-ge420139-dirty Wed Dec 10 16:34:05 GMT 2014 starting...
|
||||
running main(bist = 0)
|
||||
WARNING: Ignoring S4-assertion-width violation.
|
||||
Stepping B3
|
||||
2 CPU cores
|
||||
AMT enabled
|
||||
capable of DDR2 of 800 MHz or lower
|
||||
VT-d enabled
|
||||
GMCH: GS45, using high performance mode by default
|
||||
TXT enabled
|
||||
Render frequency: 533 MHz
|
||||
IGD enabled
|
||||
PCIe-to-GMCH enabled
|
||||
GMCH supports DDR3 with 1067 MT or less
|
||||
GMCH supports FSB with up to 1067 MHz
|
||||
SMBus controller enabled.
|
||||
0:50:ff
|
||||
2:51:b
|
||||
DDR mask 4, DDR 3
|
||||
Bank 1 populated:
|
||||
Raw card type: B
|
||||
Row addr bits: 15
|
||||
Col addr bits: 10
|
||||
byte width: 1
|
||||
page size: 1024
|
||||
banks: 8
|
||||
ranks: 1
|
||||
tAAmin: 105
|
||||
tCKmin: 12
|
||||
Max clock: 666 MHz
|
||||
CAS: 0x07e0
|
||||
DIMMs support 666 MHz, but chipset only runs at up to 533. Limiting...
|
||||
Trying CAS 7, tCK 15.
|
||||
Found compatible clock / CAS pair: 533 / 7.
|
||||
Timing values:
|
||||
tCLK: 15
|
||||
tRAS: 20
|
||||
tRP: 7
|
||||
tRCD: 7
|
||||
tRFC: 104
|
||||
tWR: 8
|
||||
tRD: 11
|
||||
tRRD: 4
|
||||
tFAW: 20
|
||||
tWL: 6
|
||||
Changing memory frequency: old 3, new 6.
|
||||
Setting IGD memory frequencies for VCO #1.
|
||||
Memory configured in single-channel mode.
|
||||
Memory map:
|
||||
TOM = 128MB
|
||||
TOLUD = 128MB
|
||||
TOUUD = 128MB
|
||||
REMAP: base = 65535MB
|
||||
limit = 0MB
|
||||
usedMEsize: 0MB
|
||||
Performing Jedec initialization at address 0x00000000.
|
||||
Final timings for group 0 on channel 1: 6.0.2.6.4
|
||||
Final timings for group 1 on channel 1: 6.0.2.6.4
|
||||
Final timings for group 2 on channel 1: 6.0.2.8.3
|
||||
Final timings for group 3 on channel 1: 6.0.2.8.6
|
||||
Lower bound for byte lane 0 on channel 1: 0.0
|
||||
Upper bound for byte lane 0 on channel 1: 10.4
|
||||
Final timings for byte lane 0 on channel 1: 5.2
|
||||
Lower bound for byte lane 1 on channel 1: 0.0
|
||||
Upper bound for byte lane 1 on channel 1: 11.2
|
||||
Final timings for byte lane 1 on channel 1: 5.5
|
||||
Lower bound for byte lane 2 on channel 1: 0.0
|
||||
Upper bound for byte lane 2 on channel 1: 10.5
|
||||
Final timings for byte lane 2 on channel 1: 5.2
|
||||
Lower bound for byte lane 3 on channel 1: 0.0
|
||||
Upper bound for byte lane 3 on channel 1: 9.7
|
||||
Final timings for byte lane 3 on channel 1: 4.7
|
||||
Timing overflow during read training.
|
||||
Read training failure: lower bound.
|
||||
USB
|
||||
|
||||
|
||||
coreboot-4.0-7551-ge420139-dirty Wed Dec 10 16:34:05 GMT 2014 starting...
|
||||
running main(bist = 0)
|
||||
Interrupted RAM init, reset required.
|
||||
USB
|
||||
|
||||
|
||||
coreboot-4.0-7551-ge420139-dirty Wed Dec 10 16:34:05 GMT 2014 starting...
|
||||
running main(bist = 0)
|
||||
Stepping B3
|
||||
2 CPU cores
|
||||
AMT enabled
|
||||
capable of DDR2 of 800 MHz or lower
|
||||
VT-d enabled
|
||||
GMCH: GS45, using high performance mode by default
|
||||
TXT enabled
|
||||
Render frequency: 533 MHz
|
||||
IGD enabled
|
||||
PCIe-to-GMCH enabled
|
||||
GMCH supports DDR3 with 1067 MT or less
|
||||
GMCH supports FSB with up to 1067 MHz
|
||||
SMBus controller enabled.
|
||||
0:50:ff
|
||||
2:51:b
|
||||
DDR mask 4, DDR 3
|
||||
Bank 1 populated:
|
||||
Raw card type: B
|
||||
Row addr bits: 15
|
||||
Col addr bits: 10
|
||||
byte width: 1
|
||||
page size: 1024
|
||||
banks: 8
|
||||
ranks: 1
|
||||
tAAmin: 105
|
||||
tCKmin: 12
|
||||
Max clock: 666 MHz
|
||||
CAS: 0x07e0
|
||||
DIMMs support 666 MHz, but chipset only runs at up to 533. Limiting...
|
||||
Trying CAS 7, tCK 15.
|
||||
Found compatible clock / CAS pair: 533 / 7.
|
||||
Timing values:
|
||||
tCLK: 15
|
||||
tRAS: 20
|
||||
tRP: 7
|
||||
tRCD: 7
|
||||
tRFC: 104
|
||||
tWR: 8
|
||||
tRD: 11
|
||||
tRRD: 4
|
||||
tFAW: 20
|
||||
tWL: 6
|
||||
Setting IGD memory frequencies for VCO #1.
|
||||
Memory configured in single-channel mode.
|
||||
Memory map:
|
||||
TOM = 128MB
|
||||
TOLUD = 128MB
|
||||
TOUUD = 128MB
|
||||
REMAP: base = 65535MB
|
||||
limit = 0MB
|
||||
usedMEsize: 0MB
|
||||
Performing Jedec initialization at address 0x00000000.
|
||||
Final timings for group 0 on channel 1: 6.0.2.7.6
|
||||
Final timings for group 1 on channel 1: 6.0.2.6.6
|
||||
Final timings for group 2 on channel 1: 6.0.2.8.7
|
||||
Final timings for group 3 on channel 1: 6.1.0.2.5
|
||||
Lower bound for byte lane 0 on channel 1: 0.0
|
||||
Upper bound for byte lane 0 on channel 1: 10.3
|
||||
Final timings for byte lane 0 on channel 1: 5.1
|
||||
Lower bound for byte lane 1 on channel 1: 0.0
|
||||
Upper bound for byte lane 1 on channel 1: 11.3
|
||||
Final timings for byte lane 1 on channel 1: 5.5
|
||||
Lower bound for byte lane 2 on channel 1: 0.0
|
||||
Upper bound for byte lane 2 on channel 1: 10.5
|
||||
Final timings for byte lane 2 on channel 1: 5.2
|
||||
Lower bound for byte lane 3 on channel 1: 0.0
|
||||
Upper bound for byte lane 3 on channel 1: 9.6
|
||||
Final timings for byte lane 3 on channel 1: 4.7
|
||||
Timing overflow during read training.
|
||||
Read training failure: lower bound.
|
||||
|
|
@ -1,5 +1,5 @@
|
|||
---
|
||||
title: First-time ThinkPad X200 flashing
|
||||
title: ThinkPad X200
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
|
|
@ -48,12 +48,11 @@ P*: Partially works with blobs
|
|||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
|
||||
Dell Latitude E6400
|
||||
===================
|
||||
|
||||
**If you haven't bought an X200 yet: the [Dell Latitude
|
||||
E6400](../install/latitude.md) is much easier to flash; no disassembly required,
|
||||
E6400](../../news/e6400.md) is much easier to flash; no disassembly required,
|
||||
it can be flashed entirely in software from Dell BIOS to Libreboot. It is the
|
||||
same hardware generation (GM45), with same CPUs, video processor, etc.**
|
||||
|
||||
|
|
@ -183,159 +182,14 @@ the following: *"This product contains Lithium Ion Battery, Lithium Battery and
|
|||
a lamp which contains mercury; dispose according to local, state or federal
|
||||
laws"* (one with an LED backlit panel will say something different).
|
||||
|
||||
Installation notes
|
||||
==================
|
||||
Hardware register dumps {#regdumps}
|
||||
-----------------------
|
||||
|
||||
[External flashing](spi.md) required, if running Lenovo BIOS.
|
||||
The coreboot wiki
|
||||
[shows](http://www.coreboot.org/Motherboard_Porting_Guide) how to
|
||||
collect various logs useful in porting to new boards. Following are
|
||||
outputs from the X200:
|
||||
|
||||
This guide is for those who want libreboot on their ThinkPad X200 while
|
||||
they still have the original Lenovo BIOS present. This guide can also be
|
||||
followed (adapted) if you brick your X200, to know how to recover.
|
||||
- BIOS 3.15, EC 1.06
|
||||
- [hwdumps/x200/](hwdumps/x200/)
|
||||
|
||||
If you have the original Lenovo firmware running, you will need to take the
|
||||
keyboard and palmrest off so that you can access the flash chip, which is just
|
||||
underneath the palm rest. You will then connect an external SPI programmer, to
|
||||
re-flash the chip externally while it is powered off with the battery removed.
|
||||
|
||||
NOTE: This guide only applies to the regular X200. For X200S and X200 Tablet
|
||||
flashing, please read other guides available on libreboot.org.
|
||||
|
||||
Flash chip size
|
||||
===============
|
||||
|
||||
Run this command on x200 to find out flash chip model and its size:
|
||||
|
||||
flashprog -p internal
|
||||
|
||||
MAC address
|
||||
===========
|
||||
|
||||
Refer to [mac\_address.md](mac_address.md).
|
||||
|
||||
The procedure
|
||||
-------------
|
||||
|
||||
This section is for the X200. This does not apply to the X200S or X200
|
||||
Tablet (for those systems, you have to remove the motherboard
|
||||
completely, since the flash chip is on the other side of the board).
|
||||
|
||||
Remove these screws:\
|
||||

|
||||
|
||||
Gently push the keyboard towards the screen, then lift it off, and optionally
|
||||
disconnect it from the board:\
|
||||

|
||||

|
||||
|
||||
Disconnect the cable of the fingerpring reader, and then pull up the palm rest,
|
||||
lifting up the left and right side of it:\
|
||||

|
||||

|
||||
|
||||
This shows the location of the flash chip, for both SOIC-8 and SOIC-16:\
|
||||

|
||||

|
||||
|
||||
Lift back the tape that covers a part of the flash chip, and then
|
||||
connect the clip:\
|
||||
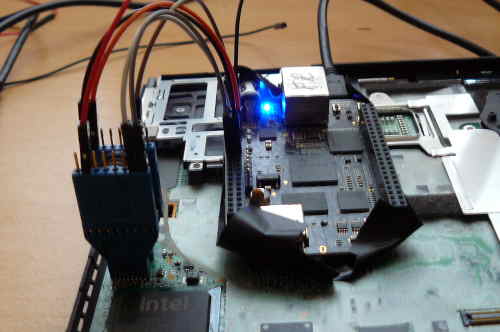
|
||||
|
||||
Now, you should be ready to install libreboot.
|
||||
|
||||
Refer to the [SPI programming instructions](spi.md).
|
||||
|
||||
When you're done, put the system back together. If it doesn't boot, try other
|
||||
RAM modules because raminit is very unreliable on this platform (in coreboot).
|
||||
|
||||
Memory
|
||||
======
|
||||
|
||||
In DDR3 machines with Cantiga (GM45/GS45/PM45), northbridge requires sticks
|
||||
that will work as PC3-8500 (faster PC3/PC3L sticks can work as PC3-8500).
|
||||
Non-matching pairs may not work. Single module (meaning, one of the slots
|
||||
will be empty) will currently only work in slot 0.
|
||||
|
||||
NOTE: according to users reports, non matching pairs (e.g. 1+2 GiB) might
|
||||
work in some cases.
|
||||
|
||||
Make sure that the RAM you buy is the 2Rx8 configuration when buying 4GiB sticks
|
||||
(In other words: maximum of 2GiB per rank, 2 ranks per card).
|
||||
|
||||
In this photo, 8GiB of RAM (2x4GiB) is installed:
|
||||
|
||||

|
||||
|
||||
Boot it!
|
||||
--------
|
||||
|
||||
You should see something like this:
|
||||
|
||||
|
||||
|
||||
Now [install Linux](../linux/).
|
||||
|
||||
X200S and X200 Tablet users: GPIO33 trick will not work.
|
||||
--------------------------------------------------------
|
||||
|
||||
sgsit found out about a pin called GPIO33, which can be grounded to
|
||||
disable the flashing protections by the descriptor and stop the ME from
|
||||
starting (which itself interferes with flashing attempts). The theory
|
||||
was proven correct; however, it is still useless in practise.
|
||||
|
||||
Look just above the 7 in TP37 (that's GPIO33):
|
||||
|
||||

|
||||
|
||||
By default we would see this in lenovobios, when trying flashprog -p
|
||||
internal -w rom.rom:
|
||||
|
||||
```
|
||||
FREG0: Warning: Flash Descriptor region (0x00000000-0x00000fff) is read-only.
|
||||
FREG2: Warning: Management Engine region (0x00001000-0x005f5fff) is locked.
|
||||
```
|
||||
|
||||
With GPIO33 grounded during boot, this disabled the flash protections as
|
||||
set by descriptor, and stopped the ME from starting. The output changed
|
||||
to:
|
||||
|
||||
```
|
||||
The Flash Descriptor Override Strap-Pin is set. Restrictions implied by
|
||||
the Master Section of the flash descriptor are NOT in effect. Please note
|
||||
that Protected Range (PR) restrictions still apply.
|
||||
```
|
||||
|
||||
The part in bold is what got us. This was still observed:
|
||||
|
||||
```
|
||||
PR0: Warning: 0x007e0000-0x01ffffff is read-only.
|
||||
PR4: Warning: 0x005f8000-0x005fffff is locked.
|
||||
```
|
||||
|
||||
It is actually possible to disable these protections. Lenovobios does,
|
||||
when updating the BIOS (proprietary one). One possible way to go about
|
||||
this would be to debug the BIOS update utility from Lenovo, to find out
|
||||
how it's disabling these protections. Some more research is available
|
||||
here:
|
||||
<http://www.coreboot.org/Board:lenovo/x200/internal_flashing_research>
|
||||
|
||||
Of course, it's likely that the Lenovo BIOS is checking for some bit in memory
|
||||
that tells it not to disable flashing, and then it won't set PRx registers. The
|
||||
way the Lenovo BIOS updater works is, it is executed in Windows first and then
|
||||
a reboot happens, triggering the re-flashing to happen during early boot. It is
|
||||
probably setting something in memory and loading the ROM, plus a payload program
|
||||
that does the flashing; Lenovo BIOS then probably sees that and runs that, instead
|
||||
of setting PRx and going for normal boot. It is theoretically possible that we
|
||||
could discover how this works, by debugging the Lenovo BIOS update utility (in
|
||||
Windows), and then replicate what it is doing, with some tool for Linux,
|
||||
then load a flashprog binary into memory and the ROM to flash (for the BIOS
|
||||
region). You would do this with GPIO33 grounded, and the payload program would
|
||||
actually flash the entire chip, with just a normal libreboot image.
|
||||
|
||||
It's possible. The above is likely the only way that the Lenovo BIOS updater
|
||||
program works. So if we discover precisely how to do that, then you could
|
||||
just connect some pogo pins to ground GPIO33, then boot up, run some software
|
||||
(which would have to be written) that does the above.
|
||||
|
||||
On a related note, libreboot has a utility that could help with
|
||||
investigating this:
|
||||
[ich9utils.md#demefactory](ich9utils.md#demefactory)
|
||||
|
|
@ -1,5 +1,5 @@
|
|||
---
|
||||
title: Прошивка ThinkPad X200 вперше
|
||||
title: ThinkPad X200
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
|
|
@ -175,153 +175,14 @@ CCFL містять меркурій. На X200 з CCFL підсвіткою (я
|
|||
яка містить ртуть; утилізуйте відповідно до місцевих, державних або федеральних
|
||||
законів"* (на тому, що має світлодіодне підсвічування, буде написано щось інше).
|
||||
|
||||
Installation notes
|
||||
==================
|
||||
Дампи апаратного регістру {#regdumps}
|
||||
-----------------------
|
||||
|
||||
[External flashing](spi.md) required, if running Lenovo BIOS.
|
||||
Вікі coreboot
|
||||
[показує](http://www.coreboot.org/Motherboard_Porting_Guide) як
|
||||
збирати різноманітні логи, корисні для портування на нові плати. Нижче наведено
|
||||
вихідні дані X200:
|
||||
|
||||
Цей посібник призначений для тих, хто бажає libreboot на своєму ThinkPad X200,
|
||||
поки у нього все ще є оригінальний Lenovo BIOS в наявності. Цього керівництва також можна
|
||||
дотримуватися (адаптувати), якщо ви перетворили ваш X200 на цеглину, щоб знати, як його відновити.
|
||||
- BIOS 3.15, EC 1.06
|
||||
- [hwdumps/x200/](hwdumps/x200/)
|
||||
|
||||
Якщо у вас виконується оригінальна мікропрограма Lenovo, вам потрібно буде зняти
|
||||
клавіатуру та підставку для рук, щоб мати доступ до мікросхеми флеш-пам'яті, яка знаходиться прямо
|
||||
під підставкою для рук. Потім ви підключите зовнішній програматор SPI, щоб
|
||||
повторно прошити мікросхему зовні, коли вона вимкнена та акумулятор висунуто.
|
||||
|
||||
ПРИМІТКА: Цей посібник стосується лише звичайного X200. Для перепрошивки X200S та X200 Tablet,
|
||||
будь-ласка прочитайте інші посібники, доступні на libreboot.org.
|
||||
|
||||
Розмір флеш-чіпа
|
||||
===============
|
||||
|
||||
Виконайте цю команду на x200, щоб дізнатися модель флеш-чіпа та його розмір:
|
||||
|
||||
flashprog -p internal
|
||||
|
||||
MAC адреса
|
||||
===========
|
||||
|
||||
Зверніться до [mac\_address.md](mac_address.md).
|
||||
|
||||
Процедура
|
||||
-------------
|
||||
|
||||
Цей розділ стосується X200. Цей не стосується X200S або X200
|
||||
Tablet (для цих систем потрібно повністю видалити материнську плату,
|
||||
оскільки мікросхема флеш-пам'яті знаходиться з іншого боку плати).
|
||||
|
||||
Викрутіть ці гвинти:\
|
||||

|
||||
|
||||
Обережно притисніть клавіатуру до екрана, потім підніміть її та за бажанням
|
||||
від'єднайте від плати:\
|
||||

|
||||

|
||||
|
||||
Від'єднайте кабель пристрою для зчитування відбитків пальців, а потім потягніть упор для рук,
|
||||
піднявши його ліву та праву сторону:\
|
||||

|
||||

|
||||
|
||||
Тут показано розташування мікросхеми флеш-пам'яті, для обох SOIC-8 та SOIC-16:\
|
||||

|
||||

|
||||
|
||||
Підніміть стрічку, яка закриває частину флеш-пам'яті, а потім
|
||||
приєднайте затискач:\
|
||||

|
||||
|
||||
Тепер ви повинні бути готові до встановлення libreboot.
|
||||
|
||||
Зверніться до [інструкцій програмування SPI](spi.md).
|
||||
|
||||
Закінчивши, знову зберіть систему. Якщо вона не завантажується, спробуйте інші
|
||||
модулі оперативної пам'яті, тому що raminit дуже ненадійний на цій платформі (в coreboot).
|
||||
|
||||
Пам'ять
|
||||
======
|
||||
|
||||
У машинах DDR3 з Cantiga (GM45/GS45/PM45), північний міст потребує стіків,
|
||||
які працюватимуть як PC3-8500 (швидші стіки PC3/PC3L можуть працювати як PC3-8500).
|
||||
Пари, що не збігаються, можуть не працювати. Один модуль (тобто один із слотів
|
||||
буде порожнім) наразі працюватиме лише в слоті 0.
|
||||
|
||||
ПРИМІТКА: згідно зі звітами користувачів, у деяких випадках невідповідні пари ( 1+2 ГБ) можуть
|
||||
працювати в деяких випадках.
|
||||
|
||||
Переконайтесь, що оперативна пам'ять, яку ви купуєте, має конфігурацію 2Rx8, купуючи стіки по 4 ГБ
|
||||
(Іншими словами: максимально 2 ГБ на ранг, 2 ранга на картку).
|
||||
|
||||
На цьому фото встановлено 8 ГБ оперативної пам'яті (2x4ГБ):
|
||||
|
||||

|
||||
|
||||
Завантажуйтесь!
|
||||
--------
|
||||
|
||||
Ви маєте побачити щось подібне цьому:
|
||||
|
||||

|
||||
|
||||
Тепер [встановлюйте Linux](../linux/).
|
||||
|
||||
Користувачі X200S та X200 Tablet: трюк GPIO33 не спрацює.
|
||||
--------------------------------------------------------
|
||||
|
||||
sgsit дізнався про контакт під назвою GPIO33, який можна заземлити,
|
||||
щоб вимкнути захист прошивки за допомогою дескриптора та зупинити ME від
|
||||
запуску (який сам по собі перешкоджає спробам прошивки). Теорія була
|
||||
доведена правильною; однак на практиці це все одно марно.
|
||||
|
||||
Подивіться трохи вище 7 у TP37 (це GPIO33):
|
||||
|
||||

|
||||
|
||||
Це замовчуванням ми побачимо це в lenovobios, під час спроби flashprog -p
|
||||
internal -w rom.rom:
|
||||
|
||||
FREG0: Warning: Flash Descriptor region (0x00000000-0x00000fff) is read-only.
|
||||
FREG2: Warning: Management Engine region (0x00001000-0x005f5fff) is locked.
|
||||
|
||||
Коли GPIO33 було заземлено під час завантаження, це вимкнуло захист флеш-пам'яті,
|
||||
встановлений дескриптором, і зупинило запуск ME. Результат змінився
|
||||
на:
|
||||
|
||||
The Flash Descriptor Override Strap-Pin is set. Restrictions implied by
|
||||
the Master Section of the flash descriptor are NOT in effect. Please note
|
||||
that Protected Range (PR) restrictions still apply.
|
||||
|
||||
Частина, виділена жирним шрифтом, - це те, що нас дістало. Це все ж спостерігалось:
|
||||
|
||||
PR0: Warning: 0x007e0000-0x01ffffff is read-only.
|
||||
PR4: Warning: 0x005f8000-0x005fffff is locked.
|
||||
|
||||
Насправді ці засоби захисту можна відключити. Lenovobios робить це,
|
||||
під час оновлення BIOS (пропрієтарного). Одним із можливих способів вирішити цю проблему
|
||||
було б відлагодити утиліту оновлення BIOS від Lenovo, для віднаходження,
|
||||
як вона вимикає ці засоби захисту. Додаткові дослідження доступні
|
||||
тут:
|
||||
<http://www.coreboot.org/Board:lenovo/x200/internal_flashing_research>
|
||||
|
||||
Звичайно, ймовірно, що Lenovo BIOS перевіряє якийсь біт в пам'яті,
|
||||
який говорить йому не вимикати перепрошивку, а потім він не встановлює регістри PRx. Принцип
|
||||
роботи програми оновлення BIOS Lenovo полягає в тому, що вона спочатку виконується в Windows,
|
||||
а потім відбувається перезавантаження, ініціюючи перепрошивку під час раннього завантаження. Ймовірно,
|
||||
це встановлює щось у пам'яті та завантажує ROM, плюс програму корисного навантаження,
|
||||
яка виконує перепрошивання; тоді Lenovo BIOS, ймовірно, бачить це та запускає це замість
|
||||
встановлення PRx і переходу до нормального завантаження. Теоретично можливо, що ми
|
||||
зможемо дізнатися, як це працює, налагодивши утиліту оновлення BIOS Lenovo (у
|
||||
Windows), а потім відтворивши її дії за допомогою якогось інструменту для Linux,
|
||||
а потім завантаживши двійковий файл flashprog в пам'ять та ROM для прошивки (для BIOS
|
||||
регіона). Ви б зробили це з заземленням GPIO33, і програма корисного навантаження
|
||||
фактично прошиє весь чіп, лише звичайним образом libreboot.
|
||||
|
||||
Це можливо. Ймовірно, це єдиний спосіб роботи програми оновлення BIOS Lenovo.
|
||||
Отже, якщо ми дізнаємося, як саме це зробити, тоді ви можете просто підключити кілька
|
||||
контактів pogo для заземлення GPIO33, потім завантажитися, запустити програмне забезпечення
|
||||
(яке потрібно було б написати), яке виконує вищезазначене.
|
||||
|
||||
У зв'язку з цим у libreboot є утиліта, яка може допомогти
|
||||
розслідувати це:
|
||||
[ich9utils.md#demefactory](ich9utils.md#demefactory)
|
||||
|
|
@ -24,6 +24,7 @@ operates Minifree Ltd; sales provide funding for the Libreboot project.
|
|||
Installing libreboot
|
||||
====================
|
||||
|
||||
- [What systems can I use libreboot on?](hardware/)
|
||||
- [How to install libreboot](install/)
|
||||
|
||||
Documentation related to operating systems
|
||||
|
|
|
|||
|
|
@ -24,6 +24,7 @@ operates Minifree Ltd; sales provide funding for the Libreboot project.
|
|||
Встановлення libreboot
|
||||
====================
|
||||
|
||||
- [На яких системах я можу встановлювати libreboot?](hardware/)
|
||||
- [Як встановити libreboot](install/)
|
||||
|
||||
Документація, яка має відношення до операційних систем
|
||||
|
|
|
|||
|
|
@ -22,6 +22,7 @@ operates Minifree Ltd; sales provide funding for the Libreboot project.
|
|||
安装 libreboot
|
||||
====================
|
||||
|
||||
- [哪些机器上可以使用 libreboot?](hardware/)
|
||||
- [如何安装 libreboot](install/)
|
||||
|
||||
操作系统相关文档
|
||||
|
|
|
|||
|
|
@ -0,0 +1,23 @@
|
|||
---
|
||||
title: D510MO flashing tutorial
|
||||
...
|
||||
|
||||
This guide is for those who want libreboot on their Intel D510MO
|
||||
motherboard while they still have the original BIOS present.
|
||||
|
||||
NOTE: D410PT is another designation and it's the same board. Flash the same ROM.
|
||||
|
||||
Flash chip size {#flashchips}
|
||||
===============
|
||||
|
||||
Use this to find out:
|
||||
|
||||
flashprog -p internal
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
||||
Flashing instructions {#clip}
|
||||
=====================
|
||||
|
||||
Refer to [spi.md](spi.md) for how to re-flash externally.
|
||||
|
|
@ -1,99 +1,14 @@
|
|||
---
|
||||
title: Intel D945GCLF desktop board
|
||||
x-toc-enable: true
|
||||
title: Intel D945GCLF flashing tutorial
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
<img tabindex=1 alt="D945GCLF" class="p" src="https://av.libreboot.org/d945gclf/d945gclf.jpg" /><span class="f"><img src="https://av.libreboot.org/d945gclf/d945gclf.jpg" /></span>
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Intel |
|
||||
| **Name** | D945GCLF/D945GCLF2D |
|
||||
| **Released** | 2008 |
|
||||
| **Chipset** | Intel Calistoga 945GC |
|
||||
| **CPU** | Intel Atom |
|
||||
| **Graphics** | ? |
|
||||
| **Display** | None. |
|
||||
| **Memory** | Up to 2GB |
|
||||
| **Architecture** | x86_64 |
|
||||
| **Original boot firmware** | Intel BIOS |
|
||||
| **Intel ME/AMD PSP** | Not present. |
|
||||
| **Flash chip** | SOIC-8 512KiB |
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | | Notes |
|
||||
|----------------|---------------------------------------|-------|
|
||||
| **Internal flashing with original boot firmware** | N | |
|
||||
| **Display** | - | |
|
||||
| **Audio** | W+ | |
|
||||
| **RAM Init** | W+ | |
|
||||
| **External output** | W+ | |
|
||||
| **Display brightness** | - | |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|--------------|
|
||||
| **GRUB** | Doesn't work |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Doesn't work |
|
||||
</div>
|
||||
If you just want flashing instructions, go to
|
||||
[../install/d945gclf.md](../install/d945gclf.md)
|
||||
This guide is for those who want libreboot on their Intel D945GCLF
|
||||
motherboard while they still have the original BIOS present.
|
||||
|
||||
D945GCLF2D also reported working by a user.
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
This board is a mini-itx desktop board for 2008. It uses an atom 230,
|
||||
which is a singe core CPU but it is hyperthreaded so it appears to have
|
||||
2 thread to the OS. The flash chip is very small, 512KiB, so grub2 does
|
||||
not fit, which is why libreboot has to use seabios on this target. Full
|
||||
disk encryption like on other supported targets will not be possible, so
|
||||
plan accordingly.
|
||||
|
||||
This board has a 945gc chipset which is the desktop equivalent of 945gm
|
||||
which can be found in the Lenovo x60/t60 or macbook2,1. This chipset
|
||||
features an ICH7 southbridge. It has 1 DIMM slot that can accommodate up
|
||||
to 2G of DDR2 RAM.
|
||||
|
||||
Connectivity-wise it has 1 PCI slot, a 10/100 ethernet port, 4 usb slot
|
||||
and 4 usb ports, with one internal header and 2 SATA ports.
|
||||
|
||||
The D945GCLF2 is an upgraded version of this board. The differences are:
|
||||
1 more USB header, 10/100/1000 ethernet and a dual core cpu (also
|
||||
hyperthreaded). Since the board is almost identical (and coreboot code
|
||||
seem to indicate that it works, since MAX\_CPU=4 is set), it is believed
|
||||
that it should also work but this is untested.
|
||||
|
||||
Remarks about vendor bios:
|
||||
--------------------------
|
||||
|
||||
- Without coreboot/libreboot this board is completely useless, since the
|
||||
vendor bios is very bad. It cannot boot from any HDD whether it is
|
||||
connected to the SATA port or USB. With libreboot it works just
|
||||
fine.
|
||||
|
||||
- The vendor bios write protects the flash so it requires external
|
||||
flashing to install libreboot on this device. Once libreboot is
|
||||
flashed there is no problem to update the firmware internally
|
||||
|
||||
Here is an image of the board:\
|
||||
\
|
||||
Here is an image of the D945GCLF2 board:\
|
||||
{width="80%" height="80%"}\
|
||||
And SPI SOIC8 flash chip\
|
||||
{width="50%" height="50%"}
|
||||
For information about this board, go to
|
||||
[../hardware/d945gclf.md](../hardware/d945gclf.md)
|
||||
|
||||
Flashing instructions {#clip}
|
||||
=====================
|
||||
|
|
@ -102,31 +17,3 @@ Refer to [spi.md](spi.md) for how to re-flash externally.
|
|||
|
||||
Here is an image of the flash chip:\
|
||||
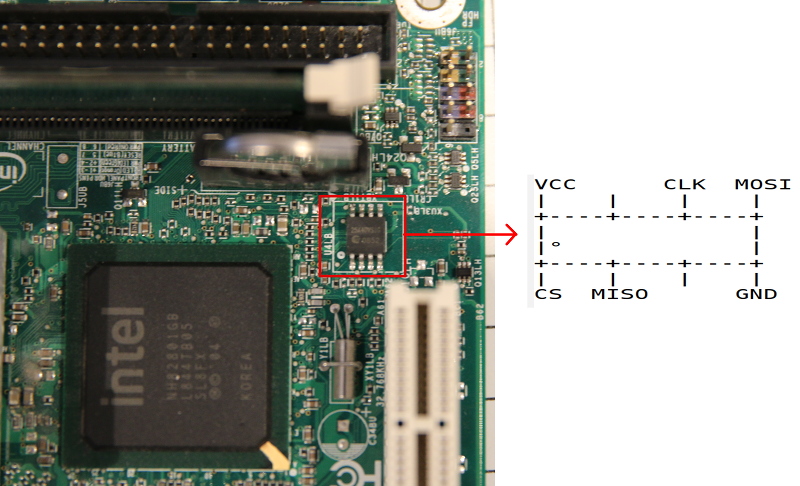
|
||||
|
||||
How to replace thermal paste and fan
|
||||
------------------------------------
|
||||
|
||||
This board comes with very crappy disposable loud fan, that one has no
|
||||
bearings, which can not be repaired or oiled properly, do not waste your
|
||||
time trying to fix it, just buy one chinese same size fan\
|
||||
{width="50%" height="50%"}
|
||||
{width="50%" height="50%"}\
|
||||
Make sure that new one has same wiring\
|
||||
{width="50%" height="50%"}\
|
||||
This is a new one, with bearing and maintenable\
|
||||
{width="50%" height="50%"}
|
||||
{width="50%" height="50%"}\
|
||||
Now remove the both coolers rotating them a bit, slowly, then clean both
|
||||
silicons and both coolers (removing cmos battery first is recommended)\
|
||||
{width="50%" height="50%"}\
|
||||
Put a little bit of non conductive thermal paste on both silicons (only
|
||||
cpu silicon iis shown on that image)\
|
||||
{width="50%" height="50%"}\
|
||||
|
||||
Before assembling new fan, some need new longer screws, make sure having
|
||||
these (on the left is original one, too short for new fan)\
|
||||
{width="50%" height="50%"}\
|
||||
After that, assemble your new fan into CPU cooler\
|
||||
{width="50%" height="50%"}\
|
||||
Finally assemle both coolers on both chips, do not forget put in the CPU
|
||||
fan connector back, and you are done.
|
||||
|
|
|
|||
|
|
@ -1,52 +0,0 @@
|
|||
---
|
||||
title: Dell Latitude thermal throttling
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
On some Dell Latitude laptops, you may encounter random shutdowns on
|
||||
heavy load. We believe this is because the SMSC EC is overly conservative
|
||||
by default; it is in charge of handling thermals and fan control on this
|
||||
machine. Our theory is that coreboot needs to write certain EC commands
|
||||
to allow higher temperatures; please read:
|
||||
|
||||
<https://codeberg.org/libreboot/lbmk/issues/202>
|
||||
|
||||
Basically, what you need to do is:
|
||||
|
||||
* Use high quality thermal paste (don't use the same dried up paste that the
|
||||
laptop came with, if you bought it on ebay for example). Arctic MX-6 is good.
|
||||
* Check that the fan works reliably
|
||||
|
||||
Also: the `intel_pstate` driver can be used to artifically cap CPU speed. See:
|
||||
|
||||
<https://www.kernel.org/doc/html/v4.12/admin-guide/pm/intel_pstate.html>
|
||||
|
||||
When you use this machine, it is recommended that you cap the CPU speed once
|
||||
you've booted into Linux. Set it to something like 50% at first. Then run a
|
||||
stress test, for example:
|
||||
|
||||
stress -c x
|
||||
|
||||
Where `x` is the number of CPU cores, e.g. 2. Monitor the temperatures using
|
||||
something like `xsensors`, making sure the CPU doesn't exceed 80c temperature.
|
||||
|
||||
You can also monitor CPU speeds in Linux like so:
|
||||
|
||||
watch -n .2 grep MHz /proc/cpuinfo
|
||||
|
||||
This will let you know what speed you're at. You can use this to determine
|
||||
whether the `intel_pstate` driver is working. How to cap speed to 50 percent, as
|
||||
in the above example:
|
||||
|
||||
echo 50 > /sys/devices/system/cpu/cpufreq/intel_pstate/max_perf_pct
|
||||
|
||||
Gradually increase the CPU speed (up to 100 on `max_perf_pct`), waiting a few
|
||||
minutes each time. You should ensure that your machine does not exceed 80C.
|
||||
|
||||
Dell's thermal safety is far too protective by default, on some of these, and
|
||||
we don't yet know how to properly configure it. Running a CPU below 80c in
|
||||
temperature and never higher than that, is a good idea anyway, for the
|
||||
long term life of your CPU.
|
||||
|
||||
Regardless, thermal shutdown is extremely reliable on this machine, but Dell
|
||||
makes it shut down *earlier*, before it can even start to CPU throttle.
|
||||
|
|
@ -1,79 +0,0 @@
|
|||
---
|
||||
title: Disabling /dev/mem protections
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
This section applies to any program that makes use of lower memory
|
||||
below 1MB. This applies to `flashprog` and `dell-flash-unlock` plus any other
|
||||
tool that uses lower memory and/or port I/O
|
||||
|
||||
Port I/O is up to you, BUT it is recommended that you re-disable lower memory
|
||||
access once you no longer need it, as this is a useful security layer against
|
||||
any wrongful operations that you may later inadvertently run as root.
|
||||
|
||||
Also disable SecureBoot
|
||||
=======================
|
||||
|
||||
If you're using a UEFI setup, it's probably because you're using
|
||||
a latter Intel platform and want to flash Libreboot internally, from
|
||||
the factory firmware to Libreboot.
|
||||
|
||||
If the factory firmware implements UEFI, and this is how you boot when
|
||||
using the factory firmware, please ensure that *SecureBoot* is disabled,
|
||||
because it will interfere with lower memory accesses if left enabled.
|
||||
|
||||
FLASH ERRORS (and workarounds)
|
||||
=======================
|
||||
|
||||
**NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.**
|
||||
|
||||
This section relates to installing libreboot on supported targets.
|
||||
|
||||
Right out of the gate, some users may experience errors with flashprog when
|
||||
using the internal programmer. They are:
|
||||
|
||||
/dev/mem access error
|
||||
---------------------
|
||||
|
||||
NOTE: if running `flashprog -p internal` for software based flashing, and you
|
||||
get an error related to `/dev/mem` access, you should reboot with
|
||||
`iomem=relaxed` kernel parameter before running flashprog, or use a kernel that
|
||||
has `CONFIG_STRICT_DEVMEM` not enabled.
|
||||
|
||||
On NetBSD and OpenBSD systems, the equivalent to `iomem=relaxed` in this case
|
||||
is `kernel.securelevel=-1`; see [NetBSD securelevel
|
||||
manual](https://wiki.netbsd.org/tutorials/kernel_secure_levels/)
|
||||
and [OpenBSD securelevel manual](https://man.openbsd.org/securelevel).
|
||||
|
||||
ERROR: Could not get I/O privileges
|
||||
------------------------------------
|
||||
|
||||
Error message: `ERROR: Could not get I/O privileges (Function not implemented)`
|
||||
|
||||
If you get this while running `flashprog -p internal -w filename.rom` (or any
|
||||
internal flash operation), note: flashprog heavily uses ioperm/iopl functions
|
||||
to operate the internal flasher, at least on x86 machines.
|
||||
|
||||
See: <https://lwn.net/Articles/804143/>
|
||||
|
||||
Yeah, just enable `CONFIG_X86_IOPL_IOPERM` in your Linux kernel. This is
|
||||
a *build-time* option, so you must re-compile your kernel, or find a build that
|
||||
has this option enabled (IOPL emulation). Many default kernel configurations
|
||||
now disable this option.
|
||||
|
||||
Here's a handy-dandy guide for building a kernel from source:
|
||||
<https://www.cyberciti.biz/tips/compiling-linux-kernel-26.html>
|
||||
|
||||
**BSD users:** On OpenBSD and NetBSD if you get similar errors, note that it
|
||||
should work here, but you need to boot with `kern.securelevel=-1`.
|
||||
See: [NetBSD securelevel manual](https://wiki.netbsd.org/tutorials/kernel_secure_levels/)
|
||||
and [OpenBSD securelevel manpage](https://man.openbsd.org/securelevel).
|
||||
|
||||
Otherwise, if you get such errors, it may just be that you're not root. You
|
||||
must run flashprog as root, at least to use the internal flasher (using external
|
||||
USB flashing dongles doesn't normally require root).
|
||||
|
||||
NOTE: BSD kernels seem to still enable IOPL by default. However, many modern
|
||||
Linux setups disable it by default these days, so it may be in teh future
|
||||
that most users will start needing to compile their own kernels. (go BSD!)
|
||||
|
|
@ -0,0 +1,264 @@
|
|||
---
|
||||
title: Flashing the Dell Latitude E6400
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
Initial flashing instructions for the E6400.
|
||||
|
||||
**ROM images are available in the [Libreboot 20230423
|
||||
release](../../news/libreboot20230423.md), and subsequent releases.**
|
||||
|
||||
**Variants with Nvidia GPUs are NOT supported in Libreboot 20230423
|
||||
or 20230625.**
|
||||
|
||||
**Variants with Nvidia GPUs are supported in Libreboot 20231021 or higher.**
|
||||
|
||||
This guide is for those who want libreboot on their Latitude E6400 while
|
||||
they still have the original Dell BIOS present. This guide can also be
|
||||
followed (adapted) if you brick your E6400, and you want to recover it.
|
||||
|
||||
Variants (nvidia or intel graphics)
|
||||
========
|
||||
|
||||
Dell E6400, E6400 XFR and E6400 ATG are all believed to work. The flashing
|
||||
instructions are identical, on all of them.
|
||||
|
||||
100% Free Software possible (Intel GPU)
|
||||
=========================
|
||||
|
||||
This board can boot entirely *free software* in the flash. The hardware is similar
|
||||
to that of ThinkPad X200, T400 etc where no-ME setup is possible.
|
||||
|
||||
No-microcode setup feasible
|
||||
----------------------------
|
||||
|
||||
The
|
||||
[microcode bugfixes/mitigations added for GM45](../../news/gm45microcode.md)
|
||||
are also applicable to this board, for users who are interested. Read that
|
||||
article for more information.
|
||||
|
||||
Libreboot still recommends that boot with CPU microcode updates, by default,
|
||||
for all the reasons described by Libreboot's [Binary Blobs Reductions
|
||||
Policy](../../news/policy.md) but this board run reasonably well without them.
|
||||
|
||||
A note about GPUs
|
||||
-----------------
|
||||
|
||||
We *confirm that* the Nvidia models are PM45, and therefore will require a VGA
|
||||
ROM for initialisation. This is supported in Libreboot *after* the 20230625
|
||||
release, if you compile from source; the `e6400_4mb` target can work on both
|
||||
variants, but will need the Nvidia VGA ROM inserted to work on Nvidia models.
|
||||
This insertion is handled automatically in newer lbmk revisions, during build
|
||||
time, or you can [insert it on a release rom
|
||||
after 20230625](ivy_has_common.md). - **A Video BIOS Option
|
||||
ROM is used, in this configuration. Libreboot's
|
||||
build system automatically downloads this at build time, or it can handle that
|
||||
for you in the same way if it was scrubbed from a release ROM.**
|
||||
|
||||
Models with Intel graphics are GM45, and fully supported in Libreboot
|
||||
with native initialisation; ROM images are available since Libreboot 20230423.
|
||||
**The Intel video initialisation is libre, implemented with publicly available
|
||||
source code via libgfxinit, from the coreboot project.**
|
||||
|
||||
Flash chip size {#flashchips}
|
||||
===============
|
||||
|
||||
Use this to find out:
|
||||
|
||||
flashprog -p internal
|
||||
|
||||
We believe most/all are 4MB (32Mb) flash sizes, but larger ROM images are
|
||||
provided for people who wish to upgrade.
|
||||
|
||||
MAC address {#macaddress}
|
||||
===========
|
||||
|
||||
The MAC address is part of the ROM image that you're flashing. You can change
|
||||
it at any time, before or after you've flashed Libreboot; you can also change
|
||||
it in the *Dell* BIOS, if you really want to. This is for the onboard gigabit
|
||||
ethernet device.
|
||||
|
||||
Refer to [mac\_address.md](../hardware/mac_address.md).
|
||||
|
||||
It is recommended that you run *nvmutil*. See:
|
||||
|
||||
[nvmutil usage manual](nvmutil.md)
|
||||
|
||||
The `nvmutil` software is specifically designed for changing MAC addresses,
|
||||
and it implements a few more safeguards (e.g. prevents multicast/all-zero
|
||||
MAC addresses) and features (MAC address randomisation, ability to correct or
|
||||
intententionally corrupt(disable) GbE sections if you wish, swap GbE parts,
|
||||
etc). You can *also* run ich9gen, if you wish:
|
||||
|
||||
[ich9gen usage manual](ich9utils.md)
|
||||
|
||||
Intel GPU: libre video initialisation available
|
||||
===============================================
|
||||
|
||||
Libreboot uses coreboot's native `libgfxinit` on this platform, for
|
||||
variants with Intel graphics.
|
||||
|
||||
For Intel GPU variants, Libreboot 20230423 and up have full support. Simply
|
||||
flash a release ROM, if you wish.
|
||||
|
||||
Nvidia GPU: Video BIOS Option ROM required
|
||||
==========================================
|
||||
|
||||
**NOTE: `nouveau` (Linux video driver) is unstable when it was last tested, in
|
||||
this setup. Either specify `nomodeset` kernel option, or use another
|
||||
operating system such as OpenBSD. More information is written on the
|
||||
[E6400 hardware page](../hardware/e6400.md), regarding OS compatibility.**
|
||||
|
||||
This is *unavailable* in Libreboot 20230423 and 20230625, but a future release
|
||||
will contain support for these variants; for now, you must compile Libreboot
|
||||
from Git. It is available in the default `master` branch of lbmk, under
|
||||
build target `e6400_4mb` - either build from source and it gets inserted
|
||||
automatically, or you can [insert it
|
||||
manually](ivy_has_common.md) on future release ROMs past Libreboot 20230625.
|
||||
|
||||
An earlier experimental revision existed in an experimental branch of
|
||||
lbmk, as build target `e6400nvidia_4mb`, but it was decided that since SeaBIOS
|
||||
is the only payload anyway on this board, having just a single build target is
|
||||
more efficient if that can (and it does) support both variants. It was therefore
|
||||
added to the master branch.
|
||||
|
||||
Actual installation is the same as with regular E6400 (Intel GPU) variants.
|
||||
Refer to the [E6400 flashing instructions](../docs/install/e6400.md).
|
||||
|
||||
Problems with Linux video drivers on Nvidia
|
||||
-------------------------------------------
|
||||
|
||||
Technically, there is nothing wrong with Libreboot itself, but the `nouveau`
|
||||
driver hangs/crashes on Nvidia models, after booting Linux with the Nvidia VGA
|
||||
ROM loaded from coreboot.
|
||||
|
||||
Until that is fixed, you must specify `nomodeset` in your Linux kernel boot
|
||||
parameters.
|
||||
|
||||
Refer to [development
|
||||
discussion](https://codeberg.org/libreboot/lbmk/issues/14#issuecomment-907758)
|
||||
for more information - [testers needed!](../maintain/testing.md)
|
||||
|
||||
The *Intel* GPU variant of E6400 is more stable, and works fully, with full
|
||||
acceleration - the Nvidia models can only be run in software, and the BSD
|
||||
systems only have the slow `nv` driver (which is nonetheless stable).
|
||||
|
||||
Nvidia errata
|
||||
-------------
|
||||
|
||||
**BEFORE** you flash it, please know that support for Nvidia variants is
|
||||
a **proof of concept**. Known issues exist. For more information, please
|
||||
read the [E6400 info page](../hardware/e6400.md), [E6400 nvidia news
|
||||
page](../../news/e6400nvidia.md) and the [development discussion via
|
||||
codeberg](https://codeberg.org/libreboot/lbmk/issues/14#issuecomment-907758).
|
||||
|
||||
How to flash internally (no diassembly)
|
||||
=======================================
|
||||
|
||||
Warning for BSD users
|
||||
---------------------
|
||||
|
||||
**NOTE (15 October 2023): The util is now called `dell-flash-unlock`, but it
|
||||
was previously called `e6400-flash-unlock`. Links have been updated.**
|
||||
|
||||
BSD *boots* and works properly on these machines, but take note:
|
||||
|
||||
Nicholas's [dell-flash-unlock](https://browse.libreboot.org/lbmk.git/plain/util/dell-flash-unlock/dell_flash_unlock.c)
|
||||
utility has been ported to OpenBSD, but *other* BSDs are assumed unsupported for
|
||||
now.
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
||||
NOTE: BSD is mentioned above, but the only BSD tested for `dell-flash-unlock`
|
||||
is OpenBSD, as of 15 October 2023.
|
||||
|
||||
Flashing from Linux
|
||||
-------------------
|
||||
|
||||
MAKE SURE you boot with this Linux kernel parameter: `iomem=relaxed` - this
|
||||
disables memory protections, permitting `/dev/mem` access needed by flashprog.
|
||||
The flash is memory mapped and flashprog accesses it via `/dev/mem`.
|
||||
|
||||
You can flash Libreboot directly from the vendor (Dell) BIOS, without taking
|
||||
the machine apart. It can be done entirely from Linux. It will probably also
|
||||
work on BSD systems, but it has only been testing on Linux thus far.
|
||||
|
||||
**NOTE (15 October 2023): The util is now called `dell-flash-unlock`, but it
|
||||
was previously called `e6400-flash-unlock`. Links have been updated.**
|
||||
|
||||
Check `util/dell-flash-unlock` in the `lbmk.git` repository, or in release
|
||||
archives for Libreboot releases from 20230423 onwards.
|
||||
|
||||
Go in there:
|
||||
|
||||
cd util/dell-flash-unlock
|
||||
make
|
||||
|
||||
With this program, you can unlock the flash in such a way where everything
|
||||
is writeable. Information about how to use it is in the `README.md` file which
|
||||
is included in that program's directory, or you can read it online here:
|
||||
|
||||
<https://browse.libreboot.org/lbmk.git/plain/util/dell-flash-unlock/README.md>
|
||||
|
||||
Literally just run that program, and do what it says. You run it once, and shut
|
||||
down, and when you do, the system brings itself back up automatically. Then
|
||||
you run it and flash it unlocked. Then you run it again. The source code is
|
||||
intuitive enough that you can easily get the gist of it; it's writing some EC
|
||||
commands and changing some chipset config bits. The EC on this machine is
|
||||
hooked up to the `GPIO33` signal, sometimes called `HDA_DOCK_EN`, which sets
|
||||
the flash descriptor override thus disabling any flash protection by the IFD.
|
||||
It also bypasses the SMM BIOS lock protection by disabling SMIs, and Dell's
|
||||
BIOS doesn't set any other type of protection either such as writing to
|
||||
Protected Range registers.
|
||||
|
||||
When you flash it, you can use this command:
|
||||
|
||||
flashprog -p internal -w libreboot.rom
|
||||
|
||||
Where `libreboot.rom` is your E6400 ROM. *Make sure* it's the right one.
|
||||
If flashprog complains about multiple flash chips detected, just pick one of
|
||||
them (doesn't matter which one). On *most* Dell machines, the most correct
|
||||
would probably be this option in flashprog: `-c MX25L3205D/MX25L3208D`.
|
||||
|
||||
So:
|
||||
|
||||
flashprog -p internal -w libreboot.rom -c MX25L3205D/MX25L3208D
|
||||
|
||||
When you see flashprog say `VERIFIED` at the end, that means the flash was
|
||||
successful. If you don't see that, or you're unsure, please [contact the
|
||||
Libreboot project via IRC](../../contact.md).
|
||||
|
||||
BACK UP THE FACTORY BIOS
|
||||
========================
|
||||
|
||||
The `-w` option flashes `libreboot.rom`. You may consider *backing up* the
|
||||
original Dell BIOS first, using the -r option:
|
||||
|
||||
flashprog -p internal -r backup.rom -c MX25L3205D/MX25L3208D
|
||||
|
||||
Do this while in a flashable state, after the 2nd run of `dell-flash-unlock`.
|
||||
|
||||
Make sure the `backup.rom` file gets backed up to an external storage media,
|
||||
not the E6400 itself.
|
||||
|
||||
With this method, you can probably flash it within 5 minutes. Again, zero
|
||||
disassembly required!
|
||||
|
||||
How to flash externally
|
||||
=========================
|
||||
|
||||
Refer to [spi.md](spi.md) as a guide for external re-flashing.
|
||||
|
||||
The SPI flash chip shares a voltage rail with the ICH9 southbridge, which is
|
||||
not isolated using a diode. As a result, powering the flash chip externally
|
||||
causes the ICH9 to partially power up and attempt to drive the SPI clock pin
|
||||
low, which can interfere with programmers such as the Raspberry Pi. See
|
||||
[RPi Drive Strength](spi.md#rpi-drive-strength) for a workaround.
|
||||
|
||||
Have a look online for videos showing how to disassemble, if you wish to
|
||||
externally re-flash.
|
||||
|
||||
|
|
@ -0,0 +1,179 @@
|
|||
---
|
||||
title: Flashing the Dell Latitude E6430
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
**NOTE:** This installation guide also pertains to E5520, E6420, E6520, E5530
|
||||
and E6530.
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
This guide is for those who want libreboot on their Latitude E6430 while
|
||||
they still have the original Dell firmware present. This guide can also be
|
||||
followed (adapted) if you brick your E6430, and you want to recover it.
|
||||
|
||||
**The Intel video initialisation is libre, implemented with publicly available
|
||||
source code via libgfxinit, from the coreboot project.**
|
||||
|
||||
Only the intel GPU variants are supported. The Nvidia GPU variants are untested
|
||||
and should be assumed *broken* by default.
|
||||
|
||||
Flash chip size {#flashchips}
|
||||
===============
|
||||
|
||||
Use this to find out:
|
||||
|
||||
flashprog -p internal
|
||||
|
||||
The internal flash size is 12MiB on this board; physically, an 8MiB and 4MiB
|
||||
chip (two chips) but this distinction only matters for external flashing.
|
||||
|
||||
MAC address {#macaddress}
|
||||
===========
|
||||
|
||||
The MAC address is part of the ROM image that you're flashing. You can change
|
||||
it at any time, before or after you've flashed Libreboot; you can also change
|
||||
it in the *Dell* BIOS, if you really want to. This is for the onboard gigabit
|
||||
ethernet device.
|
||||
|
||||
Refer to [mac\_address.md](../hardware/mac_address.md).
|
||||
|
||||
It is recommended that you run *nvmutil*. See:
|
||||
|
||||
[nvmutil usage manual](nvmutil.md) - E5530 users don't need to run this.
|
||||
|
||||
The `nvmutil` software is specifically designed for changing MAC addresses,
|
||||
and it implements a few more safeguards (e.g. prevents multicast/all-zero
|
||||
MAC addresses) and features (MAC address randomisation, ability to correct or
|
||||
intentionally corrupt(disable) GbE sections if you wish, swap GbE parts,
|
||||
etc). - **it is also the only software available for this. Please do not
|
||||
use ich9gen on this board. This is an ivybridge board, not ICH9M.**
|
||||
|
||||
Intel GPU: libre video initialisation available
|
||||
===============================================
|
||||
|
||||
Libreboot uses coreboot's native `libgfxinit` on this platform, for
|
||||
variants with Intel graphics.
|
||||
|
||||
Libreboot releases after 20230625 will support this board, otherwise you can
|
||||
refer to the [build instructions](../build/)
|
||||
|
||||
Nvidia GPU: Video BIOS Option ROM required
|
||||
==========================================
|
||||
|
||||
UNSUPPORTED. DO NOT BUY THE NVIDIA VARIANT.
|
||||
|
||||
Only the Intel GPU variants are supported. It is believed that the Nvidia
|
||||
variants still have Intel GPUs in them, configured via hardware mux, but this
|
||||
has not yet been configured or tested in the coreboot code; you should assume
|
||||
that the Nvidia models do not work.
|
||||
|
||||
How to flash internally (no diassembly)
|
||||
=======================================
|
||||
|
||||
Warning for BSD users
|
||||
---------------------
|
||||
|
||||
**NOTE (15 October 2023): The util is now called `dell-flash-unlock`, but it
|
||||
was previously called `e6400-flash-unlock`. Links have been updated.**
|
||||
|
||||
BSD *boots* and works properly on these machines, but take note:
|
||||
|
||||
Nicholas's [dell-flash-unlock](https://browse.libreboot.org/lbmk.git/plain/util/dell-flash-unlock/dell_flash_unlock.c)
|
||||
utility has been ported to OpenBSD, but *other* BSDs are assumed unsupported for
|
||||
now.
|
||||
|
||||
NOTE: Libreboot standardises on [flashprog](https://flashprog.org/wiki/Flashprog)
|
||||
now, as of 27 January 2024, which is a fork of flashrom.
|
||||
|
||||
NOTE: BSD is mentioned above, but the only BSD tested for `dell-flash-unlock`
|
||||
is OpenBSD, as of 15 October 2023.
|
||||
|
||||
Flashing from Linux
|
||||
-------------------
|
||||
|
||||
MAKE SURE you boot with this Linux kernel parameter: `iomem=relaxed` - this
|
||||
disables memory protections, permitting `/dev/mem` access needed by flashprog.
|
||||
The flash is memory mapped and flashprog accesses it via `/dev/mem`.
|
||||
|
||||
You can flash Libreboot directly from the vendor (Dell) BIOS, without taking
|
||||
the machine apart. It can be done entirely from Linux. It will probably also
|
||||
work on BSD systems, but it has only been testing on Linux thus far.
|
||||
|
||||
**NOTE (15 October 2023): The util is now called `dell-flash-unlock`, but it
|
||||
was previously called `e6400-flash-unlock`. Links have been updated.**
|
||||
|
||||
Check `util/dell-flash-unlock` in the `lbmk.git` repository, or in release
|
||||
archives for Libreboot releases from 20230423 onwards.
|
||||
|
||||
Go in there:
|
||||
|
||||
cd util/dell-flash-unlock
|
||||
make
|
||||
|
||||
With this program, you can unlock the flash in such a way where everything
|
||||
is writeable. Information about how to use it is in the `README.md` file which
|
||||
is included in that program's directory, or you can read it online here:
|
||||
|
||||
<https://browse.libreboot.org/lbmk.git/plain/util/dell-flash-unlock/README.md>
|
||||
|
||||
Literally just run that program, and do what it says. You run it once, shut
|
||||
down, and then power on the machine. Then run it again to confirm that the
|
||||
flash is unlocked. The source code is intuitive enough that you can easily get
|
||||
the gist of it; it's writing some EC commands and changing some chipset config
|
||||
bits. The EC on this machine is hooked up to the `HDA_SDO` signal, also known
|
||||
as the Flash Descriptor Override (FDO), which disables any flash protection by
|
||||
the IFD. When booted with the FDO set, the original Dell firmware disables all
|
||||
other BIOS write protections such as SMM BIOS lock bits.
|
||||
|
||||
*Make sure* to make a backup of the original firmware before proceeding to
|
||||
flash; see the instructions below.
|
||||
|
||||
When you flash it, you can use this command:
|
||||
|
||||
flashprog -p internal -w libreboot.rom
|
||||
|
||||
Where `libreboot.rom` is your E6430 ROM. *Make sure* it's the right one.
|
||||
If flashprog complains about multiple flash chips detected, just pick one of
|
||||
them (doesn't matter which one), with the `-C` flag as directed; just pick one,
|
||||
and if it doesn't work, try the next.
|
||||
|
||||
When you see flashprog say `VERIFIED` at the end, that means the flash was
|
||||
successful. If you don't see that, or you're unsure, please [contact the
|
||||
Libreboot project via IRC](../../contact.md).
|
||||
|
||||
BACK UP THE FACTORY BIOS
|
||||
========================
|
||||
|
||||
The `-w` option flashes `libreboot.rom`. You may consider *backing up* the
|
||||
original Dell BIOS first, using the -r option:
|
||||
|
||||
flashprog -p internal -r backup.rom
|
||||
|
||||
AGAIN: make sure to use `-C` accordingly, if you need to pick a chip (where
|
||||
flashprog has detected multiple chip definitions). Just pick one, any of them
|
||||
will probably work, if not try the next.
|
||||
|
||||
Do this while in a flashable state, after the 2nd run of `dell-flash-unlock`.
|
||||
|
||||
Make sure the `backup.rom` file gets backed up to an external storage media,
|
||||
not the E6430 itself.
|
||||
|
||||
With this method, you can probably flash it within 5 minutes. Again, zero
|
||||
disassembly required!
|
||||
|
||||
How to flash externally
|
||||
=========================
|
||||
|
||||
Refer to [spi.md](spi.md) as a guide for external re-flashing.
|
||||
|
||||
The SPI flash chip shares a voltage rail with the chipset, which is not
|
||||
isolated using a diode. As a result, powering the flash chip externally may
|
||||
cause the QM77 chipset to partially power up and drive the SPI pins, which can
|
||||
interfere with programmers such as the Raspberry Pi. See [RPi Drive
|
||||
Strength](spi.md#rpi-drive-strength) for a workaround.
|
||||
|
||||
Have a look online for videos showing how to disassemble, if you wish to
|
||||
externally re-flash.
|
||||
|
||||
|
|
@ -1,108 +1,10 @@
|
|||
---
|
||||
title: Gigabyte GA-G41M-ES2L desktop board
|
||||
title: GA-G41M-ES2L flashing tutorial
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
GA-G41M-ES2L
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | Gigabyte |
|
||||
| **Name** | GA-G41M-ES2L |
|
||||
| **Released** | 2009 |
|
||||
| **Chipset** | Intel G41 |
|
||||
| **CPU** | Intel Core 2 Extreme/Quad/Duo,
|
||||
Pentium Extreme/D/4 Extreme/4/Celeron |
|
||||
| **Graphics** | Integrated |
|
||||
| **Display** | None. |
|
||||
| **Memory** | Up to 8GB (2x4GB DDR2-800) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **Original boot firmware** | AWARD BIOS |
|
||||
| **Intel ME/AMD PSP** | Present. Can be disabled |
|
||||
| **Flash chip** | 2x8Mbit |
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|----------------|---------------------------------------|
|
||||
| **Internal flashing with original boot firmware** | W+ |
|
||||
| **Display** | - |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | P+ |
|
||||
| **External output** | P+ |
|
||||
| **Display brightness** | - |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-------|
|
||||
| **GRUB** | Slow! |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
This is a desktop board using intel hardware (circa \~2009, ICH7
|
||||
southbridge, similar performance-wise to the ThinkPad X200. It can make
|
||||
for quite a nifty desktop. Powered by libreboot.
|
||||
|
||||
As of Libreboot release 20221214, only SeaBIOS payload is provided in ROMs
|
||||
for this board. According to user reports, they work quite well. GRUB was
|
||||
always buggy on this board, so it was removed from lbmk.
|
||||
|
||||
IDE on the board is untested, but it might be possible to use a SATA HDD
|
||||
using an IDE SATA adapter. The SATA ports do work, but it's IDE emulation. The
|
||||
emulation is slow in DMA mode sia SeaBIOS, so SeaBIOS is configured to use PIO
|
||||
mode on this board. This SeaBIOS configuration does not affect the Linux kernel.
|
||||
|
||||
You need to set a custom MAC address in Linux for the NIC to work.
|
||||
In /etc/network/interfaces on debian-based systems like Debian or
|
||||
Devuan, this would be in the entry for your NIC:\
|
||||
hwaddress ether macaddressgoeshere
|
||||
|
||||
Alternatively:
|
||||
|
||||
cbfstool libreboot.rom extract -n rt8168-macaddress -f rt8168-macaddress
|
||||
|
||||
Modify the MAC address in the file `rt8168-macaddress` and then:
|
||||
|
||||
cbfstool libreboot.rom remove -n rt8168-macaddress
|
||||
cbfstool libreboot.rom add -f rt8168-macaddress -n rt8168-macaddress -t raw
|
||||
|
||||
Now you have a different MAC address hardcoded. In the above example, the ROM
|
||||
image is named `libreboot.rom` for your board. You can find cbfstool
|
||||
under `cbutils/` after running the following command
|
||||
in the build system:
|
||||
|
||||
./mk -d coreboot TREENAME
|
||||
|
||||
You can learn more about using the build system, lbmk, here:\
|
||||
[libreboot build instructions](../build/)
|
||||
|
||||
RAM
|
||||
===
|
||||
|
||||
**This board is very picky with RAM. If it doesn't boot, try an EHCI debug
|
||||
dongle, serial usb adapter and null modem cable, or spkmodem, to get a
|
||||
coreboot log to see if it passed raminit.**
|
||||
|
||||
Kingston 8 GiB Kit KVR800D2N6/8G with Elpida Chips E2108ABSE-8G-E
|
||||
|
||||
this is a 2x4GB setup and these work quite well, according to a user on IRC.
|
||||
|
||||
Nanya NT2GT64U8HD0BY-AD with 2 GiB of NT5TU128M8DE-AD chips works too.
|
||||
|
||||
Many other modules will probably work just fine, but raminit is very picky on
|
||||
this board. Your mileage *will* fluctuate, wildly.
|
||||
This guide is for those who want libreboot on their Intel GA-G41M-ES2L
|
||||
motherboard while they still have the original BIOS present.
|
||||
|
||||
MAC ADDRESS
|
||||
===========
|
||||
|
|
|
|||
|
|
@ -1,61 +0,0 @@
|
|||
---
|
||||
title: HP EliteBook 2570p
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
**[PLEASE READ THESE INSTRUCTIONS BEFORE INSTALLING](../../news/safety.md),
|
||||
OR YOU MIGHT BRICK YOUR MACHINE: [SAFETY PRECAUTIONS](../../news/safety.md)**
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
HP EliteBook 2570p
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|---------------------------|-----------------------------------|
|
||||
| **Manufacturer** | HP |
|
||||
| **Name** | EliteBook 2570p |
|
||||
| **Released** | 2012 |
|
||||
| **Chipset** | Intel QM77 |
|
||||
| **CPU** | Intel Ivy Bridge, socketed |
|
||||
| **Graphics** | Intel HD Graphics |
|
||||
| **Display** | 12.5" 1366x768 |
|
||||
| **Memory** | Up to 16GB (2x8GB) |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | KBC1126, proprietary |
|
||||
| **Intel ME/AMD PSP** | Present, neutered |
|
||||
| **Flash chip** | SOIC-16 16MiB |
|
||||
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
|
||||
Brief board info
|
||||
================
|
||||
|
||||
Vendor info here:
|
||||
|
||||
<https://support.hp.com/us-en/document/c03412731>
|
||||
|
||||
Installation of Libreboot
|
||||
=========================
|
||||
|
||||
Coreboot also has some information:
|
||||
|
||||
<https://doc.coreboot.org/mainboard/hp/2560p.html#programming>
|
||||
|
||||
If you're using *Libreboot release* ROM images, the ME image has been scrubbed
|
||||
and you must re-insert it. Use the information on this guide to know how
|
||||
to do that:
|
||||
|
||||
[Insert vendor files on Intel Sandybridge/Ivybridge/Haswell
|
||||
platforms](../install/ivy_has_common.md)
|
||||
|
||||
Make sure to set the MAC address in the flash:
|
||||
[Modify MAC addresses with nvmutil](../install/nvmutil.md).
|
||||
|
||||
Refer to the [Libreboot flashing guides](../install/spi.md)
|
||||
|
|
@ -1,187 +0,0 @@
|
|||
---
|
||||
title: HP EliteBook 820 G2
|
||||
x-toc-enable: true
|
||||
...
|
||||
|
||||
**[PLEASE READ THESE INSTRUCTIONS BEFORE INSTALLING](../../news/safety.md),
|
||||
OR YOU MIGHT BRICK YOUR MACHINE: [SAFETY PRECAUTIONS](../../news/safety.md)**
|
||||
|
||||
<div class="specs">
|
||||
<center>
|
||||
<img tabindex=1 alt="HP EliteBook 820 G2" class="p" src="https://av.libreboot.org/hp820g2/hp820g2.jpg" /><span class="f"><img src="https://av.libreboot.org/hp820g2/hp820g2.jpg" /></span>
|
||||
<img tabindex=1 alt="HP EliteBook 820 G2" class="p" src="https://av.libreboot.org/hp820g2/hp820g2_lid.jpg" /><span class="f"><img src="https://av.libreboot.org/hp820g2/hp820g2_lid.jpg" /></span>
|
||||
<br/>
|
||||
<img tabindex=1 alt="HP EliteBook 820 G2" class="p" src="https://av.libreboot.org/hp820g2/hp820g2_ports1.jpg" /><span class="f"><img src="https://av.libreboot.org/hp820g2/hp820g2_ports1.jpg" /></span>
|
||||
<img tabindex=1 alt="HP EliteBook 820 G2" class="p" src="https://av.libreboot.org/hp820g2/hp820g2_ports2.jpg" /><span class="f"><img src="https://av.libreboot.org/hp820g2/hp820g2_ports2.jpg" /></span>
|
||||
<br/>
|
||||
</center>
|
||||
|
||||
| ***Specifications*** | |
|
||||
|----------------------------|------------------------------------------------|
|
||||
| **Manufacturer** | HP |
|
||||
| **Name** | EliteBook 820 G2 |
|
||||
| **Variants** | EliteBook 820 G2 |
|
||||
| **Released** | 2014 |
|
||||
| **Chipset** | 5th gen (Broadwell, SoC) |
|
||||
| **CPU** | Intel i5-5200U, i5-5300U, i7-5500U, i7-5600U |
|
||||
| **Graphics** | Intel HD 5500 graphics (libre initialisation) |
|
||||
| **Display** | 14" 1366x768 or 1920x1080 TFT |
|
||||
| **Memory** | Two slots, max 16GB/slot (32GB), DDR3/SODIMM |
|
||||
| **Architecture** | x86_64 |
|
||||
| **EC** | SMSC MEC1324 in main boot flash |
|
||||
| **Original boot firmware** | HP UEFI firmware |
|
||||
| **Intel ME/AMD PSP** | Present. Can be disabled with me_cleaner. |
|
||||
| **Flash chip** | SOIC-8 16MiB 128Mbit, 12MiB usable by coreboot |
|
||||
|
||||
|
||||
```
|
||||
W+: Works without blobs;
|
||||
N: Doesn't work;
|
||||
W*: Works with blobs;
|
||||
U: Untested;
|
||||
P+: Partially works;
|
||||
P*: Partially works with blobs
|
||||
```
|
||||
|
||||
| ***Features*** | |
|
||||
|---------------------------------------------------|----|
|
||||
| **Internal flashing with original boot firmware** | N |
|
||||
| **Display (if Intel GPU)** | W+ |
|
||||
| **Audio** | W+ |
|
||||
| **RAM Init** | W+ |
|
||||
| **External output** | W+ |
|
||||
| **Display brightness** | W+ |
|
||||
|
||||
| ***Payloads supported*** | |
|
||||
|---------------------------|-----------|
|
||||
| **GRUB** | Works |
|
||||
| **SeaBIOS** | Works |
|
||||
| **SeaBIOS with GRUB** | Works |
|
||||
</div>
|
||||
|
||||
Brief board info:
|
||||
|
||||
Full hardware specifications can be found on HP's own website:
|
||||
|
||||
<https://support.hp.com/gb-en/document/c04543492>
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
Please build this from source with lbmk:
|
||||
|
||||
./mk -b coreboot hp820g2_12mb
|
||||
|
||||
More information is available in the [build guide](../build/), including how
|
||||
to install build dependencies. Building from source is required, because there
|
||||
aren't any ROM images for this board, in regular Libreboot releases. The
|
||||
reason is that the vendor inject scripts don't currently work, because coreboot
|
||||
compresses the refcode when inserting it at build time, and the process of
|
||||
compression is not yet reproducible; it's not feasible to do so, and making
|
||||
it not be compressed in flash would not be ideal either, so this is simply
|
||||
a source-only port in Libreboot.
|
||||
|
||||
HP Sure Start
|
||||
=============
|
||||
|
||||
There is a 16MB flash and a 2MB flash. Read this page for info:
|
||||
<https://doc.coreboot.org/mainboard/hp/hp_sure_start.html>
|
||||
|
||||
The page makes it seem more complicated than necessary, from a user's point
|
||||
of view. What you really need to do is just erase the 2MB flash IC, and flash
|
||||
only the first 12MB of the 16MB flash IC. A photo is shown below. Consult
|
||||
the [SPI flashing guide](../install/spi.md) and act as if you were flashing,
|
||||
but leave out `-w libreboot.rom` (don't write an image), and instead
|
||||
use the `--erase` option, with your clip connected to the private flash (2MB
|
||||
flash IC).
|
||||
|
||||
You might want to dump the private flash first, just in case (use `-r priv.rom`
|
||||
or whatever filename you want to dump to, and take two dumps, ensuring that
|
||||
the hashes match); one dump for the first erase, and another for the next
|
||||
erase. If they match, then the erase was likely a success. The private (2MB)
|
||||
flash is inaccessible from your OS. The
|
||||
system stores hashes of the IFD, GbE and a copy of IFD/GbE in private flash,
|
||||
restoring them if they were modified, but erasing the private flash disables
|
||||
this security mechanism.
|
||||
|
||||
Coreboot has its own page about this machine:
|
||||
|
||||
<https://doc.coreboot.org/mainboard/hp/elitebook_820_g2.html>
|
||||
|
||||
Make sure to read and understand all of this first, before attempting
|
||||
the Libreboot installation, because it's also important when updating
|
||||
Libreboot later on.
|
||||
|
||||
Installation of Libreboot
|
||||
=========================
|
||||
|
||||
Make sure to set the MAC address in the flash:
|
||||
[Modify MAC addresses with nvmutil](../install/nvmutil.md).
|
||||
|
||||
Refer to the [Libreboot flashing guides](../install/spi.md)
|
||||
|
||||
Here are the flash ICs:
|
||||
|
||||

|
||||
|
||||
When you flash the 12MB image, please do the following with it:
|
||||
|
||||
dd if=/dev/zero of=4mb.bin bs=4M count=1
|
||||
cat libreboot.rom 4mb.bin > libreboot16.rom
|
||||
|
||||
Be careful: do not fully flash `libreboot16.rom`
|
||||
|
||||
Flash it like this, instead:
|
||||
|
||||
```
|
||||
flashprog -p PROGRAMMER --ifd -i gbe -w libreboot16.rom --noverify-all
|
||||
flashprog -p PROGRAMMER --ifd -i bios -w libreboot16.rom --noverify-all
|
||||
flashprog -p PROGRAMMER --ifd -i me -w libreboot16.rom --noverify-all
|
||||
flashprog -p PROGRAMMER --ifd -i ifd -w libreboot16.rom --noverify-all
|
||||
```
|
||||
|
||||
Replace `PROGRAMMER` according to whichever flasher you're using. You could
|
||||
also replace it with `internal`, if later flashing internally to update an
|
||||
existing Libreboot installation.
|
||||
|
||||
If you're flashing internally, add `--noverify-all` to the flashprog
|
||||
command.
|
||||
|
||||
To erase the 2MB flash, do this:
|
||||
|
||||
```
|
||||
flashprog -p PROGRAMMER --erase
|
||||
```
|
||||
|
||||
Refer generally to the [main flashing guide](../install/) and to
|
||||
the [external flashing guide](../install/spi.md) so that you can learn how
|
||||
to actually flash it.
|
||||
|
||||
TPM 2.0 potentially supported
|
||||
==============================
|
||||
|
||||
The onboard TPM is an SLB 9660, which supports TPM 1.2 but it is known to be
|
||||
compatible with TPM 2.0 via firmware upgrade. Although not yet tested, we have
|
||||
some notes about that here:
|
||||
|
||||
[../../tasks/#hp-820-g2-tpm](../../tasks/#hp-820-g2-tpm)
|
||||
|
||||
Not yet used meaningfully by Libreboot itself, but the TPM can be used to
|
||||
implement things like measured boot.
|
||||
|
||||
References
|
||||
==========
|
||||
|
||||
See: <https://doc.coreboot.org/soc/intel/broadwell/blobs.html>
|
||||
|
||||
Libreboot's build system automatically pulls down the MRC/refcode files, and
|
||||
modifies the refcode to enable the onboard Intel Gigabit Ethernet (GbE). You
|
||||
don't need to mess with this at all, when you build Libreboot yourself.
|
||||
|
||||
You can see how this works, by looking at the patch which added 820 G2 support:
|
||||
<https://browse.libreboot.org/lbmk.git/commit/?id=401c0882aaec059eab62b5ce467d3efbc1472d1f>
|
||||
|
||||

|
||||
|
||||
Yay. If you see this boot screen, you should be proud. This is a really
|
||||
hard machine to flash.
|
||||
|
|
@ -196,7 +196,10 @@ Read on for more information. Use the `ro` files mentioned below, and your
|
|||
flash will be read-only in software (you can still externally re-flash and read
|
||||
the contents of flash).
|
||||
|
||||
For ease of use, libreboot provides ROMs that are read-write by default.
|
||||
For ease of use, libreboot provides ROMs that are read-write by default. In
|
||||
practise, you can boot a Linux kernel with access to lower memory disabled
|
||||
which will make software re-flashing impossible (unless you reboot with such
|
||||
memory protections disabled, e.g. `iomem=relaxed` kernel parameter).
|
||||
|
||||
ICH9 deblob utility {#ich9deblob}
|
||||
===================
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load Diff
|
|
@ -3,29 +3,76 @@ title: Insert vendor files on Sandybridge/Ivybridge/Haswell
|
|||
x-toc-enable: true
|
||||
...
|
||||
|
||||
Please make sure to install [build dependencies](../build/) if following this
|
||||
guide, and note that this guide assumes you use [lbmk.git](../git.md), not the
|
||||
release archives, even if you're using release *ROM images*, which is fine.
|
||||
**NOTE: This page also applies to PM45 machine Dell Latitude E6400 if it
|
||||
contains an Nvidia GPU (Libreboot vendor scripts can insert the VGA ROM)**
|
||||
|
||||
This is not a general purpose installation guide, but you *should read it*
|
||||
before installing Libreboot! *This* guide *must* be followed, no matter what
|
||||
method you use to install Libreboot; even if you compile from source, you should
|
||||
still read this page for later reference.
|
||||
|
||||
For how to use an external programmer see the [25xx NOR flashing guide](/docs/install/spi.html)
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
**PLEASE MAKE SURE you have build dependencies installed first. Although you
|
||||
do not need to re-compile release ROMs, you should follow these instructions
|
||||
before reading the instructions below:
|
||||
<https://libreboot.org/docs/build/#first-install-build-dependencies>**
|
||||
|
||||
Coreboot is nominally free software, but requires certain vendor code on some
|
||||
boards, for certain functionalities; we cover this more thoroughly in
|
||||
the [Freedom Status](../../freedom-status.md) page and in the [Binary Blob
|
||||
Reduction Policy](../../news/policy.md).
|
||||
|
||||
Therefore, you should just follow this guide if in any doubt. Otherwise, the
|
||||
freedom status page lists all boards that require vendor files, and it says
|
||||
what they are. This is because Libreboot cannot directly distribute some of them,
|
||||
but they are extracted from vendor updates at build time, and inserted into
|
||||
images; when those images are then archived for release, the non-redistributable
|
||||
filejs are removed.
|
||||
Well, not all of these files are freely redistributable. Coreboot does provide
|
||||
vendor files in some cases, if the vendor has allowed it. In other cases,
|
||||
extraction from factory firmware is required, or you can extract them from
|
||||
vendor-supplied updates - Libreboot's build system does the latter.
|
||||
|
||||
The same logic can be used after the fact, to re-download and re-insert these
|
||||
files; the page that you're reading now will tell you how to do so.
|
||||
When you [compile Libreboot ROM images from source](../build/), Libreboot will
|
||||
automatically download any given files that are required, for any given board
|
||||
target. This is done without user intervention, and only when absolutely needed
|
||||
to make the machine boot properly.
|
||||
|
||||
*If in doubt, just follow these instructions anyway; if your board doesn't need
|
||||
vendor files inserted, nothing will happen. You only need to follow this guide
|
||||
if you use release ROMs; if you're building directly from source, using the
|
||||
Libreboot build system, then you can just flash the result.*
|
||||
The problem?
|
||||
------------
|
||||
|
||||
Well, if the files cannot be freely redistributed, then we can't provide them.
|
||||
So how do we handle *that*, in the context of Libreboot releases?
|
||||
|
||||
The solution
|
||||
------------
|
||||
|
||||
The answer is very simple: these files are **NOT** provided, at all! However,
|
||||
the very same logic used by the build system can be run standalone, to re-insert
|
||||
these vendor files on release ROMs. The `inject` script detects what files are
|
||||
needed for your ROM image.
|
||||
|
||||
The script will detect what board you're inserting on, or you can manually tell
|
||||
it what board, and it will fetch them for you, inserting them, so that your
|
||||
board is ready to flash - flashing it without these required files may result in
|
||||
a brick.
|
||||
|
||||
Vendor file locations
|
||||
--------------
|
||||
|
||||
During auto-download of files, they are saved to these locations within the
|
||||
Libreboot build system:
|
||||
|
||||
* ME firmware: `vendor/*/me.bin` - the `*` can be any given directory. Different ones will
|
||||
be used by given boards, but the directory name may not match the board
|
||||
target name.
|
||||
* SMSC SCH5545 fan control firmware (for Dell T1650): `vendor/t1650/sch5545ec.bin`
|
||||
* SMSC KBC1126 embedded controller firmware, on HP EliteBooks: `ec/`
|
||||
* Intel MRC firmware, used for ram/peripheral init on Haswell machines such as
|
||||
thinkpad t440p/w541: `mrc/`
|
||||
|
||||
The above list refers to the *non-redistributable files*, and these are not
|
||||
directly included in releases. These are auto-downloaded during the build.
|
||||
The `me.bin` files are produced by extracting them from vendor updates and
|
||||
neutering them with `me_cleaner` so that Intel ME is disabled during early boot.
|
||||
|
||||
Injecting vendor files into ROM
|
||||
------------------------------------
|
||||
|
|
@ -33,19 +80,18 @@ Injecting vendor files into ROM
|
|||
You must determine the correct board name, for your board, based on the list
|
||||
generated when running this command:
|
||||
|
||||
./mk -b coreboot list
|
||||
./build roms list
|
||||
|
||||
For example, `t440pmrc_12mb` corresponds to ThinkPad T440p with MRC firmware.
|
||||
Whereas `t440plibremrc_12mb` corresponds to T440p with libre MRC firmware.
|
||||
Another example: `x230_12mb` corresponds to Thinkpad X230.
|
||||
|
||||
In order to inject the necessary files into a rom image, run the script from the root of lbmk and point to the rom image.
|
||||
|
||||
If you only wish to flash a release rom then the process of injecting the necessary files is quite simple.
|
||||
Run the injection script pointing to the release archive you downloaded:
|
||||
|
||||
./vendor inject libreboot-RELEASE_targetname.tar.xz
|
||||
|
||||
**You are strongly advised only to insert it on the tarball, because then
|
||||
checksums are verified to ensure that the vendor files were inserted correctly.
|
||||
Otherwise, you can do it manually on each individual image, specifying the
|
||||
board name with the instructions provided below:**
|
||||
./vendor inject /path/to/libreboot-20230319-18-g9f76c92_t440pmrc_12mb.tar.xz
|
||||
|
||||
The script can automatically detect the board as long as you do not change the file name.
|
||||
You can then find flash-ready ROMs in `/bin/release/`
|
||||
|
|
@ -64,32 +110,24 @@ For example:
|
|||
Check that the files were inserted
|
||||
==================================
|
||||
|
||||
You *must* ensure that the files were inserted. The inject command automatically
|
||||
verifies checksums of the complete images, when you run it directly on a
|
||||
release tarball, but not when running it manually on an individual image;
|
||||
checking it manually is useful for the latter, but you should probably just
|
||||
insert it into the tarball.
|
||||
You *must* ensure that the files were inserted.
|
||||
|
||||
Some examples of how to do that in lbmk:
|
||||
|
||||
./mk -d coreboot TREENAME
|
||||
./update trees -b coreboot utils
|
||||
|
||||
TREENAME should be the coreboot tree corresponding to your board. Check
|
||||
this in `config/coreboot/BOARD/target.cfg` for your board, and `tree` will be
|
||||
set to e.g. `default`, or some other tree name.
|
||||
|
||||
Now you find `elf/cbfstool`, which is a directory containing `cbfstool`
|
||||
Now you find `cbutitls/default`, which is a directory containing `cbfstool`
|
||||
and `ifdtool`. Do this on your ROM image (`libreboot.rom` in the example
|
||||
below):
|
||||
|
||||
./elf/cbfstool/TREENAME/cbfstool libreboot.rom print
|
||||
./cbutils/default/cbfstool libreboot.rom print
|
||||
|
||||
You should check that the files were inserted in cbfs, if needed; for example,
|
||||
EC firmware or MRC firmware.
|
||||
|
||||
Next:
|
||||
|
||||
./elf/ifdtool/TREENAME/ifdtool -x libreboot.rom
|
||||
./cbutils/default/ifdtool -x libreboot.rom
|
||||
|
||||
This creates several `.bin` files, one of which says `me` in it (Intel ME).
|
||||
Run hexdump on it:
|
||||
|
|
@ -103,31 +141,14 @@ You'll note the small size of the Intel ME, e.g. 84KB on sandybridge platforms.
|
|||
This is because lbmk *automatically* neuters it, disabling it during
|
||||
early boot. This is done using `me_cleaner`, which lbmk imports.
|
||||
|
||||
NOTE: the MAC changer makes use of `nvmutil`, which you can read more about in
|
||||
the [nvmutil documentation](nvmutil.md).
|
||||
|
||||
Errata
|
||||
======
|
||||
|
||||
NOTE: As of Libreboot releases from May 2024 onward, the Intel MRC is no longer
|
||||
included for Haswell; MRC is a blob for raminit, but we now provide libre
|
||||
raminit. The following targets no longer exist in the build system:
|
||||
|
||||
* `t440pmrc_12mb` (use `t440plibremrc_12mb` instead)
|
||||
* `t440pbmrc_12mb` (use `t440plibremrc_12mb` instead)
|
||||
* `w541mrc_12mb` (use `w541_12mb` instead)
|
||||
* `w541bmrc_12mb` (use `w541_12mb` instead)
|
||||
* `dell9020sff_12mb` (use `dell9020sff_nri_12mb` instead)
|
||||
* `dell9020sffbmrc` (use `dell9020sff_nri_12mb` instead)
|
||||
* `dell9020mt_12mb` (use `dell9020mt_nri_12mb` instead)
|
||||
* `dell9020mtbmrc` (use `dell9020mt_nri_12mb` instead)
|
||||
|
||||
This is written as errata because some users may still be using older release
|
||||
images but on the newer build system from May 2024 onward; you must use the
|
||||
Libreboot 20240225 release if you want to inject MRC and so on, for these older
|
||||
targets.
|
||||
|
||||
Libreboot's [binary blob reduction policy](../../news/policy.md) is very strict,
|
||||
and states: if a blob can be avoided, it must be avoided. Therefore, the MRC
|
||||
is removed on Haswell and Libreboot will only use the libre raminit (called
|
||||
NRI, short for Native Ram Initialisation).
|
||||
**NOTE: Haswell machines come with `mrc.bin` or without, depending on the
|
||||
ROM image configuration. These ROM configs have `mrc.bin`: `t440pmrc_12mb`
|
||||
and `w541mrc_12mb`. These ROM configs have libre MRC: `t440p_12mb`
|
||||
and `w541_12mb` - it is critical that you choose the right one, when using
|
||||
the `-b` flag in the `./vendor inject` command. For example, if you
|
||||
used `-b t440p_12mb` on a ROM image that actually corresponds
|
||||
to `t440pmrc_12mb`, then the required `mrc.bin` file would not be added
|
||||
and that ROM would not boot when flashed.**
|
||||
|
|
|
|||
|
|
@ -3,9 +3,6 @@ title: Insert vendore files on Sandybridge/Ivybridge/Haswell
|
|||
x-toc-enable: true
|
||||
...
|
||||
|
||||
Regarding vendorfile insertion: if unsure, just follow these instructions.
|
||||
If a given target does not require vendor files, none will be inserted.
|
||||
|
||||
**TODO: Re-translate this again to Ukrainian. It was translated before, but
|
||||
the english page got heavily re-written.**
|
||||
|
||||
|
|
@ -71,10 +68,10 @@ Libreboot build system:
|
|||
* ME firmware: `vendor/*/me.bin` - the `*` can be any given directory. Different ones will
|
||||
be used by given boards, but the directory name may not match the board
|
||||
target name.
|
||||
* SMSC SCH5545 fan control firmware (for Dell T1650): `vendor/t1650/sch5545ec.bin` -
|
||||
ditto 7010/9010 MT/SFF optiplex machines.
|
||||
* SMSC SCH5545 fan control firmware (for Dell T1650): `vendor/t1650/sch5545ec.bin`
|
||||
* SMSC KBC1126 embedded controller firmware, on HP EliteBooks: `ec/`
|
||||
* Intel MRC firmware, provides raminit on HP EliteBook 820 G2
|
||||
* Intel MRC firmware, used for ram/peripheral init on Haswell machines such as
|
||||
thinkpad t440p/w541: `mrc/`
|
||||
|
||||
The above list refers to the *non-redistributable files*, and these are not
|
||||
directly included in releases. These are auto-downloaded during the build.
|
||||
|
|
@ -87,7 +84,11 @@ Inject vendor files into ROM
|
|||
You must determine the correct board name, for your board, based on the list
|
||||
generated when running this command:
|
||||
|
||||
./mk -b coreboot list
|
||||
./build roms list
|
||||
|
||||
For example, `t440pmrc_12mb` corresponds to ThinkPad T440p with MRC firmware.
|
||||
Whereas `t440plibremrc_12mb` corresponds to T440p with libre MRC firmware.
|
||||
Another example: `x230_12mb` corresponds to Thinkpad X230.
|
||||
|
||||
In order to inject the necessary files into a rom image, run the script from the root of lbmk and point to the rom image.
|
||||
|
||||
|
|
@ -117,7 +118,7 @@ You *must* ensure that the files were inserted.
|
|||
|
||||
Some examples of how to do that in lbmk:
|
||||
|
||||
./update trees -d coreboot TREENAME
|
||||
./update trees -b coreboot utils
|
||||
|
||||
Now you find `cbutitls/default`, which is a directory containing `cbfstool`
|
||||
and `ifdtool`. Do this on your ROM image (`libreboot.rom` in the example
|
||||
|
|
@ -144,31 +145,17 @@ You'll note the small size of the Intel ME, e.g. 84KB on sandybridge platforms.
|
|||
This is because lbmk *automatically* neuters it, disabling it during
|
||||
early boot. This is done using `me_cleaner`, which lbmk imports.
|
||||
|
||||
NOTE: the MAC changer makes use of `nvmutil`, which you can read more about in
|
||||
the [nvmutil documentation](nvmutil.md).
|
||||
|
||||
Errata
|
||||
======
|
||||
|
||||
NOTE: As of Libreboot releases from May 2024 onward, the Intel MRC is no longer
|
||||
included for Haswell; MRC is a blob for raminit, but we now provide libre
|
||||
raminit. The following targets no longer exist in the build system:
|
||||
**NOTE: Haswell machines come with `mrc.bin` or without, depending on the
|
||||
ROM image configuration. These ROM configs have `mrc.bin`: `t440pmrc_12mb`
|
||||
and `w541mrc_12mb`. These ROM configs have libre MRC: `t440p_12mb`
|
||||
and `w541_12mb` - it is critical that you choose the right one, when using
|
||||
the `-b` flag in the `./vendor inject` command. For example, if you
|
||||
used `-b t440p_12mb` on a ROM image that actually corresponds
|
||||
to `t440pmrc_12mb`, then the required `mrc.bin` file would not be added
|
||||
and that ROM would not boot when flashed.**
|
||||
|
||||
* `t440pmrc_12mb` (use `t440plibremrc_12mb` instead)
|
||||
* `t440pbmrc_12mb` (use `t440plibremrc_12mb` instead)
|
||||
* `w541mrc_12mb` (use `w541_12mb` instead)
|
||||
* `w541bmrc_12mb` (use `w541_12mb` instead)
|
||||
* `dell9020sff_12mb` (use `dell9020sff_nri_12mb` instead)
|
||||
* `dell9020sffbmrc` (use `dell9020sff_nri_12mb` instead)
|
||||
* `dell9020mt_12mb` (use `dell9020mt_nri_12mb` instead)
|
||||
* `dell9020mtbmrc` (use `dell9020mt_nri_12mb` instead)
|
||||
|
||||
This is written as errata because some users may still be using older release
|
||||
images but on the newer build system from May 2024 onward; you must use the
|
||||
Libreboot 20240225 release if you want to inject MRC and so on, for these older
|
||||
targets.
|
||||
|
||||
Libreboot's [binary blob reduction policy](../../news/policy.md) is very strict,
|
||||
and states: if a blob can be avoided, it must be avoided. Therefore, the MRC
|
||||
is removed on Haswell and Libreboot will only use the libre raminit (called
|
||||
NRI, short for Native Ram Initialisation).
|
||||
NOTE: the MAC changer makes use of `nvmutil`, which you can read more about in
|
||||
the [nvmutil documentation](nvmutil.md).
|
||||
|
|
|
|||
|
|
@ -6,37 +6,6 @@ x-toc-enable: true
|
|||
**[PLEASE READ THESE INSTRUCTIONS BEFORE INSTALLING](../../news/safety.md),
|
||||
OR YOU MIGHT BRICK YOUR MACHINE: [SAFETY PRECAUTIONS](../../news/safety.md)**
|
||||
|
||||
Ch1p's guide
|
||||
============
|
||||
|
||||
This page tells you how to flash an ivybridge ThinkPad with Libreboot,
|
||||
internally, when it has the Lenovo firmware on it. It was written independently
|
||||
of ch1p's original guide, the existence of which was later made clear to the
|
||||
Libreboot project, by ch1p himself.
|
||||
|
||||
See: <https://github.com/gch1p/thinkpad-bios-software-flashing-guide>
|
||||
|
||||
Ch1p's own guide also tells you how to do exactly the same thing (same result)
|
||||
as this guide, but this guide (from the Libreboot project) was made
|
||||
independently, without knowing that ch1p's guide existed at the time. Ch1p,
|
||||
aka Evgeny Zinoviev, is the author of the ME Soft Temporary Disable support
|
||||
patch in coreboot, that the guide below makes use of. Specifically, this
|
||||
coreboot patch:
|
||||
|
||||
```
|
||||
commit 833e9bad4762e0dca6c867d3a18dbaf6d5166be8
|
||||
Author: Evgeny Zinoviev <me@ch1p.io>
|
||||
Date: Thu Nov 21 21:47:31 2019 +0300
|
||||
|
||||
sb/intel/bd82x6x: Support ME Soft Temporary Disable Mode
|
||||
```
|
||||
|
||||
Anyway, follow ch1p's guide or this one. Ch1p was on Libreboot IRC and linked
|
||||
the above guide, so it has been added here to honour him.
|
||||
|
||||
Introduction
|
||||
============
|
||||
|
||||
External flashing still recommended
|
||||
-----------------------------------
|
||||
|
||||
|
|
|
|||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue