

| ***Specifications*** | |
|----------------------------|------------------------------------------------|
| **Manufacturer** | Dell |
| **Name** | OptiPlex 3050 Micro |
| **Variants** | OptiPlex 3050 Micro |
| **Released** | 2017 |
| **Chipset** | Intel Kaby Lake |
| **CPU** | Intel Kaby Lake |
| **Graphics** | Intel HD graphics |
| **Memory** | DDR4 SODIMMs (max 32GB, 2x16GB) |
| **Architecture** | x86\_64 |
| **Original boot firmware** | Dell UEFI firmware |
| **Intel ME/AMD PSP** | Present. Can be disabled with me\_cleaner. |
| **Flash chip** | SOIC-8 16MiB (128Mbit) |
```
W+: Works without blobs;
N: Doesn't work;
W*: Works with blobs;
U: Untested;
P+: Partially works;
P*: Partially works with blobs
?: UNKNOWN AT THIS TIME
```
| ***Features*** | |
|---------------------------------------------------|----|
| **Internal flashing with original boot firmware** | W* |
| **Display (if Intel GPU)** | W+ |
| **Audio** | W+ |
| **RAM Init** | W* |
| ***Payloads supported*** | |
|----------------------------|-----------|
| **GRUB (libgfxinit only)** | Works |
| **SeaBIOS** | Works |
Buy pre-installed
=================
**Dell OptiPlex 3050 Micro is available to purchase with Libreboot preinstalled.
See: 



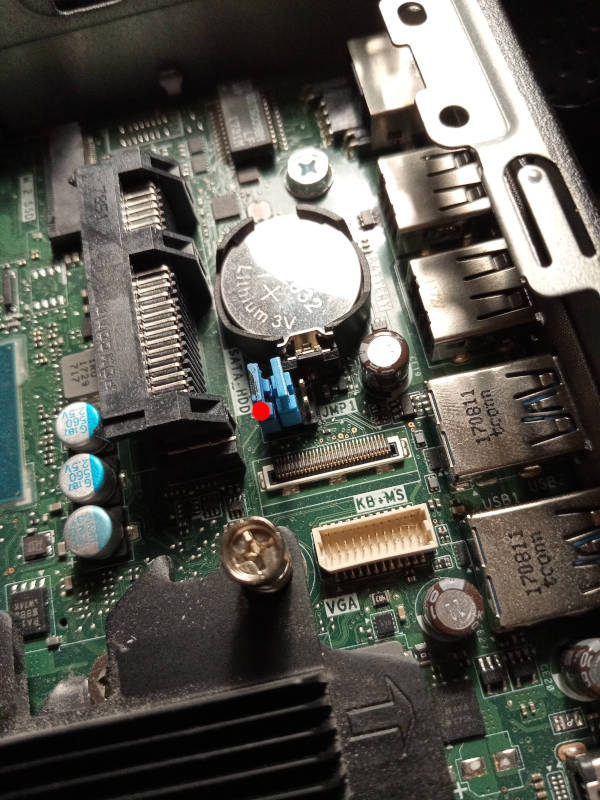
 If you have factory firmware (Dell), you can short the service jumper. It's
near the RAM, under where the HDD goes (click the photos shown above).
Just put a short on it when booting,
and all flash protection is disabled; the factory firmware write might EFI
variables to flash during shutdown sequence, so you should *pull the plug* to
shut it down (remove the power by pulling the plug) after flashprog
says `VERIFIED`.
Flash a ROM image (hardware)
-----------------
For general information, please refer to [25xx NOR flash
instructions](../install/spi.md) - that page refers to use of socketed flash.
The side cover comes off easily, and you can find the flash ICs next to the RAM.
Simply remove the screw at the back. The top panel then slides forward, and you
can remove the SSD caddy; from then on, the flash is accossible.
Observe the following photo of the flash (SOIC-8):
If you have factory firmware (Dell), you can short the service jumper. It's
near the RAM, under where the HDD goes (click the photos shown above).
Just put a short on it when booting,
and all flash protection is disabled; the factory firmware write might EFI
variables to flash during shutdown sequence, so you should *pull the plug* to
shut it down (remove the power by pulling the plug) after flashprog
says `VERIFIED`.
Flash a ROM image (hardware)
-----------------
For general information, please refer to [25xx NOR flash
instructions](../install/spi.md) - that page refers to use of socketed flash.
The side cover comes off easily, and you can find the flash ICs next to the RAM.
Simply remove the screw at the back. The top panel then slides forward, and you
can remove the SSD caddy; from then on, the flash is accossible.
Observe the following photo of the flash (SOIC-8):
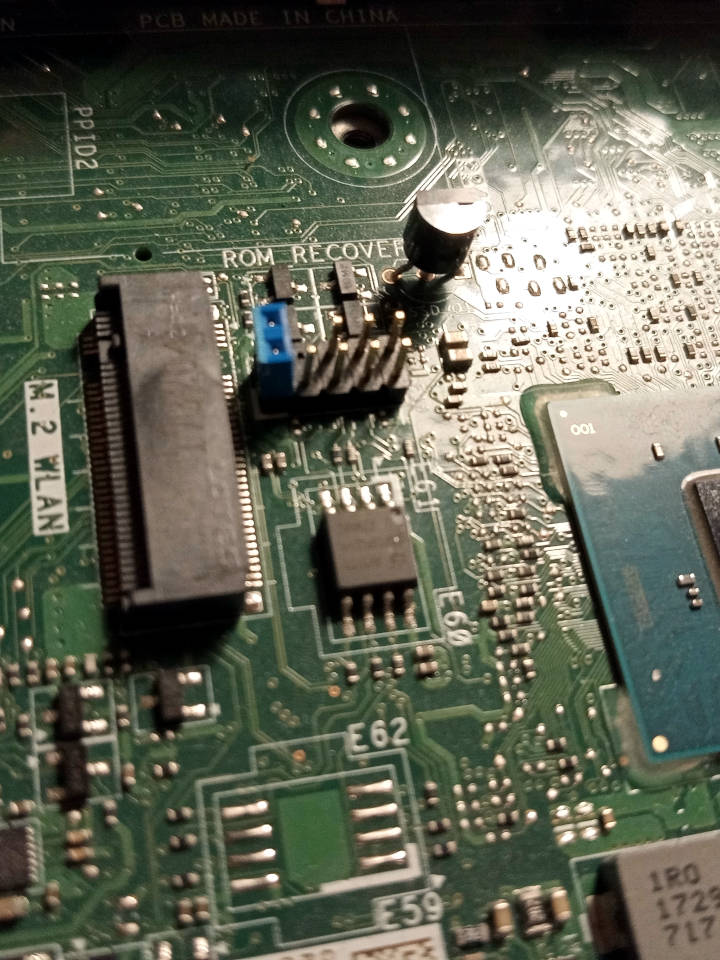
 You can otherwise flash internally, including from factory firmware(if the
service jumper is set).
Errata
======
Power-on after power failure
----------------------------
Older Libreboot revisions made this machine always turn on, when plugging in
a power supply (charger brick), if a previous power loss was observed. This is
because coreboot sets a special register in the PMC that configures such
behaviour, but it was hardcoded to always-on. This is undesirable for most
people, so Libreboot 20241206 *revision 8* and newer releases contain the
following modification:
You can otherwise flash internally, including from factory firmware(if the
service jumper is set).
Errata
======
Power-on after power failure
----------------------------
Older Libreboot revisions made this machine always turn on, when plugging in
a power supply (charger brick), if a previous power loss was observed. This is
because coreboot sets a special register in the PMC that configures such
behaviour, but it was hardcoded to always-on. This is undesirable for most
people, so Libreboot 20241206 *revision 8* and newer releases contain the
following modification: